Finding out what is doing a port
Quickly run:
curl localhost:9001Reverse SSH tunnelling theory
Info
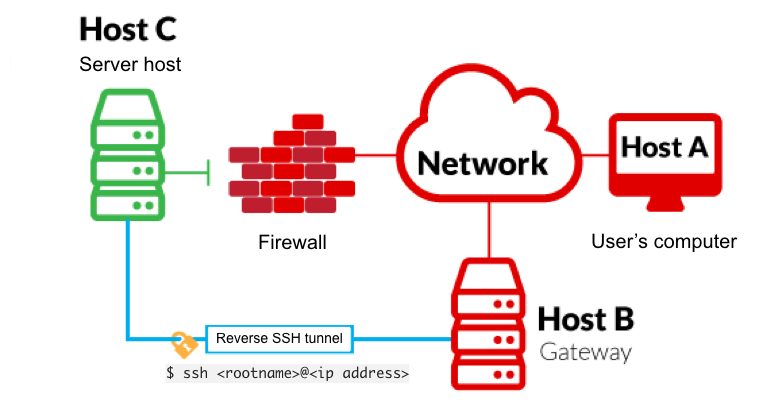
Reverse SSH port forwarding specifies that the given port on the remote server host is to be forwarded to the given host and port on the local side.
Note
-Lis a local tunnel (YOU ⇐ CLIENT). If a site was blocked, you can forward the traffic to a server you own and view it. For example, ifimgurwas blocked at work, you can dossh -L 9000:imgur.com:80 user@example.comGoing tolocalhost:9000on your machine, will loadimgurtraffic using your other server.
-R is a remote tunnel (YOU ⇒ CLIENT). You forward your traffic to the other server for others to view. Similar to the example above, but in reverse.
We will use a tool called ss to investigate sockets running on a host.
If we run ss -tulpn it will tell us what socket connections are running
| Argument | Description |
|---|---|
-t | Display TCP sockets |
-u | Display UDP sockets |
-l | Displays only listening sockets |
-p | Shows the process using the socket |
-n | Doesn’t resolve service names |
To expose a service running on a blocked port by a firewall rule to the outside, we can expose the port to us (locally). Run the following on your machine:
ssh -L YOUR_MACHINE_PORT:localhost:VICTIMS_MACHINE_PORT USERNAME@IP_ATTACKPerforming a reverse SSH tunneling
When you find a port that is only opened in localhost like:
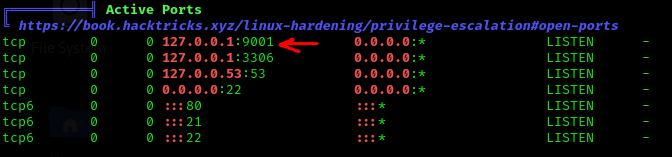
you can drop a SSH key on the server and use SSH to do a reverse tunneling of the port you want to access back on our machine:
# Generate the ssh key
ssh-keygen -f USERNAME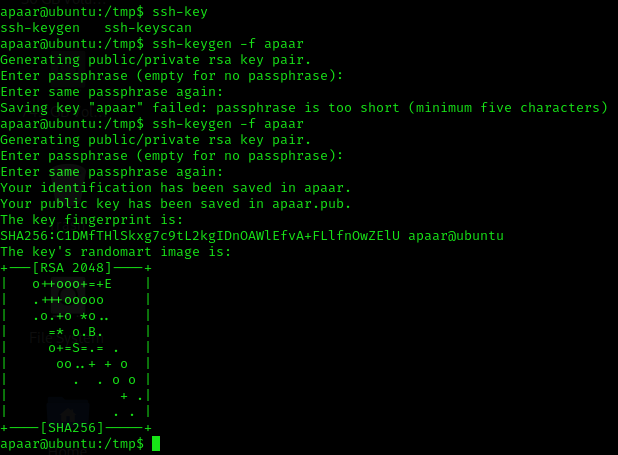
Now copy the USERNAME.pub key into the USERNAME .ssh folder:
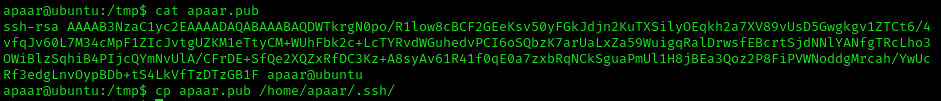
cp USERNAME.pub /home/USERNAME/.ssh/authored_keysGive to the SSH private key the necessary permissions and use the argument -L to perform a reverse port forwarding of the local port to your local box port:
chmod 400 USERNAME
ssh -L YOUR_MACHINE_PORT:localhost:VICTIMS_MACHINE_PORT -i USERNAME USERNAME@IP_ATTACKUsing Chisel
- Check the note Chisel 🦦
