In this note, we will learn more about users and groups, especially within the Active Directory. Gathering information about the compromised machine is essential that could be used in the next stage. Account discovery is the first step once we have gained initial access to the compromised machine to understand what we have and what other accounts are in the system.

An Active Directory environment contains various accounts with the necessary permissions, access, and roles for different purposes. Common Active Directory service accounts include built-in local user accounts, domain user accounts, managed service accounts, and virtual accounts.
- The built-in local users’ accounts are used to manage the system locally, which is not part of the AD environment.
- Domain user accounts with access to an active directory environment can use the AD services (managed by AD).
- AD managed service accounts are limited domain user account with higher privileges to manage AD services.
- Domain Administrators are user accounts that can manage information in an Active Directory environment, including AD configurations, users, groups, permissions, roles, services, etc. One of the red team goals in engagement is to hunt for information that leads to a domain administrator having complete control over the AD environment.
The following are Active Directory Administrators accounts:
| BUILTIN\Administrator | Local admin access on a domain controller |
|---|---|
| Domain Admins | Administrative access to all resources in the domain |
| Enterprise Admins | Available only in the forest root |
| Schema Admins | Capable of modifying domain/forest; useful for red teamers |
| Server Operators | Can manage domain servers |
| Account Operators | Can manage users that are not in privileged groups |
Now that we learn about various account types within the AD environment. Let’s enumerate the Windows machine that we have access to during the initial access stage. As a current user, we have specific permissions to view or manage things within the machine and the AD environment.
Active Directory (AD) Enum
Now, enumerating in the AD environment requires different tools and techniques. Once we confirm that the machine is part of the AD environment, we can start hunting for any variable info that may be used later. In this stage, we are using PowerShell to enumerate for users and groups.
The following PowerShell command is to get all active directory user accounts. Note that we need to use -Filter argument.
PS C:\Users\thm> Get-ADUser -Filter *
DistinguishedName : CN=Administrator,CN=Users,DC=thmredteam,DC=com
Enabled : True
GivenName :
Name : Administrator
ObjectClass : user
ObjectGUID : 4094d220-fb71-4de1-b5b2-ba18f6583c65
SamAccountName : Administrator
SID : S-1-5-21-1966530601-3185510712-10604624-500
Surname :
UserPrincipalName :
PS C:\Users\thm>We can also use the LDAP hierarchical tree structure to find a user within the AD environment. The Distinguished Name (DN) is a collection of comma-separated key and value pairs used to identify unique records within the directory. The DN consists of Domain Component (DC), OrganizationalUnitName (OU), Common Name (CN), and others. The following “CN=User1,CN=Users,DC=thmredteam,DC=com” is an example of DN, which can be visualized as follow:
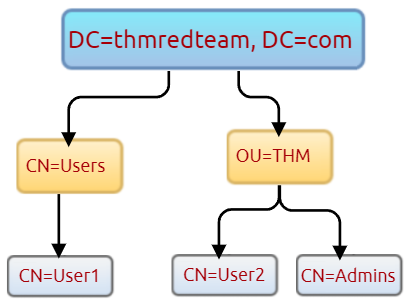
Using the SearchBase option, we specify a specific Common-Name CN in the active directory. For example, we can specify to list any user(s) that part of Users.
PS C:\Users\thm> Get-ADUser -Filter * -SearchBase "CN=Users,DC=THMREDTEAM,DC=COM"
DistinguishedName : CN=Administrator,CN=Users,DC=thmredteam,DC=com
Enabled : True
GivenName :
Name : Administrator
ObjectClass : user
ObjectGUID : 4094d220-fb71-4de1-b5b2-ba18f6583c65
SamAccountName : Administrator
SID : S-1-5-21-1966530601-3185510712-10604624-500
Surname :
UserPrincipalName :Note that the result may contain more than one user depending on the configuration of the CN.
NOTE: In Windows domains, Organizational Unit (OU) refers to containers that hold users, groups and computers to which similar policies should apply. In most cases, OUs will match departments in an enterprise.
