- Firstly, if you run
ss -tulwnand you find rare ports open like:
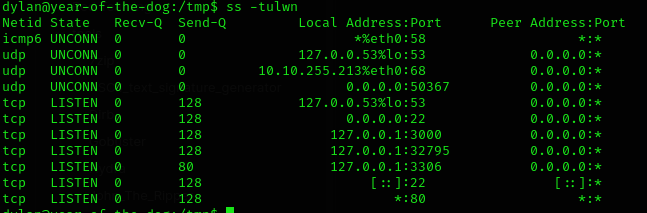
-
Note the port
3000 -
- To use the binary on the machine, just upload to it by a python server and do a
chmod +x socat.bin
- To use the binary on the machine, just upload to it by a python server and do a
-
Use it with:
# Forward our traffic from port 8080 to port 3000
/tmp/socat tcp-l:8080,fork,reuseaddr tcp:127.0.0.1:3000 &- Now navigate to the newly opened port in the attackers machine
