Credits to Yago Jesús and Aroki cyber securityspeech in RootedCON 2025
Post Pwn!
Once the system is compromised, now what?
- Keep privileges
- Without trace
- Without being seen
- Ptrace() injections
- Rootkits
- C2C
Previously used
Userland R00tkits (2010 / ?)
- Easy to develop
- Stable
- Relatively obvious
- ld.so.preload
Where do they operate?

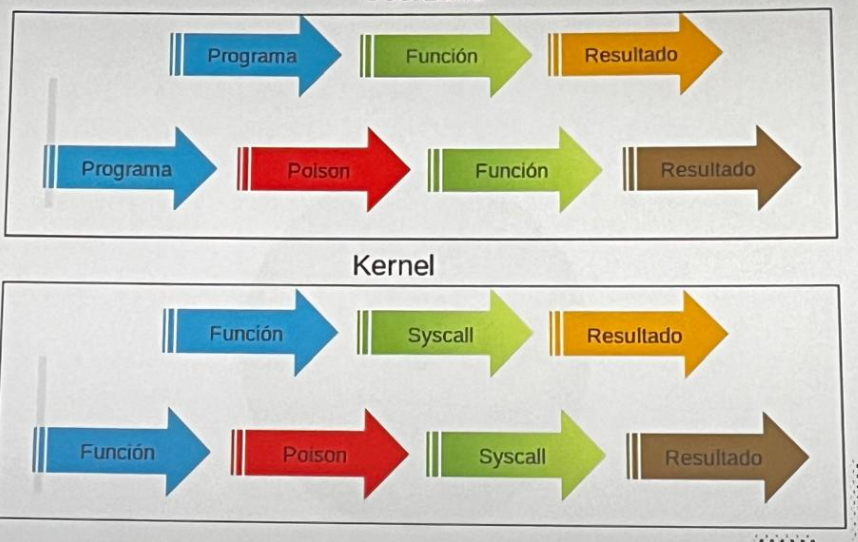
X startup
- Useful for devices with X
/home/<user>/.config/autostart- Useful for “The year of Linux on the desktop”
TODO()
