Investigate image metadata
- Use command
file image.png - Use command
exiftool image.png - Use command
xxd image.png - Use command
strings image.png - Use tool binwalk to search binary images for embedded files and executable code:
binwalk image.png- To extract the file:
binwalk -e image.png
- To extract the file:
- Use command:
steghide extract -sf image.png - Steganographic Decoder
- Upload the file to it
- Bruteforce the password and extract contents of an image:
stegseek -sf image.png /path/to/wordlist
# Then if it extracts something do
file whatever.file # to know what is it-
Use command
steghide info image.png -
Inspect audio files (like
.wavfiles) with Sonic Visualizer- Click on
Layer > Add Spectrogram
- Click on
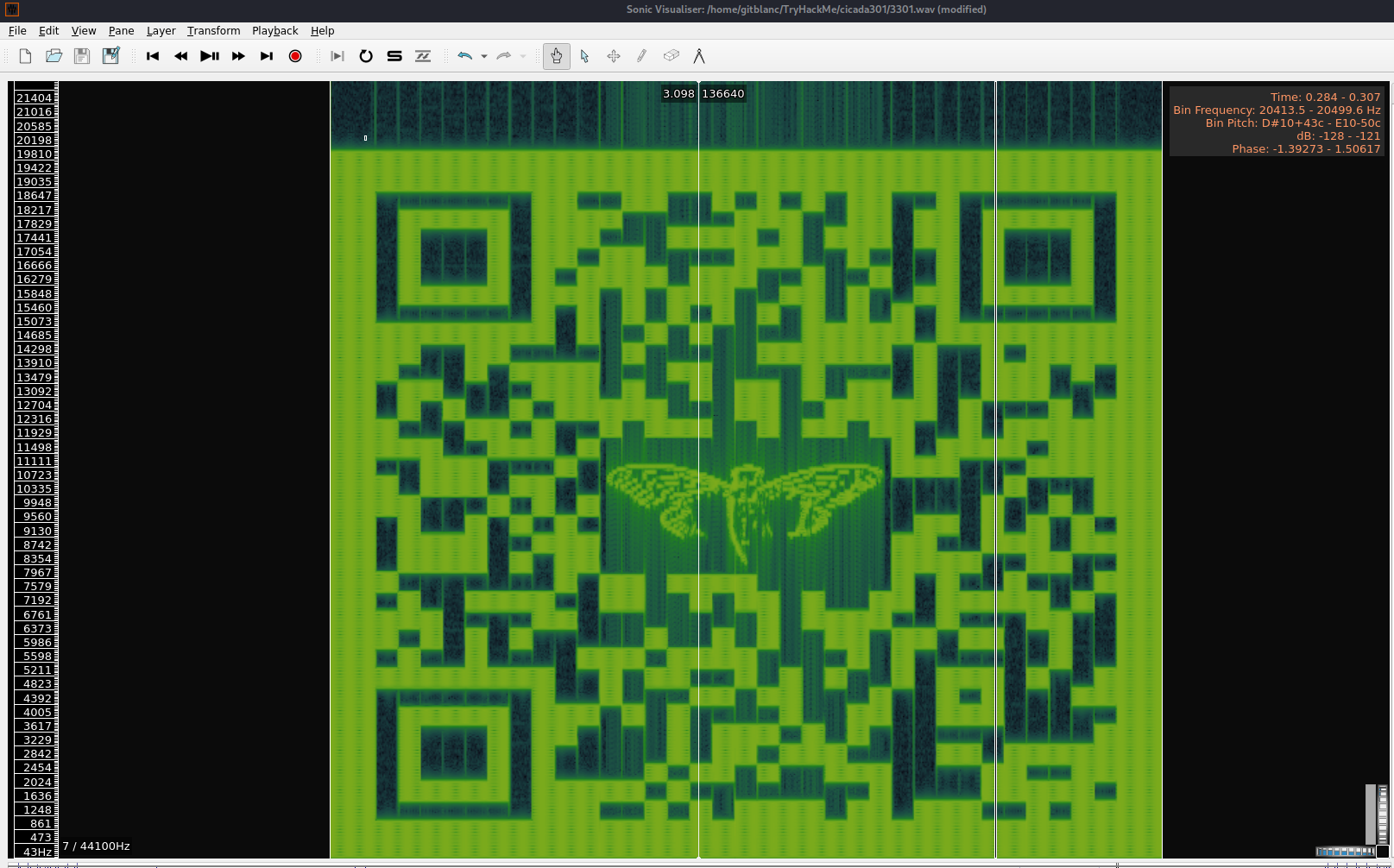
- Now set the scale to dB^2 and the colour to White on Black
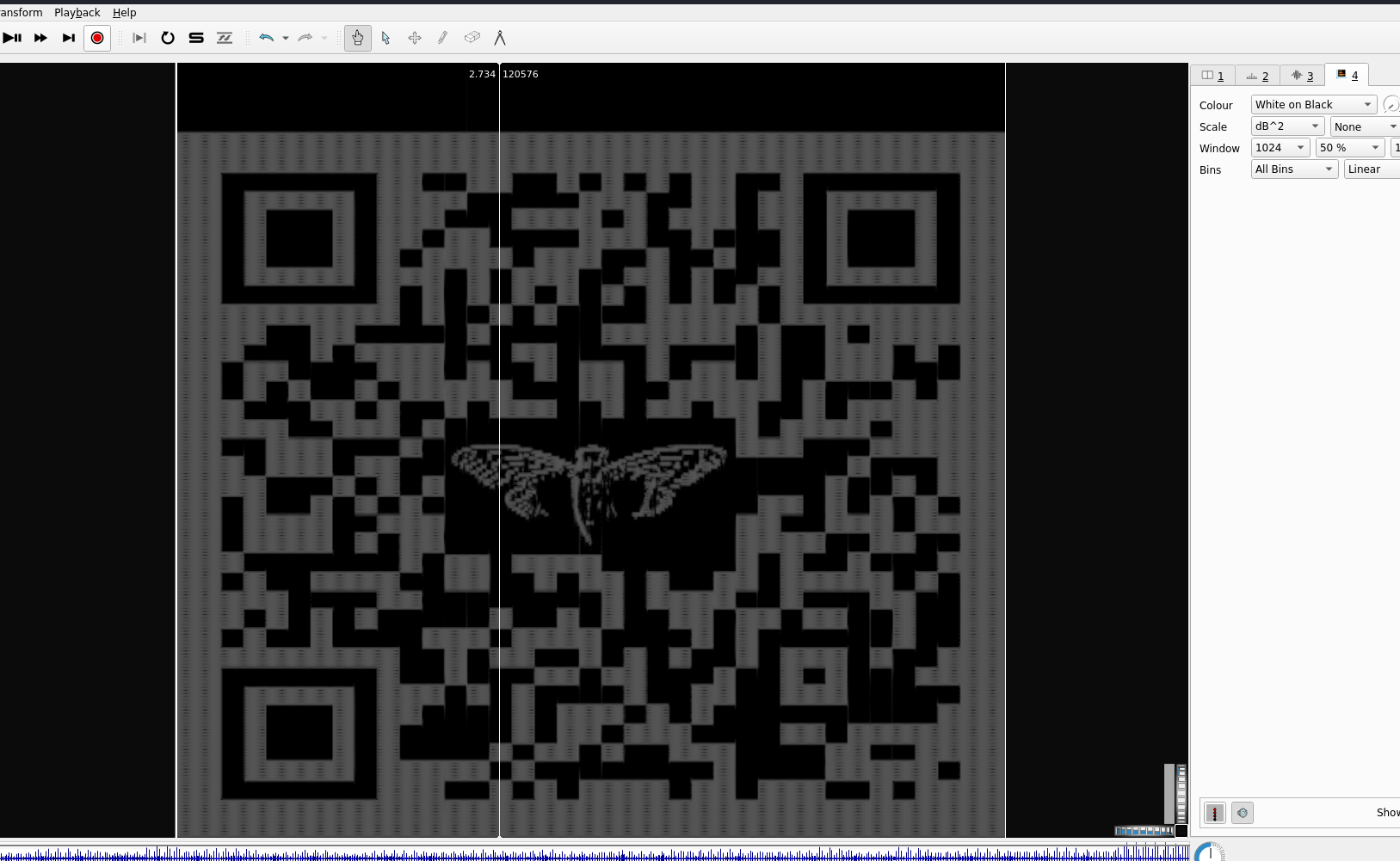
-
Try with the tool outguess when you have an image
- Also there is this other project (manteined) outguess
- Then, install it with:
./configure && make - Then, try the command:
./outguess -r /file/to/analyze /path/to/the/output
-
If you find a corrupted image (checking the file header of the image which should be
\x89x50\x4Ex47), the try this command:
printf '\x89\x50\x4E\x47' | dd of=IMAGE.png bs=4 conv=notrunc
printf '\xff\xd8\xff\xe0' | dd of=IMAGE.jpg bs=4 conv=notrunc- If you have two strings in different formats, try this python script:
s1 = "44585d6b2368737c65252166234f20626d"
s2 = "1010101010101010101010101010101010"
h = hex(int(s1, 16) ^ int(s2, 16))[2:]
print(bytes.fromhex(h).decode('utf-8'))- You also have the tool stegsolve
- Install with:
wget http://www.caesum.com/handbook/Stegsolve.jar -O stegsolve.jar
chmod +x stegsolve.jar
mkdir bin
mv stegsolve.jar bin/-
Use it with:
java -jar stegsolve.jar -
You might also need to search for a web in WaybackMachine
-
Open
.pcapfiles with wireshark and analyze them -
If you find a morse code on a
.wav, try the tool morsecode decoder -
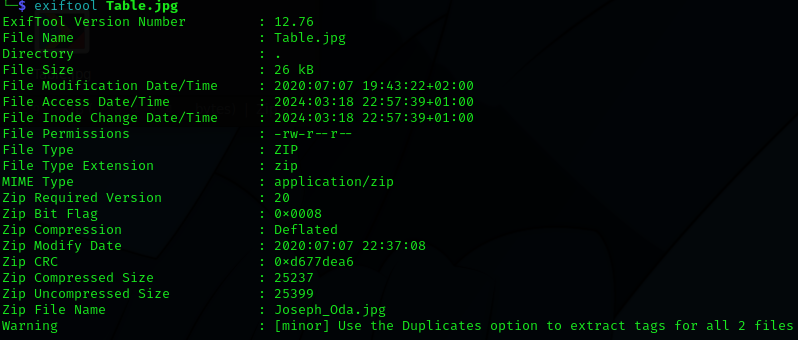
If you find an image and running
exiftool image.jpgyou find some zip: