Before you learn what phishing is, you’ll need to understand the term social engineering. Social engineering is the psychological manipulation of people into performing or divulging information by exploiting weaknesses in human nature. These “weaknesses” can be curiosity, jealously, greed and even kindness and the willingness to help someone. Phishing is a source of social engineering delivered through email to trick someone into either revealing personal information, credentials or even executing malicious code on their computer.
These emails will usually appear to come from a trusted source, whether that’s a person or a business. They include content that tries to tempt or trick people into downloading software, opening attachments, or following links to a bogus website.
A term you’ll come across and the type of phishing campaign a red team would participate in is spear-phishing, as with throwing a physical spear; you’d have a target to aim at, the same can be said with spear-phishing in that you’re targeting an individual, business or organisation rather than just anybody as mass. This is an effective form of phishing for a red team engagement as they are bespoke to the target it makes them hard to detect by technology such as spam filters, antivirus and firewalls.
A red team could be contracted to solely carry out a phishing assessment to see whether a business is vulnerable to this type of attack or can also be part of a broader scale assessment and used to gain access to computer systems or services.
Some other methods of phishing through other mediums are smishing which is phishing through SMS messages, and vishing which is performed through phone calls.
Example Scenario:
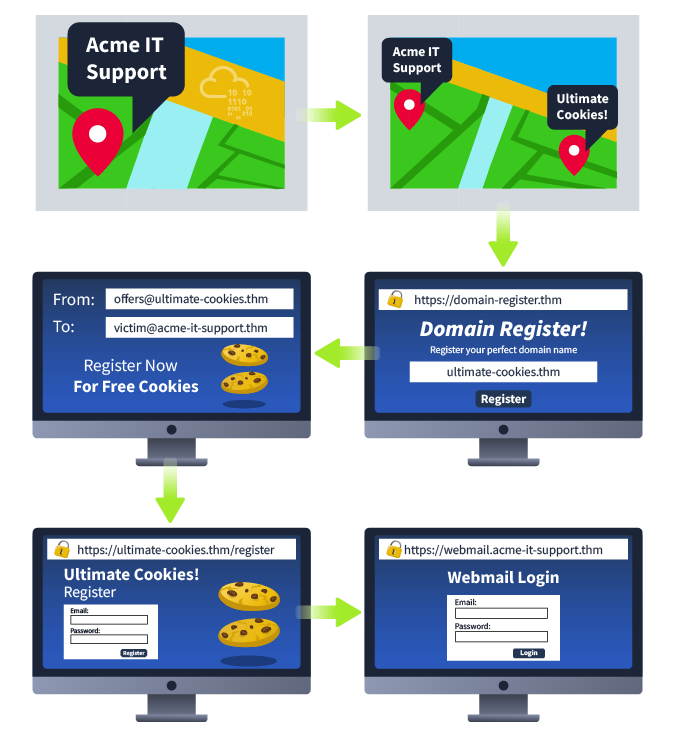
The below example scenario shows how an employee of a company could be tricked into revealing their credentials.
- The attacker locates the physical location of the target business.
- The attacker then looks for nearby food suppliers and discovers a company called Ultimate Cookies!
- The Attacker registers the domain name ultimate-cookies.thm
- The attacker then crafts an email to their target, tempting them with an offer of receiving some free cookies if they sign up to the website. Because the victim has heard of this local company, they are more likely to trust it.
- The victim then follows the link in the email to the fake website created by the attacker and registers online. To keep things simple, the victim reuses the same password for all their online accounts.
- The attacker now has the victim’s email address and password and can log onto the victim’s company email account. The attacker could now have access to private company information and also have somewhere to launch another phishing attack against other employees.
Next, you’ll learn what goes on in setting up the infrastructure for a red team phishing campaign.
