-
Sometimes you can find that a process is consuming to much or maybe analyzing the processes running you see something anomaly
- For the command of displaying linux services and running processes visit Some Linux cheatsheet commands 👾
-
Once you find the suspicious process or service, you can download the files associated to it and analyze them on VirusTotal
-
If you discover a miner, try to search the file where the malware is being executed and then you could find out the wallet address and more.
- You might find the wallet addres encoded like:
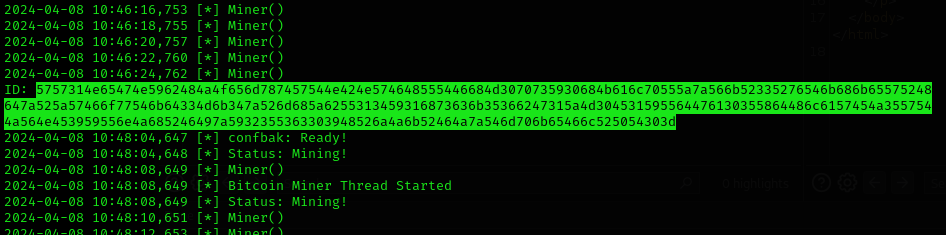
- So you must decode it on CyberChef for example
- Otherwise, checkout Translation and Shifting (Format encoding) 🥭
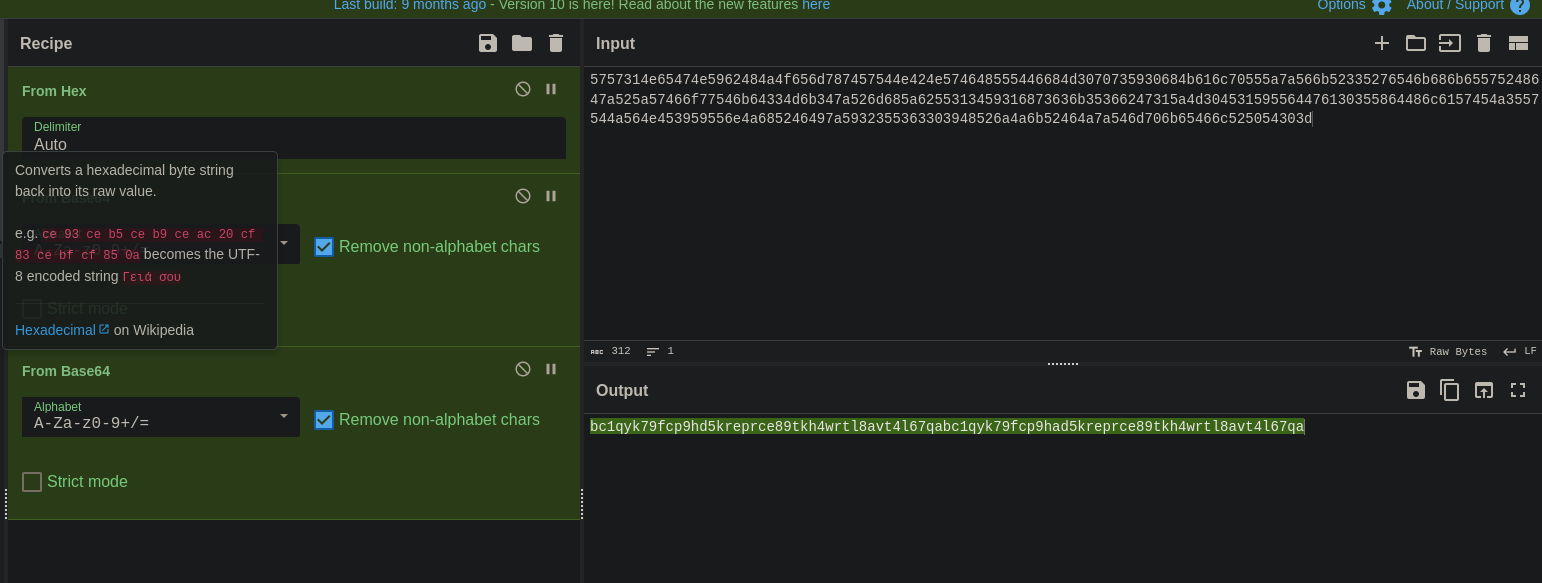
-
Rember that it can be obfuscated, so you might separate the base64 decoded identifier like:
-
bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qabc1qyk79fcp9had5kreprce89tkh4wrtl8avt4l67qa→bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qabc1qyk79fcp9had5kreprce89tkh4wrtl8avt4l67qa
-
Then you can search it in Blockchain Explorer
