How to understand the /etc/passwd file in Linux
The /etc/passwd file stores vital information (described below) about users such as username, home directory, etc.
Since this file contains vital information for all users, it has reading permissions and it is not necessary to have privileges to see it.
You can read the /etc/passwd file by using the less command followed by the path as shown below.
less /etc/passwd
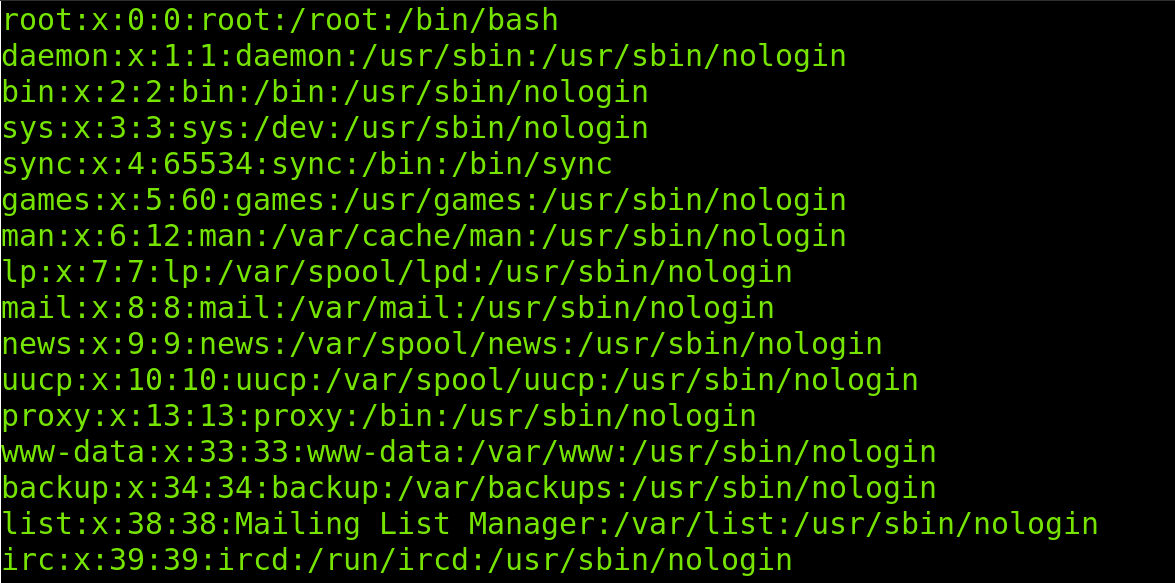 Let’s take the first two lines to explain the structure of the /etc/passwd file in the following table:
Let’s take the first two lines to explain the structure of the /etc/passwd file in the following table:
| root | x | 0 | 0 | root | /root | /bin/bash |
|---|---|---|---|---|---|---|
| daemon | x | 1 | 1 | daemon | /usr/bin | /usr/sbin/nologin |
| USER | AUTH | UID | GID | GECOS | HOME | SHELL |
The first two rows contain the same data shown in the first two lines of the /etc/passwd in the image above. It is important to note that each item is separated by two dots; you can consider the two dots as columns.
The meaning of each column is:
- USER: The first field shows the username.
- AUTHENTICATION: The second field shows the password status, if an x, the password is stored in the /etc/shadow file, if an
- UID: The third field shows the user ID.
- GID: The fourth field shows the group ID.
- GECOS: This field stores user information such as full name, phone number, and email.
- HOME: This field contains the path to the home directory.
- SHELL: Finally, the last field shows the shell for the user.
The x in the second field indicates the password is encrypted and stored in the /etc/shadow file. This file is protected by permissions and can only be read by privileged users. If instead of an X you see an asterix (*) or exclamation mark (!), it means that the password is blank and the user does not need a password to login.
The user ID 0 is reserved for the root user. IDs bigger than 500 can be assigned to users. Below 500 IDs are reserved for the system.
In the following figure you can see the linuxhintuser line including some GECOS information such as full name (Linux Hint) and phone numbers:
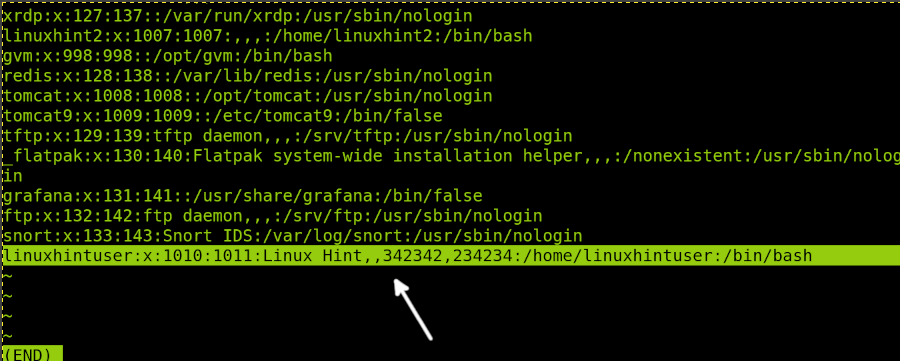
Years ago, passwords were stored in the /etc/passwd file. this was changed. Passwords are now stored in the /etc/shadow file which needs privileges.
The /etc/passwd file is accessible to every user because it holds information users need to interact with the system, for example, to login.
How to edit the /etc/passwd file
The /etc/passwd can be edited using the vipw command. This command is also useful to edit /etc/shadow (When used with the -s flag) and /etc/group files.
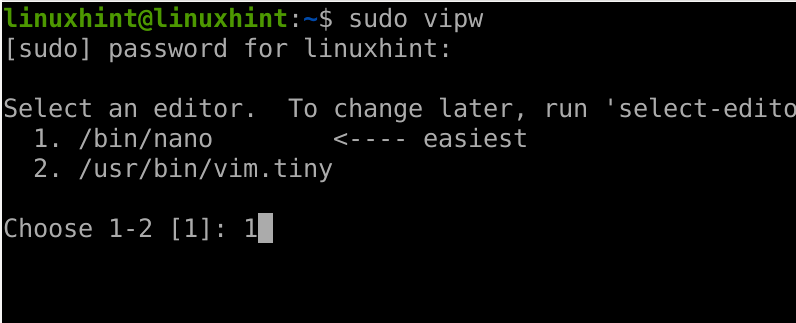
To edit the /etc/passwd file, run the vipw command and when asked, select the text editor of your preference. In my case I’m selecting nano as shown below.
sudo vipw
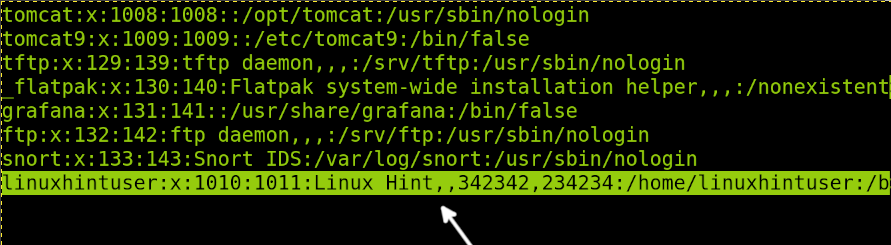
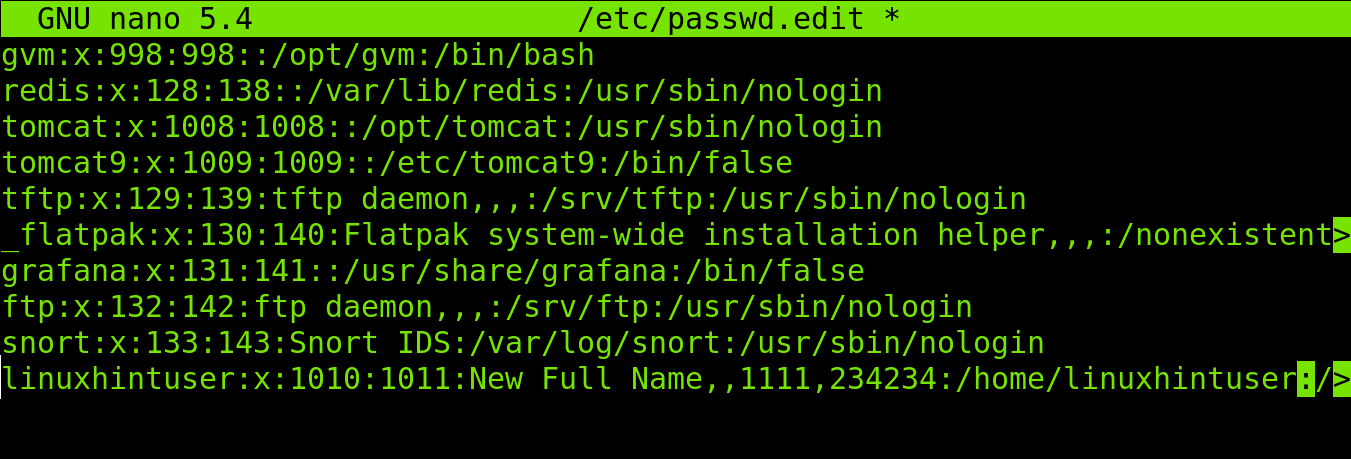
As you can see in the following figure, after running the vipw command, the /etc/passwd file will be opened with a text editor. You can then edit all fields.

In the example below I will edit the linuxhintuser information (Last line). As you can see, the full name is Linux Hint, phone numbers are 342342 and 234234.
As shown in the example below, I edited the full name, replacing the full name (linuxhintuser) with “New Full Name” and editing phone numbers.
Once you are done editing the file, close and save changes.
After closing and saving the file, you will be warned about possible changes you may need to reproduce in the /etc/shadow file. This is not necessary if you don’t edit the password.

You can check the /etc/passwd file using the less or cat commands and you will see changes were properly applied.

Additional functions for the vipw command can be implemented using flags:
- -g: The -g flag is used to edit the /etc/group file containing information about user groups.
- -s: This flag is used to edit both the /etc/shadow and /etc/gshadow files.
- -p: The -p flag is used to edit the passwd database.
- -h: This flag is used to display the help menu.
As you can see in the content above, the /etc/passwd is linked to other files like /etc/shadow and /etc/group, both of which are described below.
The /etc/shadow file
As said previously, formerly Linux/Unix passwords were stored in the /etc/passwd file, which was dangerous since every user has access to it. A user with access to the encrypted password can easily break it by using one of the online databases or through brute force.
To solve this exposure, the /etc/shadow file was implemented to store user encrypted passwords without reading permissions or without super user privileges.
You can see the /etc/shadow file by using cat or less commands as root or with sudo as shown previously.
less /etc/shadow
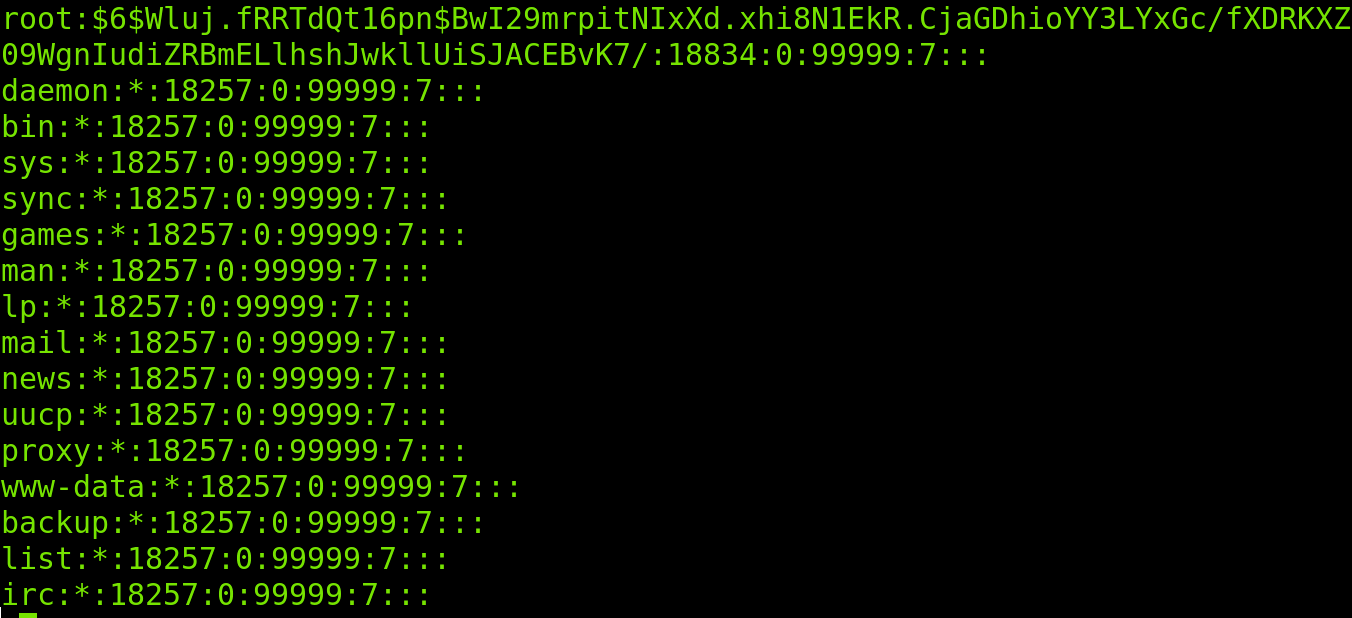
As you can see in the screenshot below, there are 9 columns (Defined by two dots each). Each field contains the first information:
- 1: Username.
- 2: Encrypted password.
- 3: Last password change in days, counting from Jan, 1970.
- 4: Minimum days a user can keep a password before changing it.
- 5: Maximum days a user can keep a password before changing it (If 99999, then no limit)
- 6: In this field the root can define when a user will be requested to change the password.
- 7: This field shows when an account will be inactive after password expiration.
- 8: Password expiration date (Counting from 1 Jan, 1970).
- 9: The last field is reserved without containing useful information.
As you can see, the /etc/shadow file only contains password related information.
To change a password within this file, you need to execute the passwd command followed by the username whose password you want to replace, as shown in the figure below where the linuxhintuser password is updated.
sudo passwd linuxhintuser
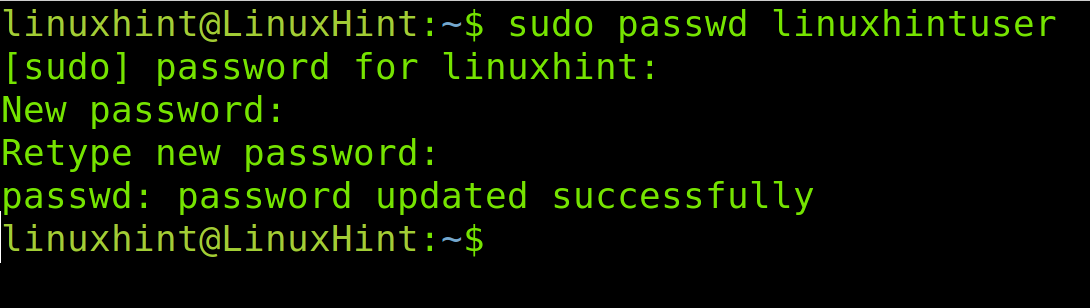
As you can see above, the password was successfully changed.
The /etc/group file
The /etc/group file stores information on groups. This file, like both /etc/passwd and /etc/shadow, also can be edited with the vipw command.
You can read the /etc/group file using the less command as done before.
less /etc/group
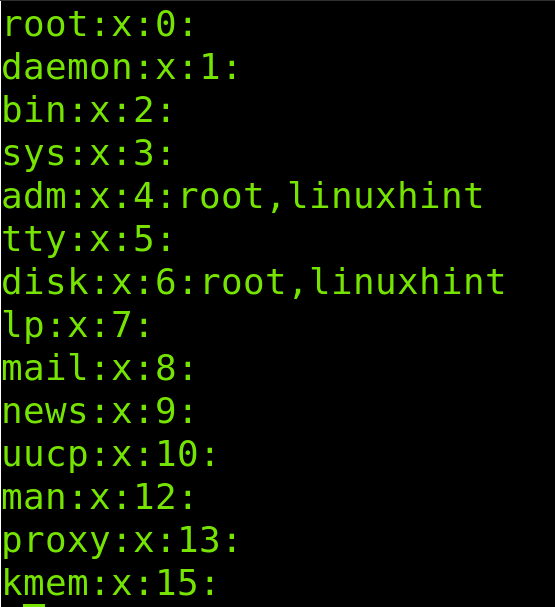
The file looks like the following screenshot, containing 4 columns with group related information, where the first field is group name, the second field is password related, the third is the GID (Group ID) and the fourth shows the group users.
I also would recommend studying the usermode command, some examples are available at https://linuxhint.com/sudo_linux/, also related to user administration. This command is also recommended by the passwd command man page.
