Before performing further actions, we need to obtain general knowledge about the security solutions in place. Remember, it is important to enumerate antivirus and security detection methods on an endpoint in order to stay as undetected as possible and reduce the chance of getting caught.
This task will discuss the common security solution used in corporate networks, divided into Host and Network security solutions.
Host Security Solutions

It is a set of software applications used to monitor and detect abnormal and malicious activities within the host, including:
- Antivirus software
- Microsoft Windows Defender
- Host-based Firewall
- Security Event Logging and Monitoring
- Host-based Intrusion Detection System (HIDS)/ Host-based Intrusion Prevention System (HIPS)
- Endpoint Detection and Response (EDR)
Let’s go more detail through the host-based security solutions that we may encounter during the red team engagement.
Antivirus Software (AV)
Antivirus software also known as anti-malware, is mainly used to monitor, detect, and prevent malicious software from being executed within the host. Most antivirus software applications use well-known features, including Background scanning, Full system scans, Virus definitions. In the background scanning, the antivirus software works in real-time and scans all open and used files in the background. The full system scan is essential when you first install the antivirus. The most interesting part is the virus definitions, where antivirus software replies to the pre-defined virus. That’s why antivirus software needs to update from time to time.
There are various detection techniques that the antivirus uses, including
- Signature-based detection
- Heuristic-based detection
- Behavior-based detection
Signature-based detection is one of the common and traditional techniques used in antivirus software to identify malicious files. Often, researchers or users submit their infected files into an antivirus engine platform for further analysis by AV vendors, and if it confirms as malicious, then the signature gets registered in their database. The antivirus software compares the scanned file with a database of known signatures for possible attacks and malware on the client-side. If we have a match, then it considers a threat.
Heuristic-based detection uses machine learning to decide whether we have the malicious file or not. It scans and statically analyses in real-time in order to find suspicious properties in the application’s code or check whether it uses uncommon Windows or system APIs. It does not rely on the signature-based attack in making the decisions, or sometimes it does. This depends on the implementation of the antivirus software.
Finally, Behavior-based detection relies on monitoring and examining the execution of applications to find abnormal behaviors and uncommon activities, such as creating/updating values in registry keys, killing/creating processes, etc.
As a red teamer, it is essential to be aware of whether antivirus exists or not. It prevents us from doing what we are attempting to do. We can enumerate AV software using Windows built-in tools, such as wmic.
PS C:\Users\thm> wmic /namespace:\\root\securitycenter2 path antivirusproductThis also can be done using PowerShell, which gives the same result.
PS C:\Users\thm> Get-CimInstance -Namespace root/SecurityCenter2 -ClassName AntivirusProduct
displayName : Bitdefender Antivirus
instanceGuid : {BAF124F4-FA00-8560-3FDE-6C380446AEFB}
pathToSignedProductExe : C:\Program Files\Bitdefender\Bitdefender Security\wscfix.exe
pathToSignedReportingExe : C:\Program Files\Bitdefender\Bitdefender Security\bdservicehost.exe
productState : 266240
timestamp : Wed, 15 Dec 2021 12:40:10 GMT
PSComputerName :
displayName : Windows Defender
instanceGuid : {D58FFC3A-813B-4fae-9E44-DA132C9FAA36}
pathToSignedProductExe : windowsdefender://
pathToSignedReportingExe : %ProgramFiles%\Windows Defender\MsMpeng.exe
productState : 393472
timestamp : Fri, 15 Oct 2021 22:32:01 GMT
PSComputerName :As a result, there is a third-party antivirus (Bitdefender Antivirus) and Windows Defender installed on the computer. Note that Windows servers may not have SecurityCenter2 namespace, which may not work on the attached VM. Instead, it works for Windows workstations!
Microsoft Windows Defender
Microsoft Windows Defender is a pre-installed antivirus security tool that runs on endpoints. It uses various algorithms in the detection, including machine learning, big-data analysis, in-depth threat resistance research, and Microsoft cloud infrastructure in protection against malware and viruses. MS Defender works in three protection modes: Active, Passive, Disable modes.
Active mode is used where the MS Defender runs as the primary antivirus software on the machine where provides protection and remediation. Passive mode is run when a 3rd party antivirus software is installed. Therefore, it works as secondary antivirus software where it scans files and detects threats but does not provide remediation. Finally, Disable mode is when the MS Defender is disabled or uninstalled from the system.
We can use the following PowerShell command to check the service state of Windows Defender:
PS C:\Users\thm> Get-Service WinDefend
Status Name DisplayName
------ ---- -----------
Running WinDefend Windows Defender Antivirus ServiceNext, we can start using the Get-MpComputerStatus cmdlet to get the current Windows Defender status. However, it provides the current status of security solution elements, including Anti-Spyware, Antivirus, LoavProtection, Real-time protection, etc. We can use select to specify what we need for as follows,
PS C:\Users\thm> Get-MpComputerStatus | select RealTimeProtectionEnabled
RealTimeProtectionEnabled
-------------------------
FalseAs a result, MpComputerStatus highlights whether Windows Defender is enabled or not.
Host-based Firewall
It is a security tool installed and run on a host machine that can prevent and block attacker or red teamers’ attack attempts. Thus, it is essential to enumerate and gather details about the firewall and its rules within the machine we have initial access to.

The main purpose of the host-based firewall is to control the inbound and outbound traffic that goes through the device’s interface. It protects the host from untrusted devices that are on the same network. A modern host-based firewall uses multiple levels of analyzing traffic, including packet analysis, while establishing the connection.
A firewall acts as control access at the network layer. It is capable of allowing and denying network packets. For example, a firewall can be configured to block ICMP packets sent through the ping command from other machines in the same network. Next-generation firewalls also can inspect other OSI layers, such as application layers. Therefore, it can detect and block SQL injection and other application-layer attacks.
PS C:\Users\thm> Get-NetFirewallProfile | Format-Table Name, Enabled
Name Enabled
---- -------
Domain True
Private True
Public TrueIf we have admin privileges on the current user we logged in with, then we try to disable one or more than one firewall profile using the Set-NetFirewallProfile cmdlet.
PS C:\Windows\system32> Set-NetFirewallProfile -Profile Domain, Public, Private -Enabled False
PS C:\Windows\system32> Get-NetFirewallProfile | Format-Table Name, Enabled
---- -------
Domain False
Private False
Public FalseWe can also learn and check the current Firewall rules, whether allowing or denying by the firewall.
PS C:\Users\thm> Get-NetFirewallRule | select DisplayName, Enabled, Description
DisplayName Enabled
----------- -------
Virtual Machine Monitoring (DCOM-In) False
Virtual Machine Monitoring (Echo Request - ICMPv4-In) False
Virtual Machine Monitoring (Echo Request - ICMPv6-In) False
Virtual Machine Monitoring (NB-Session-In) False
Virtual Machine Monitoring (RPC) False
SNMP Trap Service (UDP In) False
SNMP Trap Service (UDP In) False
Connected User Experiences and Telemetry True
Delivery Optimization (TCP-In) TrueDuring the red team engagement, we have no clue what the firewall blocks. However, we can take advantage of some PowerShell cmdlets such as Test-NetConnection and TcpClient. Assume we know that a firewall is in place, and we need to test inbound connection without extra tools, then we can do the following:
PS C:\Users\thm> Test-NetConnection -ComputerName 127.0.0.1 -Port 80
ComputerName : 127.0.0.1
RemoteAddress : 127.0.0.1
RemotePort : 80
InterfaceAlias : Loopback Pseudo-Interface 1
SourceAddress : 127.0.0.1
TcpTestSucceeded : True
PS C:\Users\thm> (New-Object System.Net.Sockets.TcpClient("127.0.0.1", "80")).Connected
TrueAs a result, we can confirm the inbound connection on port 80 is open and allowed in the firewall. Note that we can also test for remote targets in the same network or domain names by specifying in the -ComputerName argument for the Test-NetConnection.
NOTE: Host Intrusion Detection System (HIDS) analyzes system state, system calls, file-system modifications, application logs, and other system activity.
NOTE: Endpoint detection and response (EDR) is a series of tools that monitor devices for activity that could indicate a threat.
Security Event Logging and Monitoring
By default, Operating systems log various activity events in the system using log files. The event logging feature is available to the IT system and network administrators to monitor and analyze important events, whether on the host or the network side. In cooperating networks, security teams utilize the logging event technique to track and investigate security incidents.
There are various categories where the Windows operating system logs event information, including the application, system, security, services, etc. In addition, security and network devices store event information into log files to allow the system administrators to get an insight into what is going on.
We can get a list of available event logs on the local machine using the Get-EventLog cmdlet.
PS C:\Users\thm> Get-EventLog -List
Max(K) Retain OverflowAction Entries Log
------ ------ -------------- ------- ---
512 7 OverwriteOlder 59 Active Directory Web Services
20,480 0 OverwriteAsNeeded 512 Application
512 0 OverwriteAsNeeded 170 Directory Service
102,400 0 OverwriteAsNeeded 67 DNS Server
20,480 0 OverwriteAsNeeded 4,345 System
15,360 0 OverwriteAsNeeded 1,692 Windows PowerShellSometimes, the list of available event logs gives you an insight into what applications and services are installed on the machine! For example, we can see that the local machine has Active Directory, DNS server, etc. For more information about the Get-EventLog cmdlet with examples, visit the Microsoft documents website.
In corporate networks, log agent software is installed on clients to collect and gather logs from different sensors to analyze and monitor activities within the network. We will discuss them more in the Network Security Solution task.
System Monitor (Sysmon)

Windows System Monitor sysmon is a service and device driver. It is one of the Microsoft Sysinternals suites. The sysmon tool is not an essential tool (not installed by default), but it starts gathering and logging events once installed. These logs indicators can significantly help system administrators and blue teamers to track and investigate malicious activity and help with general troubleshooting.
One of the great features of the sysmon tool is that it can log many important events, and you can also create your own rule(s) and configuration to monitor:
- Process creation and termination
- Network connections
- Modification on file
- Remote threats
- Process and memory access
- and many others
For learning more about sysmon, visit the Windows document page here.
As a red teamer, one of the primary goals is to stay undetectable, so it is essential to be aware of these tools and avoid causing generating and alerting events. The following are some of the tricks that can be used to detect whether the sysmon is available in the victim machine or not.
We can look for a process or service that has been named “Sysmon” within the current process or services as follows,
PS C:\Users\thm> Get-Process | Where-Object { $_.ProcessName -eq "Sysmon" }
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
373 15 20212 31716 3316 0 Sysmonor look for services as follows,
PS C:\Users\thm> Get-CimInstance win32_service -Filter "Description = 'System Monitor service'"
# or
Get-Service | where-object {$_.DisplayName -like "*sysm*"}It also can be done by checking the Windows registry
PS C:\Users\thm> reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows-Sysmon/OperationalAll these commands confirm if the sysmon tool is installed. Once we detect it, we can try to find the sysmon configuration file if we have readable permission to understand what system administrators are monitoring.
PS C:\Users\thm> findstr /si '<ProcessCreate onmatch="exclude">' C:\tools\*
C:\tools\Sysmon\sysmonconfig.xml:
C:\tools\Sysmon\sysmonconfig.xml: For more detail about the Windows sysmon tool and how to utilize it within endpoints, we suggest trying the TryHackMe room: Sysmon.
Host-based Intrusion Detection/Prevention System (HIDS/HIPS)
HIDS stands for Host-based Intrusion Detection System. It is software that has the ability to monitor and detect abnormal and malicious activities in a host. The primary purpose of HIDS is to detect suspicious activities and not to prevent them. There are two methods that the host-based or network intrusion detection system works, including:
- Signature-based IDS - it looks at checksums and message authentication.
- Anomaly-based IDS looks for unexpected activities, including abnormal bandwidth usage, protocols, and ports.
Host-based Intrusion Prevention Systems (HIPS) works by securing the operating system activities which where is installed. It is a detecting and prevention solution against well-known attacks and abnormal behaviors. HIPS is capable of auditing log files of the host, monitoring processes, and protecting system resources. HIPS is a mixture of best product features such as antivirus, behavior analysis, network, application firewall, etc.
There is also a network-based IDS/IPS, which we will be covering in the next task.
Endpoint Detection and Response (EDR)
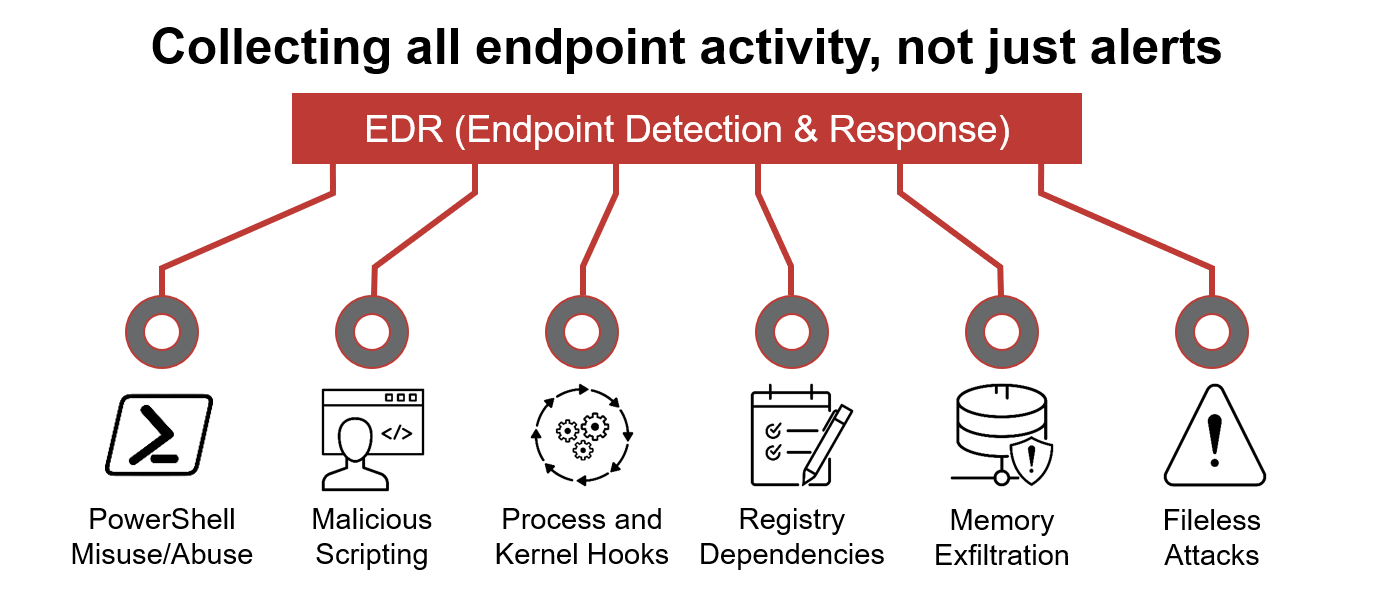
It is also known as Endpoint Detection and Threat Response (EDTR). The EDR is a cybersecurity solution that defends against malware and other threats. EDRs can look for malicious files, monitor endpoint, system, and network events, and record them in a database for further analysis, detection, and investigation. EDRs are the next generation of antivirus and detect malicious activities on the host in real-time.
EDR analyze system data and behavior for making section threats, including
- Malware, including viruses, trojans, adware, keyloggers
- Exploit chains
- Ransomware
Below are some common EDR software for endpoints
- Cylance
- Crowdstrike
- Symantec
- SentinelOne
- Many others
Even though an attacker successfully delivered their payload and bypassed EDR in receiving reverse shell, EDR is still running and monitors the system. It may block us from doing something else if it flags an alert.
We can use scripts for enumerating security products within the machine, such as Invoke-EDRChecker and SharpEDRChecker. They check for commonly used Antivirus, EDR, logging monitor products by checking file metadata, processes, DLL loaded into current processes, Services, and drivers, directories.
